

|
|
 |
2.1 IT Structure Analysis
The IT structure analysis provides the means for performing a preliminary survey aimed at collecting information which will be needed later on when drawing up an IT baseline protection security concept. It is split into the following sub-tasks:
These sub-tasks are described below and explained by means of an accompanying example. A detailed version of the example is included with the auxiliary aids contained on CD-ROM which comes with the IT Baseline Protection Manual.
Analysis of a network plan
A network plan (for example in the form of a network topology plan) can be a useful starting point for the IT structure analysis. A network plan is a graphical representation of the components used in the IT and communications area under consideration and of the manner in which they are networked together. The plan should represent the following objects:
Moreover, for each of the objects represented there should be a minimum set of information which can be obtained from an assigned catalogue. As a minimum, the following information should be noted down for each IT system:
Certain information is needed not only for the IT systems themselves but also for the network connections between the systems and for connections to the outside world, namely
If the IT assets in the company/agency have exceeded a certain scope, it is recommended that suitable support programs are used to help with data collection and maintenance of the network plan, as the documentation may be quite complex and require constant updates.
Updating of the network plan
As the IT structure is generally adapted to the specific requirements of the organisation and maintenance of the network plan ties up certain resources, the network plan will not always be up-to-date. In practice often only major changes in the IT structure of individual areas actually result in the plan being updated.
With regard to use of the network plan for the IT structure analysis, the next step entails comparing the existing network plan (or partial plans, if the overall plan has been divided into smaller sections to make it easier to read) with the actual existing IT structure and if necessary updating it to reflect the current situation. During this activity, those responsible for IT and any administrators of individual applications and networks should be consulted. If any programs are used for centralised network and system management, a check should be made in every case as to whether these programs offer any support in drawing up a network plan. However, it should be noted that functions for the automatic or semi-automatic detection of components temporarily generate additional network traffic. Steps must be taken to ensure that this network traffic does not impair IT operations.
Reducing complexity by identifying groups of similar assets
The next step is to remove from the network plan any information which is not necessary for the next set of tasks, in order to make it easier to use. Accordingly, any identical components should be combined into one group which is represented in the network plan by a single object. Components may then be assigned to one and the same group if all the components
If these conditions are adhered to in assigning individual assets to a single group, then for the purposes of IT security it may be assumed that a sample from one group will be representative of the IT security state of the group as a whole.
By far the most important instance where grouping of components in the network plan is appropriate is the grouping together of client computers. Usually there will be a large number of clients within a company/agency which, however, can be reduced to a manageable number of groups if the procedure outlined above is followed. If the number of IT assets is very large and for reasons of redundancy or throughput many servers perform the same task, servers too can be grouped together.
After the grouping process is complete, the components grouped together are shown on the network plan as a single object. The type and number of components represented in each group should be noted down.
Example: Bundesamt für Organisation und Verwaltung (Federal Agency for Organisation and Administration, BOV) - Part 1
In the discussion below a fictitious governmental department known as the BOV is used to illustrate how a simplified network plan can look. It should be noted that the IT structure of the BOV is by no means optimal as regards IT security. The example is simply used to illustrate the procedure of using the IT Baseline Protection Manual. (The complete example is included among the auxiliary aids on the CD-ROM.)
Let us assume that the BOV is an official body with a staff of 150, 130 of whom have their own workstations. The BOV is geographically split between its main office in Bonn and a branch office in Berlin where, amongst other things, tasks in the areas of policy, standards and co-ordination are performed. Of the 130 staff with IT-supported workstations, 90 work in Bonn and 40 in Berlin.
All the workstations are networked in order that staff can perform their tasks. The Berlin branch office is linked over a leased line. Every employee can call up the standards and regulations to which his work is subject, along with forms and document templates, at any time. All the relevant products of the work are placed in a central database. Draft documents are exclusively prepared, distributed and signed in electronic form. To implement and support all the necessary functionality, an IT department has been set up in Bonn.
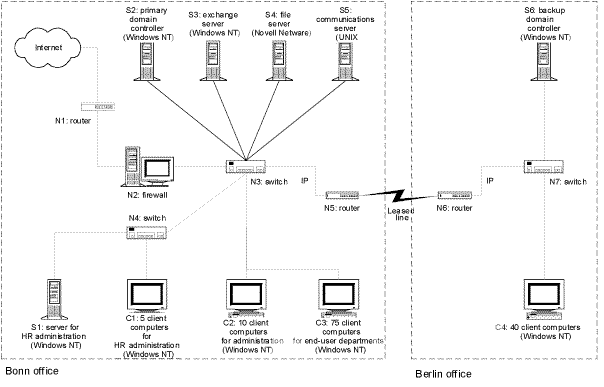
Figure: Example of a simplified network plan
In the network plan illustrated, each IT system (server, client or other active network component) is shown with an identifying number (Sn, Cn, Nn etc.), together with its function and, if appropriate, the operating system is indicated in brackets.
Both in Berlin and in Bonn the clients have been combined into appropriate groups. All 130 clients have virtually the same configuration but there are differences between them as regards the applications, integration into the network and the underlying infrastructure. Group C1 represents the 5 clients in the HR Department. They have access to server S1 in the HR Department in Bonn. C2 and C3 represent the 10 clients in the Administration Department and the 75 clients in the end-user departments in Bonn. The only differences here are in relation to the application programs used. Finally, group C4 represents the clients in end-user departments in Berlin. These differ from groups C1 to C3 in the environmental infrastructure and their integration into the overall network.
