

|
|
| Previous | Table of Contents | Next |
The third scheme is to install a WINS (Windows Internet Naming Service) server, which centralizes name resolution to a single server and eliminates IP resolution broadcasts that can degrade a networks performance. Basically, the WINS server provides a single-server location where internal clients can go to resolve NetBIOS names into IP addresses for the local intranet.
WINS is a service that comes with Windows NT Server. You choose to install it when you set up the Windows NT Server operating system. The details of this service are not important to this discussion. You should make sure to install it, however, during the Windows NT Server installation. Once the service is installed, its operation is nearly automatic. You can usually get by without performing any administrative activities, although some administrators may want to investigate custom settings.
Another service available in Windows NT Server is DHCP (Dynamic Host Configuration Protocol). DHCP will automatically assign IP addresses to clients so you do not need to be burdened as an administrator with this responsibility. Basically, IP addresses are “leased” for a period of time and then released so other stations can use them if necessary. This optimizes the IP address space and ensures that a computer that is not in use for a while does not “hold” an IP address that could be used by another computer.
The main point is to make sure you install the WINS and DHCP services on at least one of your Windows NT Server systems during installation.
Next, this chapter looks at the physical requirements for connecting a Windows NT system to the Internet. Because the goal is to use this system as a web server or as a proxy server and implement appropriate security measures that will protect the system from crackers. Recall that a proxy server enables internal users to access the Internet while preventing outsiders from getting into the internal network.
Most organizations have two requirements when it comes to the Internet:
Note: A third requirement is to allow Internet users or users from other organizations (that is, business partners) to access internal systems. This third requirement, however, is one that is beyond the capabilities of the Windows NT operating system on its own and one that requires the use of additional firewall software as discussed in a moment.
As shown in figure 12.6, a Windows NT web server is often set up as a stand-alone system that is not connected to the internal network. Such a connection might provide a pathway for Internet hackers into the internal network.
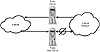
Figure 12.6 Windows NT systems can operate as proxy servers and as public web servers. Note that the web server is disconnected from the internal network.
There is usually little reason to connect a public web server to an internal network in the first place. If internal users need to view the web server information that you publish, creating a duplicate server on the internal network with the same information is better. Alternatively, internal users with a connection to the Internet can “backtrack” to your Internet-connected web server once they make a connection to the Internet.
There is only one problem with setting up a web server that has no internal connections; your content providers will have trouble updating information on the server or monitoring the activities of users. Assume the web server is physically located in the IS (information systems) department but the content providers work in marketing. They could walk their updates over to IS and install them on the server or they could send the updates to an administrator in IS to install on the server. Better yet is an actual network connection to the server, but this must be set up with caution because it provides a pathway for intruders to the internal network if both networks are running the TCP/IP protocol.
One technique to solve the above problem is to use a replication scheme in which the web server is connected to a replication server via a non-TCP/IP link such as IPX. The replication server is connected to the internal network and the web server is connected to the Internet. Any information or updates placed on the replication server by content providers is automatically replicated to the web server over the IPX link. Internet hackers cannot cross the IPX link. This “protocol isolation” technique keeps the internal network secure.
Going beyond the public web server approach, you may want to use Windows NT to provide connections to the Internet for your internal users. This provision can be done with a properly configured NT system running Microsoft Proxy Server, covered in a later section.
As mentioned earlier, in some cases, you may actually want to allow Internet users to access internal system. Those users might be your own mobile or remote employees who are using the Internet as their link to the corporate office. In other cases, the Internet users are business partners. In all of these cases, you need powerful firewall systems like those available from the following vendors. You can check the web sites listed in table 12.1 for additional information.
| Firewall Vendor | Web Site Address |
|---|---|
| AltaVista Firewall for NT from Digital Equipment Corp. | http://www.dec.com |
| Eagle Firewall from Raptor Systems Inc. | http://www.raptor.com |
| Firewall-1 from Checkpoint Software Technologies | http:/www.checkpoint. com |
| Firewall/Plus from Network-1 Software and Technology Inc. | http://www.network-1.com |
One thing to keep in mind throughout this discussion is that the Windows NT on its own does not make a suitable firewall between the Internet and an internal network. You cannot properly configure the firewall to sufficiently protect the internal network. You can set it to do a good job of protecting the server itself, but even then you should consider such server expendable, which means that backups should always be at hand to rebuild a server that some hacker has corrupted.
The next two sections discuss hardware configurations for public web servers and proxy servers.
| Previous | Table of Contents | Next |