

|
|
| Previous | Table of Contents | Next |
The first step in making the Internet connection for a web server running IIS is to get an account with an Internet service provider and decide on the type of connection you want. A number of decisions need to be made, such as the name of the domain, the amount of bandwidth for the connection, whether you use a dedicated high-speed line, or a dial-up line that is on all the time, the type of router to use for the connection, and how IP addressing will be configured. These issues can be taken up with your ISP. They are not particularly related to security and therefore are not covered in this section.
Besides all the choices, you need to decide on a connection scheme that will protect your systems against attacks by intruders and hackers.
As mentioned, routers are required to make the connection from your web server or proxy server to your Internet service provider as pictured in figure 12.7. Many routers now available on the market include sophisticated firewall features, or at least include packet filtering and protocol filtering features that can serve as a first line of defense against attacks on your system. You can use these routers to supplement Windows NT’s own security features.
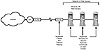
Figure 12.7 Packet filtering routers can provide a first line (but not the only line) of defense against intruder attacks.
Packet filtering routers are available from most router vendors. As mentioned, they provide one line of defense and should not be considered for ultimate protection. Some routers such as those from Ascend (http://www.ascend.com) do provide advanced firewall features, but they are more expensive than most routers for this configuration.
A packet filtering router will enable you to filter incoming packets based on the address in packets or the port number in the packet. For example, you can choose to discard packets that have the source address of your competitor. Note that this is not foolproof because a skilled user can forge a different address. In addition, users that operate from behind firewalls usually don’t have an address that relates to their specific machine so filtering may not do a lot of good. Packet filtering is usually more effective when combined with proxy servers and full-featured firewalls that can make more intelligent decisions about whether to admit a packet or not. For example, Microsoft Proxy Server will discard any packets that are not a response to a request from an internal user.
Note: Microsoft Internet Information Server has built-in packet filtering options. Because addresses are not always accurate, the IIS filtering options are actually more useful for blocking annoying or unnecessary traffic from selected sites as previously mentioned. A proxy server or a firewall is needed to take full advantage of packet filtering.
Another option is to use a proxy server connection, which enables internal users to access the Internet but blocks Internet users from accessing the internal network. A big part of the proxy server’s job, however, is to closely monitor traffic coming back into the server as a response to user requests. It must make sure that a response is indeed associated with an internal users request. How it does this is discussed later in this chapter under “Microsoft Proxy Server.”
The trick to setting up a proxy server is to provide a hardware gateway through which traffic can flow in both directions, but under the tight control of the proxy server software. This is almost always done with a dual-homed system as pictured in figure 12.8.

Figure 12.8 Microsoft Proxy Server should be installed on a dual-homed server, which has two network interface cards. One is attached to the Internet and one is attached to the internal network. Routing is disabled between the cards.
A dual-homed system is a system with two network adapters. One adapter is connected to the Internet and the other is connected to the internal network. Windows NT Server is installed on the server along with the Microsoft Proxy Server software. Routing is disabled between the two network adapters and the proxy server is solely responsible for managing traffic between the adapters.
The general rule for any system connected to the Internet is to disable as many services as possible. Any service might have a bug or hidden security weakness that provides an avenue for attack. Some services are inherently insecure, such as Microsoft’s built in SMB (Server Message Blocks) file sharing protocol, which should never be enabled on an Internet-connected server unless you fully understand the implications of running this file sharing service on the Internet. SMB provides an avenue for attack by a hacker that can operate as an SMB client and access shared directories on your system.
There are two methods to disable services in Windows NT. One method is to completely shut down the service so that it does not run in the server at all. The other method has to do with disabling the service on the Internet-connected network adapter in a dual-homed system. In the latter case, the service still runs and is available to users who access the system over the “inside” network connection.
Disabling a service from a network adapter is a matter of removing the “binding” that the service has to the adapter. You must disable binding for SMB file sharing services (Server and Workstation), NWLink IPX/SPX Compatible Transport, WINS Client (TCP/IP), and the NetBEUI Protocol form an Internet-connected adapter.
Figure 12.9 illustrates the dialog box where you disable bindings. You open the Network utility, then click the Bindings tab at the top of the dialog box to display this screen. Note that all the bindings are removed in this example (the cross-mark indicates the binding is disabled) because the system in this illustration is a web server that only needs to run HTTP services.
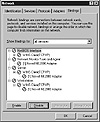
Figure 12.9 The Bindings page is where you disable services that are bound to the Internet-connected network adapter.
| Previous | Table of Contents | Next |