

|
|
| Previous | Table of Contents | Next |
Ports are the ends points of a communication link between applications running on different systems. Port address filtering can be used to block actions related to a particular application. Hackers often use specific applications to gain information about your internal network or to gain access to systems. You can block the use of these applications by blocking the ports that they run on. The usual technique for Windows NT is to block all ports except the selected ports you want to use. For web servers, it is appropriate to block all ports except port 80, which is the port that HTTP uses. If only port 80 is enabled, then only HTTP traffic will be able to get through to a server. All packets requesting services on other ports are discarded.
Blocking all but specific ports makes port filtering easy to configure and provides high levels of security. Hackers can only attempt to subvert a system using the few applications that are allowed on the system. A web server running Windows NT and the Microsoft Internet Information Server is relatively easy to secure.
Many routers provide port filtering in addition to packet filtering. The advantage of filtering ports on a router is that any system on the internal side of the router can benefit from the filtering. As shown in figure 12.7, three servers are connected to the Internet. The router in this case performs filtering for all the servers.
Alternatively, you can use Windows NT’s built-in port filtering to set port filtering options at each of the individual servers. The dialog box for enabling and disabling ports is pictured in figure 12.10. Note that Permit Only is enabled in each column and only TCP port 80 has been enabled.
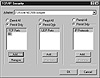
Figure 12.10 The TCP/IP dialog box is where you can enable or disable the ports that Windows NT will listen to.
One note of caution. Windows NT’s port filtering options are rather rudimentary. Microsoft even admits in its documentation that “NT’s port filtering shouldn’t be considered an adequate replacement for a dedicated router or a complete firewall setup.” Still, when configured on a stand-alone system, these options can provide a level of protection against hackers.
Warning: You should consider any web server as an expendable system that might come under hacker attack. Always be prepared to restore the system from backup at any time.
Setting ports on the Microsoft Proxy Server requires a little more involvement. In order to allow applications to work through the server, you’ll need to determine exactly which ports are required and enable them. Some applications require multiple ports. For example, Microsoft Proxy Server supports the VDOLive application, which uses outbound TCP port 7000 and inbound UDP port 0. Setting proxy server ports uses a different interface than the one pictured in figure 12.10.
Microsoft Internet Information Server (IIS) is a web server for publishing information on the Internet or on internal TCP/IP networks (intranets). Like all web servers, it uses the HyperText Transfer Protocol (HTTP) and also supports File Transfer Protocol (FTP) services. Web servers accept requests from web browsers and respond by sending web pages back to the browser. Web pages are created by using HyperText Markup Language (HTML).
IIS can be used to provide both static and dynamic content to users. Static content includes predefined pages that are sent with the same contents to all users that request them. Dynamic pages are created on the spot by the web server based on requests made by the user. Information to create the page may come from database servers and other information servers, or from connected equipment such as cameras and microphones. For example, a web server might be connected to a camera that points at a major city intersection. Users can view the site before going to lunch to see what the latest traffic conditions are like; this is real-time dynamic information.
IIS supports a number of interfaces for creating dynamic pages, including CGI (Common Gateway Interface), ISAPI (Internet Server API), and the Internet Database Connector. CGI is the standard forms-based method that enables users to interact with web servers. ISAPI is a Microsoft interface that provides a much more enhanced interface than CGI. The Internet Database Connector enables the IIS to connect with back-end database systems and query those systems.
IIS also provides virtual server capabilities, in which a single server hosts several different domains. For example, a company in several different and unrelated businesses can obtain a domain name and IP address for each, then host both on the same server.
IIS integrates with Windows NT security, enabling you to take advantage of existing user accounts, groups, rights, and permissions built into Windows NT. This is ideal for intranet environments or for supporting mobile and remote users.
For example, you can provide subscription services, which are essentially pay-for-view web sites. Once a user pays their subscription, you create an account and grant the account permissions in special pay-for-view directories. Many financial sites on the web do this. You can go to the home page and view the latest financial news, but if you want analysis or additional information, you must have an account that enables you to access directories where pay-for-view information is located.
With IIS, you use the Windows NT directory structure to control access to information. Normally, most users access the server via a special anonymous user account. The server will pop up a logon dialog box and ask the user to supply a user name and password if users try to access a restricted directory. Upon successful logon to the account, the user then access the server using his account rather than the anonymous user account.
The anonymous user account is called IUSR_computername, where computername is the name of the server. Everyone that accesses the web site initially uses this account.
| Previous | Table of Contents | Next |