

|
|
 |
7.6 Remote Access
Description
Remote access enables a user to log on from a local computer to a remote computer network and use its resources as if a direct LAN link existed. The services used here are known as Remote Access Service (RAS). RAS ensures that remote users can access the network resources.
In general, RAS is used in the following situations:
RAS offers a simple solution in such scenarios: the remote user establishes a connection with the corporate network e.g. over the telephone network using a modem. This direct connection can exist for as long as is necessary and can be viewed as a leased line which is only active on demand.
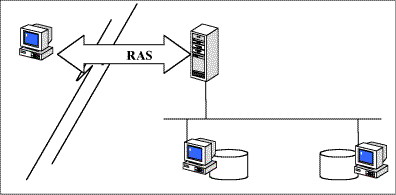
Figure: Remote Access to Resources
Establishment of a RAS connection generally requires three components as follows:
RAS is implemented as a client/server architecture: the RAS client can be configured so that it automatically establishes the RAS connection when corporate network resources are required by dialling the phone number of the computer on which the RAS server software is installed. Alternatively, the RAS connection can be initiated manually by the user. Some operating systems, e.g. Windows NT, also allow the RAS to be activated immediately following system logon.
There are two basic ways of establishing a connection to the remote LAN (see Safeguard Selection of a suitable RAS system architecture):
From the point of view of security, the following security objectives apply to RAS access:
Threat Scenario
The client/server architecture of RAS systems means that both the RAS client and the RAS server are exposed to specific risks due to the type of operational environment and the manner of use.
At this point we advise against considering the dangers to the client and server completely separately since, for example, if a RAS client were to be compromised, the RAS server would automatically be endangered. Moreover it should be borne in mind that, for example in the Windows environment, every RAS client can also be operated as a RAS server, so that the threats which apply to RAS servers apply equally to a RAS client.
The following typical threats are assumed for the IT baseline protection of a RAS system:
Force Majeure
Organisational Shortcomings
Human Error
Technical Failure
Deliberate Acts
Recommended Countermeasures (S)
To implement IT baseline protection, selection of the required packages of safeguards ("modules"), as described in Sections 2.3 and 2.4, is recommended.
A RAS system consists of several components which from the outset should be protected as individual components. Quite apart from the RAS functionality, these should be viewed as normal IT systems or network switching elements which need to be protected according to the suggestions made in the relevant safeguard modules. RAS servers are computers which are normally fully under the control of an organisation and perform the important task of controlling access to the internal network. The RAS functionality is generally superimposed on an operating system which in most cases offers additional services as well. Hence the security of RAS access also depends on there being no security weaknesses either at operating system or service level.
As well as protecting the RAS system components, however, it is also necessary to draw up a RAS security policy which must be integrated into the existing security policy. At the same time as implementing existing security requirements, the RAS system requires that new, RAS-specific security rules are defined.
A RAS system will generally be used in the environment of other systems which serve to control access to the internal network from outside. Examples of other systems with which a RAS system has to work are firewall systems and remote maintenance systems. For this reason, when implementing the RAS-specific safeguards, the safeguards from the relevant modules of the affected systems must also be considered. The modules which should be considered include:
Secure RAS access depends on a series of safeguards being taken, starting at the design stage, and then moving on to procurement and operation. The steps involved here and the safeguards which should be considered at each of the steps are listed below.
| 1. | A RAS concept must be prepared up front, based on the security requirements for the existing IT systems and the requirements arising from the planned situations under which RAS will be used. |
| 1.1 | To tailor the concept to the particular application, the requirements must be determined at the start. For this purpose a requirements analysis must be performed (see Performing a RAS requirements analysis). |
| 1.2 | On the basis of the requirements thus determined, a RAS concept can then be defined (see Development of a RAS concept). |
| 1.3 | To implement the concept, a RAS system architecture must be defined (see Selection of a suitable RAS system architecture), which is tailored to the organisation's RAS requirements and the RAS concept to be implemented. |
| 2. | Before the RAS system can be procured, the requirements relating to the RAS product must be derived from the RAS concept and the choice of a suitable RAS product must be based on these (see Selection of a suitable RAS product). |
| 3. | The security-relevant safeguards for the implementation of the RAS concept may be broken down into the following areas: |
| 3.1 | definition of security guidelines for use of RAS (see Definition of a set of RAS security guidelines), |
| 3.2 | installation and initial configuration (see Secure installation of the RAS system and Secure configuration of the RAS system), and |
| 3.3 | the ongoing operation of the RAS system (see Secure operation of the RAS system). |
| Typically, RAS servers and RAS clients must always be considered with RAS systems. As the users of a RAS system essentially contribute to its secure operation, they must be prepared for the use of RAS access and be instructed in the use of the RAS software. Here in particular their attention must be drawn to the dangers which exist when RAS access is used from home or on the road (see Training before actual use of a program and Education on IT security measures). | |
| Tunnel protocols are often used as a means of protecting RAS connections. These allow the establishment, building on an existing connection, of a communication channel between IT systems or networks which is sealed off through access control and encryption. Because this channel is sealed off from the outside world the term Virtual Private Network (VPN) is frequently employed (see Use of suitable tunnel protocols for RAS communication). |
The safeguards package for the "Remote Access" module is presented below.
Infrastructure
Organisation
Personnel
Hardware and software
Communication
Contingency Planning
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
last update: October 2000 |