

|
|
 |
2.3 IT Baseline Protection Modelling
Once the required information is available from the IT structure analysis and the assessment of protection requirements, the next major task is to model the IT assets under consideration with the aid of the existing modules of the IT Baseline Protection Manual. The outcome of this exercise is an IT baseline protection model of the IT assets which is made up from different modules of the manual, in some cases with the same modules being used several times over, and maps the security-relevant aspects of the IT assets onto specific modules and vice versa.
It makes no difference to the IT baseline protection model created whether the IT assets consist of IT systems already in service or whether the IT assets in question are still at the planning stage. However, the model may be used differently depending on whether the assets are already in use or not.
The diagram below clarifies the role of the modelling and its possible outcomes:
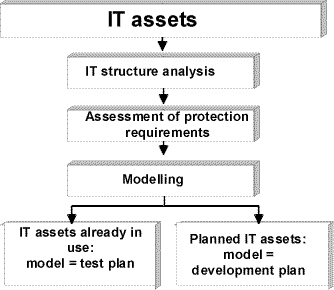
Figure: outcome of IT baseline protection modelling
Typically a set of IT assets currently in use will contain not only elements which have already been implemented but also elements which are still at the planning stage. The resulting IT baseline protection model then contains both a test plan and also elements of a design concept. The IT security concept will then be based on a combination of the IT security safeguards which are identified during the target versus actual comparison as being inadequate or missing and those identified for IT assets which are still at the planning stage.
To map a generally complex set of IT assets to the modules in the manual it is recommended that the IT security aspects are considered as groups arranged according to particular topics.
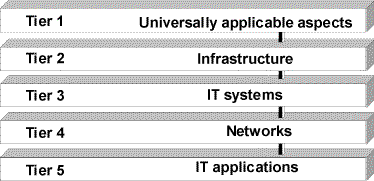
Figure: Tiers in the IT baseline protection model
The IT security aspects of a set of IT assets are assigned to the individual tiers as follows:
Using this tier approach has the following advantages.
IT baseline protection modelling entails determining for the modules of a given tier whether and how they can be used to map the IT assets. Depending on the module considered, the objects which are mapped in this way may be of different kinds: individual components, groups of components, buildings, property, organisational units etc.
The IT baseline protection model, i.e. the assignment of modules to target objects, should be documented in the form of a table containing the following columns:
The procedure for modelling a set of IT assets is described in detail in Section 2.3.1 below. Particular importance here is attached to any constraints which apply, when it is appropriate to use a given module and to which target objects it should be applied. Section 2.3.2 presents a shortened modelling procedure for the special case of a single IT system or a single group.
2.3.1 Modelling a Set of IT Assets
When modelling a set of IT assets it is recommended that the modules are assigned using the 5-tier model. This is then followed by the completeness check.
Tier 1: Higher order aspects of IT security
In this tier the generic aspects of the IT assets, which apply to each individual component, are modelled. The primary elements under consideration here are policies and procedures derived from those policies. These aspects should be controlled uniformly for the entire set of IT assets so that in most cases the corresponding modules then only have to be applied once to the entire set of IT assets.
Tier 2: Security of the infrastructure
The structural conditions relevant to the existing IT assets are modelled with the aid of the modules contained in Chapter 4 "Infrastructure". This entails assignment of the relevant module from the IT Baseline Protection Manual to every building, room or protective cabinet (or group of these components).
Tier 3: Security of the IT systems
This tier is concerned with security aspects relating to IT systems, i.e. to server and client computers, hosts, terminals etc. Tier 3 is covered by modules from Chapters 5 to 9 of the IT Baseline Protection Manual.
By analogy with the area "Security of the infrastructure", the modules relating to the area of "Security of the IT systems" may be applied either to individual IT systems or to groups of such IT systems. This is assumed below although no further specific reference to it is made.
Tier 4: Security in the network
This tier is concerned with security aspects in the network which cannot be isolated to particular IT systems (e.g. servers) in the network. Rather, the concern here is those security aspects which relate to the network connections and communications between the IT systems.
