

|
|
| Previous | Table of Contents | Next |
Stealth viruses attempt to conceal their presence from the user. Most stealth viruses conceal themselves only while the virus is active in memory and hooked into the operating system as a service provider. These viruses actively intercept system requests that might reveal information about the viral infection and alter the system service output to conceal their presence. Figure 15.31 presents an overview of the boot stealthing process.
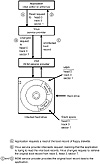
Figure 15.31 Operation of a stealth MBR virus.
Stealth viruses are typically classified as having size stealth or read stealth capabilities, or both. Size stealthing applies exclusively to file infecting viruses. When a virus infects a program file, the virus usually attaches a copy of itself onto the target program file. This results in the target file growing in size by the length of the virus. Because a user might notice such a difference in file size, the size stealthing virus masks the size increase. (Believe it or not, some users, especially antivirus researchers, do remember the size of certain executable files on their system.)
By examining the infected file’s contents, a user could see the virus and the changes it has made to the program. This type of stealthing, then, is somewhat like hiding during a game of hide-and-seek by placing a lampshade over one’s head. However, most users don’t examine the binary contents of their program files, and if they don’t notice any change in the overall computer performance or in the size of their programs, they probably won’t notice the viral infection. As workstations become faster, decreases in performance may be even less noticeable, at least at first.
With read stealthing, when the operating system or another program makes a request to read an infected boot record or file, the virus intercepts the request and provides the requester with the original, uninfected contents.
The Stoned.Monkey virus, for example, uses read stealthing. If a user executes a disk editing utility to examine the MBR contents, where Stoned.Monkey hides, he or she won’t find any evidence of infection. Stoned.Monkey’s system service routine is called anytime the disk is accessed, and it checks to see whether any attempts are being made to read the MBR. If so, the virus provides a backed-up copy of the original item in place of the infected copy. This stealthing can be defeated by specially written tools and antivirus programs, but goes undetected by the average disk utility.
Read stealthing also serves to conceal viruses in program files. Usually, the read stealthing file virus possesses size stealthing capabilities as well; it would be useless for a program to hide content changes to an infected file, yet still show the increased file size. As an example, the Tremor virus uses both read stealthing and size stealthing to conceal its presence in infected files.
Most stealth viruses can conceal their presence only while resident and active in the computer’s memory. If they are not installed as a memory-resident service provider, any infection is visible. This is why most antivirus manufacturers instruct users to boot from a write-protected, uninfected floppy disk before scanning for, or repairing, virus infections.
How Stealth Viruses Work
Many stealth viruses conceal themselves only when active in memory and hooked into the operating system as a service provider; for example, the FBR, MBR, or PBR stealth viruses. The typical boot virus installs itself into memory as a resident service provider. In the case of a boot virus with stealth qualities, the service provider examines all read and write requests to the drives attached to the system.
If the virus detects that DOS or another application is trying to read the boot sector of an infected disk, it can locate the original, uninfected copy of FBR, MBR, or PBR and pass this along to the requesting program. Similarly, if a program attempts to write to the boot record of an infected disk, the virus can choose to overwrite the backed-up copy of the boot record as opposed to the actual, viral boot record present on the disk. The virus uses this strategy while resident to protect itself from being detected or overwritten from infected media.
To provide this functionality, the resident portion of the stealth boot virus must be able to detect whether a disk is infected; if infected, the virus must at this point hide the infection. If uninfected, the virus at this point would normally infect it.
A user might, for example, have the hypothetical ZYX virus on her computer. On infected floppies, the ZYX virus places the original FBR in track 0, head 0, sector 3. If the user inserts an uninfected floppy disk into the disk drive and uses a disk editor to examine the FBR, the virus must understand that the disk isn’t yet infected and provide the actual boot record at track 0, head 0, sector 1. However, if the user inserts an infected floppy disk into the drive, the virus must detect the infection and provide the backed-up boot record from track 0, head 0, sector 3.
Some stealth boot record viruses only conceal the virus while it is in the hard drive’s MBR or active PBR, because this is an easy task. The virus assumes that if it’s resident, the hard drive’s PBR or MBR must be infected. This is possible because if the user booted off the hard drive and the virus is memory-resident, the virus must have loaded from the active partition’s MBR or PBR.
On the other hand, if the user booted from an infected floppy disk to start the computer, then the virus most likely infected the MBR or active PBR when it first obtained control during floppy bootup. The virus still can safely assume that the MBR or PBR must be infected and can stealth it without explicitly checking the MBR or PBR for infection.
Although the virus can safely assume that if it is resident, the MBR or PBR is infected, it can’t assume the same with floppy disk boot records. Because the user can insert different floppy disks into a drive, the virus must explicitly examine the boot record of each disk to determine whether it is already infected. If infected, the virus can hide the original boot record. If uninfected, the virus can infect the boot record.
| Previous | Table of Contents | Next |