

|
|
 |
Using the IT Baseline Protection Manual
2.2 Assessment of Protection Requirements
2.3 IT Baseline Protection Modelling
2.5 Supplementary Security Analysis
2.6 Implementation of IT Security Safeguards
2.7 IT Baseline Protection Certificate
Implementation and maintenance of a reasonable level of IT security can only be ensured if all those involved proceed in a planned and organised fashion. The efficient implementation of IT security safeguards and review of their efficacy therefore necessitates a well thought out and controlled IT security process.
This IT security process begins with definition of the IT security objectives and the establishment of IT security management. The function of IT security management is to draw up and implement an IT security concept. As IT security is maintained in ongoing operations the IT security process regularly entails returning to the security concept so as to permit a continuous process. This approach is illustrated schematically in the diagram below.
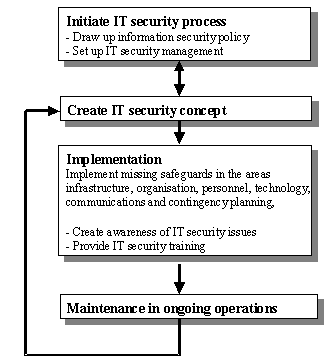
Figure: IT security process
Further information on the area of IT security management will be found in Chapter 3 of this manual.
The primary function of IT security management is to draw up the IT security concept, which is indispensable to the implementation of the necessary IT security safeguards. In the next few sections of this chapter a description will therefore be provided as to how an IT security concept can be created using the IT Baseline Protection Manual.
The general procedure to be followed is illustrated diagrammatically in the figure below:
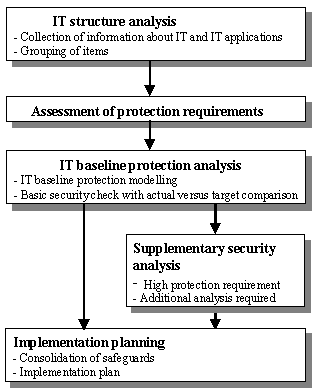
Figure: Creation of an IT security concept
Once information on the existing IT assets has been collected, the protection requirement is assessed. In the IT baseline protection analysis which follows, first of all the IT infrastructure under consideration is modelled using modules from the manual. A target versus actual comparison between the recommended standard security safeguards and the safeguards which have already been implemented is then carried out. If any components are identified during assessment of the protection requirement as having a high or very high protection requirement, then it is recommended that a supplementary IT security analysis is carried out after the IT baseline protection analysis. This can also be necessary in any instances where the IT Baseline Protection Manual does not contain any suitable modules. After the IT security concept has been drawn up using the IT Baseline Protection Manual, a plan is then prepared for implementation of the IT security safeguards identified and consolidated.
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
last update: October 2000 |