To simplify matters, it may be appropriate to consider sections within the complete network rather than the whole network at once. The division of the full network into subnets should be performed in accordance with these two criteria:
If these two criteria do not lend themselves to a suitable division of the full network (for example because some of the resulting subnets are too large or too small), as an alternative the division into subnets may proceed at the organisational level. Under this approach, the subnets are defined so that they correspond to discreet areas of responsibility of the different administrators or teams of administrators.
It is not possible to make a definite recommendation as to how best to subdivide the complete network into subnets, as the requirements stated above might be incompatible with the existing IT assets. Instead, a decision should be made in the individual case as to what is the most practical way of splitting up the complete network, bearing in mind the modules of the IT Baseline Protection Manual which are to be used.
Tier 5: Security in applications
The lowest tier entails modelling of the applications. Modern applications are seldom limited to a single IT system. In particular, core applications used across an entire organisation are generally implemented as client/server applications. In many cases servers themselves access other servers downstream, e.g. database systems. The security of the applications must therefore be considered independently of the IT systems and networks.
Completeness check
In the final step a check should be performed as to whether the entire system has been modelled without any gaps. It is recommended that the network plan or a similar overview of the IT assets is used here and that the individual components are checked systematically. Every component should either be assigned to a group or else be modelled separately. If the complete network has been divided into subnets in connection with Tier 4, a check should be performed as to whether
It is important that not only all hardware and software components are modelled from a technical perspective, but that the related organisational, personnel and infrastructural aspects are fully covered also. This can be checked using the tables provided in Section 2.3.2, in which for a few typical components those modules of the IT Baseline Protection Manual which should be included in the modelling in every case are specified.
If, when performing these checks, any gaps are revealed in the modelling, the relevant missing components must be added. Otherwise there is a risk that important elements of the complete system or important security aspects will be overlooked when using the IT Baseline Protection Manual.
If it is not possible to perform all the modelling because some modules which are needed are missing from the IT Baseline Protection Manual, we would ask you to notify your requirements to the BSI's IT Baseline Protection Hotline.
Bundesamt für Organisation und Verwaltung (Federal Agency for Organisation and Administration, BOV) - Part 8
The table below is an excerpt from the modelling performed for the fictitious BOV Department.
| No. | Name of module | Target object / target group | Contact person | Notes |
| 3.1 | Organisation | Bonn site | The Organisation module must be worked through separately for the Bonn and Berlin sites, as Berlin has its own organisational procedures. | |
| 3.1 | Organisation | Berlin site | ||
| 3.2 | Personnel | Entire BOV | The BOV's Human Resources Department is located centrally in Bonn. | |
| 4.3.3 | Data Media Archives | R U.02 (Bonn) | The backup data media are kept in this room. | |
| 5.3 | Laptop PC | C5 | The laptops in Bonn/Berlin are in each case combined together into a group. | |
| 5.3 | Laptop PC | C6 | ||
| 7.5 | WWW Server | S5 | S5 functions as the server for the Intranet. | |
| 9.2 | Databases | S5 | A database is used on server S5. |
2.3.2 Modelling of an Individual IT System
Depending on the object(s) under examination, the tables below serve different functions. If the IT assets under consideration consists only of a single IT system or a single group of IT systems which have the same configuration, same framework conditions and same applications, then as a minimum the modules required for modelling can be read directly out of these tables. Modules with no entry in the relevant column should be used as well if they are relevant to the individual IT system under consideration.
If on the other hand the IT assets are composed out of different components, then the tables provided below will help in checking whether modelling as described in Section 2.3.1 is complete. If, for example, the present IT assets contain Windows NT clients, then all the modules which have an "X" in the relevant table should be considered during modelling. Modules identified with "(X)" only need to be used when certain conditions apply. These conditions are listed in Section 2.3.1.