Collecting information about the IT systems
The next step relevant to the assessment of protection requirements and modelling of the IT assets to be subsequently performed is to prepare a list of the existing and planned IT systems in tabular form. The term "IT system" refers here not only to computers in the narrower sense, but also to other active network components such as network printers, private branch exchanges (PBX) etc. The focus here is on the technical implementation of an IT system, e.g. stand-alone PC, Windows NT server, PC client under Windows 95, UNIX server, PBX. At this point, only the system as such (e.g. UNIX server) should be recorded, rather than the individual elements which make up the IT system (i.e. CPU, keyboards, monitors etc. should be omitted).
Both networked and non-networked IT systems should be recorded, i.e. in particular, any IT systems which are not already included in the network plan previously considered. IT systems which have been grouped together as part of the exercise of simplifying the network plan can be viewed from now on as a single object. Again, the IT systems which are not included on the network plan should be checked to see whether it would be logical to group some of them together. For example, this might be possible if there is a large number of stand-alone PCs which satisfy the conditions stated as being necessary for grouping in the "Reducing complexity by identifying groups of similar assets" section above.
When collecting the data, the following information which will be needed at subsequent stages should be noted down:
Example: Bundesamt für Organisation und Verwaltung (Federal Agency for Organisation and Administration, BOV) - Part 2
As an example, the table below shows an excerpt from the list of IT systems in the BOV. (The complete list is included in the auxiliary aids provided on the CD-ROM.)
| No. | Description | Platform | Number | Installation site | Status | User(s) / Admin. |
| S1 | Server for Human Resources | Windows NT Server | 1 | Bonn, R 1.01 | Operational | Human Resources |
| S2 | Primary domain controller | Windows NT Server | 1 | Bonn, R 3.10 | Operational | All IT users |
| C1 | Group of clients in HR data processing | Windows NT Workstation | 5 | Bonn, R 1.02 - R 1.06 | Operational | Human Resources |
| C2 | Group of clients in the Administration Department | Windows NT Workstation | 10 | Bonn, R 1.07 - R 1.16 | Operational | Administration Department |
| C6 | Group of laptops for the Berlin office | Laptop under Windows 95 | 2 | Berlin, R 2.01 | Operational | All IT users in the Berlin office |
| N1 | Router connecting to the Internet | Router | 1 | Bonn, R 3.09 | Operational | All IT users |
| N2 | Firewall | Application gateway on UNIX | 1 | Bonn, R 3.09 | Operational | All IT users |
| N3 | Switch | Switch | 1 | Bonn, R 3.09 | Operational | All IT users |
| T1 | Private branch exchange for Bonn | ISDN PBX | 1 | Bonn, B.02 | Operational | All staff in the Bonn head office |
IT systems/groups S1, S2, C1, C2, N1, N2 and N3 are taken directly from the network plan. In addition, the non-networked IT systems C6 (laptops) and T1 (PBXs) have been added.
Capturing information about the IT applications and related information
To reduce the amount of effort required, in each case only the most important IT applications already running or planned to be run on the IT systems under consideration have been included. It is not essential for the efficient performance of this task to record every application as long as all IT applications for a given IT system which fall within the following three categories are specified:
To ensure that all the necessary data is collected, when recording information about IT applications the users and/or those responsible for a given IT application should be asked to provide an assessment.
The definition and gathering of information about IT applications is easier if the IT applications are compiled in a manner which is oriented to the IT systems. Due to their widespread impact, the servers should be the first items on which information is collected. To obtain as balanced a picture as possible, the survey can then be completed to include the clients and stand-alone systems. Which network switching elements support which IT applications must then be established.
It can be helpful here to assign a serial number to each application for reference purposes. As many IT Security Officers also perform the role of Data Privacy Officer responsible for the protection of person related data, we recommend making a note at this point as to whether any person related data is stored and/or processed on the described IT application.
The applications are then in each case assigned to the IT systems which are necessary to run them. This can be the IT systems on which the IT applications are processed, but it could also include IT systems which transfer data generated within the applications.
The result of this exercise is a summary of which major IT applications are processed on which IT systems, used by which IT systems and/or transferred by which IT systems. It is recommended that the results are documented in tabular form.
Example: Bundesamt für Organisation und Verwaltung (Federal Agency for Organisation and Administration, BOV) - Part 3
The table below shows an excerpt from the data collected on IT applications and their assignment to the IT systems concerned in the fictitious example of the BOV.
Description of the IT applications
IT-Systems
| Applicn no. | IT application / information | Person related data | S1 | S2 | S3 | S4 | S5 | S6 | S7 |
| A1 | Processing of HR data | X | X | ||||||
| A2 | Benefits processing | X | X | ||||||
| A3 | Travel expense accounting | X | X | ||||||
| A4 | User authentication | X | X | X | |||||
| A5 | System management | X | |||||||
| A6 | Exchange (e-mail, diary) | X | X | ||||||
| A7 | Central document administration | X |
Key: Ai X Sj = Execution of IT application Ai depends on IT system Sj.
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
last update: October 2000 |