

|
|
| Previous | Table of Contents | Next |
As just mentioned, IIS uses the Windows NT security model extensively to help you protect the system from hackers and viruses, and to ensure that legitimate users only access information they are allowed to access. The Windows NT File System provides most of this security but NTFS, not FAT must be in use. The web server has its own set of directory permissions that apply to any user that accesses the directories through web services (that is, by accessing the server using the HTTP protocol). These permissions include Read-only, Execute-only, and Write. The home directory for the web server has the Read-only permission.
You can also enable session encryption between client and server by using SSL (Secure Sockets Layer) version 2.0 and 3.0. Some additional security features are discussed in the following sections as outlined in the following list:
The Anonymous User Account
The IUSR_computername account is automatically created when you install IIS. When web users access the web server, they do so under the guise of this account. Multiple users can access the server using this account at the same time.
The IUSR_computername account is like any other Windows NT user account. Administrators can change the permissions that the account has in any directory. By default, the account is enabled, but administrators can disable anonymous logon altogether on sensitive and secure servers. In this case, the initial request to view the home page for the web server will result in a logon dialog box and the web user must provide a valid user name and password.
IIS Directory Structure
The IIS installation process creates a directory structure for IIS called C:\InetPub\wwwroot (or something similar depending on the version), but you can change the name during installation. The directory becomes the home directory and contains a file called default.htm, a sample file that you can overwrite with your own default.htm file. When a web user accesses the web server using a web browser and the HTTP protocol, the default.htm file in this directory is automatically returned to the user’s web browser.
Note: When web users access the IIS home directory, they do not see the directory name C:\InetPub\wwwroot. To them, the directory appears as the root of the server. The address field in their browser will appear with the name of the web site, such as http://www.website.com.
You can customize directory structures in a variety of ways. For example, you can add additional files in the home directory that users can access by clicking a button on the default home page or other related pages. You can also create subdirectories that branch from the home directory, then set special permissions in the directories. For example, figure 12.11 shows two directories branching from the home directory.
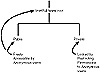
Figure 12.11 IIS creates a root directory for web services where you can create branching sub-directories. Permissions can be set individually in each subdirectory.
The private directory has restricted access. This restricted access is done by revoking permissions for the anonymous user account in the directory. You then grant permissions to the user or group accounts that can access the directory and have users log on using those accounts. For example, the private directory may contain sensitive information that only remote and mobile employees can access. You create a group called “Remote Employees” and grant it access to the directory. When a remote employee visits the web site and attempts to access the directory, a logon dialog box appears where they can enter their credentials. This box appears if the anonymous user account does not have permissions in the directory.
IIS Permissions
The IIS web server has its own set of permissions that apply to the home directory and the virtual directories that are accessible by web clients. These permissions are in addition to the NTFS permissions in each directory. The permissions are as follows:
Warning: Never apply the Write and Execute permission to the same directory because it would allow someone to upload a harmful program and then execute that program on your web server.
| Previous | Table of Contents | Next |