Key:
| X | The module must be applied to this IT system. |
| (X) | The module must be applied to this IT system if the conditions specified in Section 2.3.1 apply. |
| X1 | A server room can be replaced by a server cabinet. |
| IT Systems | Stand-Alone Systems / Clients | |||||||
| Module | DOS-PC (Single User) | UNIX System | Laptop PC | PC (Multi-user) | Windows NT PC | Windows 95 PC | ||
| 3.0 | IT Security Management | X | X | X | X | X | X | |
| 3.1 | Organisation | X | X | X | X | X | X | |
| 3.2 | Personnel | X | X | X | X | X | X | |
| 3.3 | Contingency Planning Concept | (X) | (X) | (X) | (X) | (X) | (X) | |
| 3.4 | Data Backup Policy | X | X | X | X | X | X | |
| 3.6 | Computer Virus Protection Concept | X | X | X | X | X | X | |
| 3.7 | Crypto Concept | (X) | (X) | (X) | (X) | (X) | (X) | |
| 3.8 | Handling of Security Incidents | (X) | (X) | (X) | (X) | (X) | (X) | |
| 4.1 | Buildings | X | X | X | X | X | ||
| 4.2 | Cabling | X | X | X | X | X | ||
| 4.3.1 | Offices | X | X | X | X | X | ||
| 4.3.2 | Server rooms | |||||||
| 4.3.3 | Storage Media Archives | |||||||
| 4.3.4 | Technical Infrastructure Rooms | |||||||
| 4.4 | Protective Cabinets | |||||||
| 4.5 | Working Place At Home (Telecommuting) | |||||||
| 5.1 | DOS PC (Single User) | X | (X) | (X) | ||||
| 5.2 | UNIX System | X | (X) | (X) | ||||
| 5.3 | Laptop PC | X | (X) | |||||
| 5.4 | PCs With a Non-Constant User Population | (X) | (X) | (X) | X | |||
| 5.5 | PC under Windows NT | (X) | X | |||||
| 5.6 | PC with Windows 95 | (X) | X | |||||
| 5.99 | Stand-Alone IT Systems Generally | |||||||
| 6.1 | Server-Supported Network | |||||||
| 6.2 | UNIX Server | |||||||
| 6.3 | Peer-to-Peer Network | |||||||
| 6.4 | Windows NT Network | |||||||
| 6.5 | Novell Netware 3.x | |||||||
| 6.6 | Novell Netware 4.x | |||||||
| 6.7 | Heterogeneous Networks | |||||||
| 6.8 | Network and System Management | |||||||
| 7.1 | Exchange of Data Media | (X) | (X) | (X) | (X) | (X) | (X) | |
| 7.2 | Modem | |||||||
| 7.3 | Firewall | |||||||
| 7.4 | ||||||||
| 7.5 | WWW Server | |||||||
| 7.6 | Remote Access | |||||||
| 8.1 | Telecommunications System (Private Branch Exchange, PBX) | |||||||
| 8.2 | Fax Machine | |||||||
| 8.3 | Answering Machine | |||||||
| 8.4 | LAN connection over ISDN | |||||||
| 8.5 | Fax Servers | |||||||
| 8.6 | Mobile Telephones | |||||||
| 9.1 | Standard Software | X | X | X | X | X | X | |
| 9.2 | Databases | |||||||
| 9.3 | Telecommuting | |||||||
| IT Systems | Stand-Alone Systems / Clients | Stand-Alone Systems / Clients | |
| Module | Telecommuting | Stand-Alone IT Systems Generally | |
| 3.0 | IT Security Management | X | X |
| 3.1 | Organisation | X | X |
| 3.2 | Personnel | X | X |
| 3.3 | Contingency Planning Concept | (X) | (X) |
| 3.4 | Data Backup Policy | X | X |
| 3.6 | Computer Virus Protection Concept | X | X |
| 3.7 | Crypto Concept | (X) | (X) |
