

|
|
| Previous | Table of Contents | Next |
How Stealth File Viruses Work
The file infecting stealth virus must install a memory-resident service provider to intercept any requests made by DOS or other applications to access program files. This service provider must determine whether the file being accessed contains a copy of the virus. If the program file is infected, the virus service provider must conceal the virus’ presence in the file.
A size stealthing file virus behaves as follows: If the virus is resident and the user takes a directory of their files, the virus must conceal the size increase of all infected files. To do so, it hooks into a system service used by the DOS command interpreter (COMMAND.COM) to find and obtain information on disk files. The DOS DIR command invokes this system service in the DOS kernel for each file present in a given directory. Each time DOS requests this service for a new file, the virus allows the DOS kernel to service the request, and then examines the results, which include the filename, its date and timestamp of last modification, the file’s attributes, and its size.
By examining the service request results, the size stealth file virus knows exactly which file is being processed. It can scrutinize the file to determine whether it is infected. If the virus decides that the file does harbor a copy of the virus, it can change the file size field, subtracting out the virus size from the actual size of the program. The virus then passes the modified results on to the DOS command interpreter, which then shows the file with its original size.
Size stealthing viruses use many different methods to determine whether a file is infected. When a program is first infected, for example, many size stealthing viruses update the timestamp of the target file to include a special value in the seconds field. At least several viruses update the seconds field in the timestamp to include an invalid value of 62 seconds. Because DOS never displays the seconds field when the user lists directory contents, this usually goes unnoticed. Later, when the user takes a directory of her files, the virus can determine whether a file has been infected by examining the timestamp on the file. If the timestamp is invalid (and equal to 62), the virus assumes that the program is infected and hides the file size increase.
Using the preceding technique eliminates the need for the virus to examine the contents of each program for the viral presence. This is advantageous to the virus because checking the contents of each file during a directory listing would measurably slow down the listing, possibly alerting the user.
Although the timestamp scheme is fast, it isn’t without flaws. If an uninfected file happens to be stamped with an invalid timestamp, the virus may mistakenly assume the file is infected and inadvertently change the file’s size. The user then might notice a decrease in size on certain files and be tipped off to the presence of the virus.
Read stealthing file viruses use several different techniques to conceal infections. The virus still installs a special resident service provider that monitors access to all files on the computer. However, rather than intercepting file information requests, the virus service provider intercepts those services used to open, read the contents of, or close a file.
In the most common read stealthing scheme, if the viral resident handler detects a request to open an executable file, it examines the program contents to determine whether the file is infected. If the virus detects a copy of itself in the file, it disinfects the file on the fly, writing out the disinfected program back to the disk. It then allows the service requester to do whatever it likes to the file. Finally, when the application closes the file, the virus handler again seizes control and reinfects the executable file.
Slow viruses are memory-resident viruses that infect programs and boot records using covert, non-stealthing techniques. A typical resident virus, for example, opens the program being executed, writes the virus to the program, then closes it. Behavior such as writing to a program file is usually monitored by antivirus software, and the virus may be detected as a result.
Rather than replicating on its own, the slow virus waits in memory for system service activities to take place that are seldom (or never) examined by an antivirus program.
For example, a slow virus might hook into the DOS system service that is used by the DOS command interpreter (COMMAND.COM) to copy files. When DOS services this copy request, it reads from the source file into memory, then writes this memory image to the destination file. During this process, DOS reads and then loads the file into memory in portions of 64 KB at a time. The slow virus waits for DOS to load a file portion into memory, then inserts its viral code in the file while it is in memory. Figures 15.32 and 15.33 illustrate the first two phases of a slow virus infection.
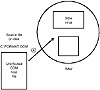
Figure 15.32 User copies COM file to new directory (or disk).
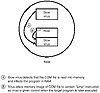
Figure 15.33 The second step of slow virus infection.
DOS then writes a memory image that contains both the original file portion and the virus to the copy destination (see fig. 15.34). Antivirus programs can’t determine if a program makes any changes to computer memory. Such an approach, then, would allow the slow file virus to infect a new program without engaging in any behavior that antivirus software can easily monitor.
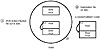
Figure 15.34 DOS completes the process. The destination file is infected.
| Previous | Table of Contents | Next |