| 3.8 | Handling of Security Incidents | (X) | (X) |
| 4.1 | Buildings | X | |
| 4.2 | Cabling | X | |
| 4.3.1 | Offices | X | |
| 4.3.2 | Server Rooms | ||
| 4.3.3 | Storage Media Archives | ||
| 4.3.4 | Technical Infrastructure Rooms | ||
| 4.4 | Protective Cabinets | ||
| 4.5 | Working Place At Home (Telecommuting) | X | |
| 5.1 | DOS PC (Single User) | (X) | |
| 5.2 | UNIX System | (X) | |
| 5.3 | Laptop PC | ||
| 5.4 | PCs With a Non-Constant User Population | ||
| 5.5 | PC under Windows NT | (X) | |
| 5.6 | PC with Windows 95 | (X) | |
| 5.99 | Stand-Alone IT Systems Generally | (X) | X |
| 6.1 | Server-Supported Network | ||
| 6.2 | UNIX Server | ||
| 6.3 | Peer-to-Peer Network | ||
| 6.4 | Windows NT Network | ||
| 6.5 | Novell Netware 3.x | ||
| 6.6 | Novell Netware 4.x | ||
| 6.7 | Heterogeneous Networks | ||
| 6.8 | Network and System Management | ||
| 7.1 | Exchange of Data Media | (X) | (X) |
| 7.2 | Modem | (X) | |
| 7.3 | Firewall | ||
| 7.4 | |||
| 7.5 | WWW Server | ||
| 7.6 | Remote Access | ||
| 8.1 | Telecommunications System (Private Branch Exchange, PBX) | ||
| 8.2 | Fax Machine | (X) | |
| 8.3 | Answering Machine | (X) | |
| 8.4 | LAN connection over ISDN | (X) | |
| 8.5 | Fax Servers | ||
| 8.6 | Mobile Telephones | ||
| 9.1 | Standard Software | X | X |
| 9.2 | Databases | ||
| 9.3 | Telecommuting | X |
| IT Systems | Server / Network | ||||||
| Module | UNIX Network | Peer-to-Peer Network | Windows NT Network | Novell 3.x Network | Novell 4.x Network | ||
| 3.0 | IT Security Management | X | X | X | X | X | |
| 3.1 | Organisation | X | X | X | X | X | |
| 3.2 | Personnel | X | X | X | X | X | |
| 3.3 | Contingency Planning Concept | (X) | (X) | (X) | (X) | (X) | |
| 3.4 | Data Backup Policy | X | X | X | X | X | |
| 3.6 | Computer Virus Protection Concept | X | X | X | X | X | |
| 3.7 | Crypto Concept | (X) | (X) | (X) | (X) | (X) | |
| 3.8 | Handling of Security Incidents | (X) | (X) | (X) | (X) | (X) | |
| 4.1 | Buildings | X | X | X | X | X | |
| 4.2 | Cabling | X | X | X | X | X | |
| 4.3.1 | Offices | X | |||||
| 4.3.2 | Server Rooms | X | X | X | X | ||
| 4.3.3 | Storage Media Archives | ||||||
| 4.3.4 | Technical Infrastructure Rooms | ||||||
| 4.4 | Protective Cabinets | X1 | X1 | X1 | X1 | X1 | |
| 4.5 | Working Place At Home (Telecommuting) | ||||||
| 5.1 | DOS PC (Single User) | (X) | |||||
| 5.2 | UNIX System | (X) | |||||
| 5.3 | Laptop PC | (X) | |||||
| 5.4 | PCs With a Non-Constant User Population | (X) | |||||
| 5.5 | PC under Windows NT | (X) | |||||
| 5.6 | PC with Windows 95 | (X) | |||||
| 5.99 | Stand-Alone IT Systems Generally | (X) | |||||
| 6.1 | Server-Supported Network | X | X | X | X | ||
| 6.2 | UNIX Server | X | |||||
| 6.3 | Peer-to-Peer Network | X | |||||
| 6.4 | Windows NT Network | X | |||||
| 6.5 | Novell Netware 3.x | X | |||||
| 6.6 | Novell Netware 4.x | X | |||||
| 6.7 | Heterogeneous Networks | X | X | X | X | X | |
| 6.8 | Network and System Management | ||||||
| 7.1 | Exchange of Data Media | ||||||
| 7.2 | Modem | ||||||
| 7.3 | Firewall | ||||||
| 7.4 | |||||||
| 7.5 | WWW Server | (X) | (X) | (X) | (X) | ||
| 7.6 | Remote Access | ||||||
| 8.1 | Telecommunications System (Private Branch Exchange, PBX) | ||||||
| 8.2 | Fax Machine | ||||||
| 8.3 | Answering Machine | ||||||
| 8.4 | LAN connection over ISDN | ||||||
| 8.5 | Fax Servers | (X) | (X) | (X) | (X) | ||
| 8.6 | Mobile Telephones | ||||||
| 9.1 | Standard Software | X | X | X | X | X | |
| 9.2 | Databases | (X) | (X) | (X) | (X) | ||
| 9.3 | Telecommuting | ||||||
| IT Systems | Communication System | ||||||
| Module | Firewall | Private Branch Exchange | Fax Machine | Answer-phone | Fax Servers | ||
| 3.0 | IT Security Management | X | X | X | X | X | |
| 3.1 | Organisation | X | X | X | X | X | |
| 3.2 | Personnel | X | X | X | X | X | |
| 3.3 | Contingency Planning Concept | (X) | (X) | (X) | (X) | (X) | |
| 3.4 | Data Backup Policy | X | X | X | X | X | |
| 3.6 | Computer Virus Protection Concept | X | X | X | X | X | |
| 3.7 | Crypto Concept | (X) | (X) | (X) | (X) | (X) | |
| 3.8 | Handling of Security Incidents | (X) | (X) | (X) | (X) | (X) | |
| 4.1 | Buildings | X | X | X | X | X | |
| 4.2 | Cabling | X | X | X | X | X | |
| 4.3.1 | Offices | X | X | ||||
| 4.3.2 | Server Rooms | X | X | X | |||
| 4.3.3 | Storage Media Archives | ||||||
| 4.3.4 | Technical Infrastructure Rooms | ||||||
| 4.4 | Protective Cabinets | X1 | X1 | X1 | |||
| 4.5 | Working Place At Home (Telecommuting) | ||||||
| 5.1 | DOS PC (Single User) | ||||||
| 5.2 | UNIX System | ||||||
| 5.3 | Laptop PC | ||||||
| 5.4 | PCs With a Non-Constant User Population | ||||||
| 5.5 | PC under Windows NT | ||||||
| 5.6 | PC with Windows 95 | ||||||
| 5.99 | Stand-Alone IT Systems Generally | ||||||
| 6.1 | Server-Supported Network | X | X | ||||
| 6.2 | UNIX Server | (X) | (X) | ||||
| 6.3 | Peer-to-Peer Network | ||||||
| 6.4 | Windows NT Network | (X) | (X) | ||||
| 6.5 | Novell Netware 3.x | (X) | (X) | ||||
| 6.6 | Novell Netware 4.x | (X) | (X) | ||||
| 6.7 | Heterogeneous Networks | X | X | ||||
| 6.8 | Network and System Management | ||||||
| 7.1 | Exchange of Data Media | ||||||
| 7.2 | Modem | ||||||
| 7.3 | Firewall | X | |||||
| 7.4 | |||||||
| 7.5 | WWW Server | ||||||
| 7.6 | Remote Access | ||||||
| 8.1 | Telecommunications System (Private Branch Exchange, PBX) | X | |||||
| 8.2 | Fax Machine | X | |||||
| 8.3 | Answering Machine | X | |||||
| 8.4 | LAN connection over ISDN | ||||||
| 8.5 | Fax Servers | X | |||||
| 8.6 | Mobile Telephones | ||||||
| 9.1 | Standard Software | X | X | ||||
| 9.2 | Databases | ||||||
| 9.3 | Telecommuting | ||||||
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
last update: July 2001 |