

|
|
| Previous | Table of Contents | Next |
This whole process repeats again on the next 64-bit block of the original plaintext. Note that many of the intricate details of the process have been left out for clarity. You can get these additional details by referring to one or more of the web sites listed in table 10.6.
| Site Name | Address |
|---|---|
| DES: The Data Encryption Standard | http://www.cs.wm.edu/~hallyn/des/ |
| The Data Encryption Standard | http://raphael.math.uic.edu/~jeremy/ crypt/contrib/stj.html |
| DES | http://snoopy.falkor.gen.nz/~rae/DES.html |
| Implementing DES | http://www2.andrews.edu/~buttler/ des_project.html |
DES has always been controversial. The biggest concern is that it may have an unknown weakness or a weakness that is only known by the NSA. The possibility of a brute force attack, which is an attack that uses a lot of money and a lot of processing power to break a cipher, exists. Some feel the NSA already has this potential. Originally, the proposed key size for DES was 64 bits, but this was reduced to 56 bits just before approval as a standard. Some feel that reducing the key size gave the U.S. Government, using the powerful computer systems at NSA, the potential to break the code.
The 56-bit key space of DES has been considered susceptible to an attack for some time. An extension to DES called DESX is considered to be virtually immune to an exhaustive key search. Key searches are described later under Attacks and Cryptanalysis.
All other block ciphers are considered alternatives to DES because DES was the first publicly available standard. Alternatives include IDEA (International Data Encryption Algorithm) and Ron Rivest’s RC ciphers. These ciphers are discussed next.
IDEA (International Data Encryption Algorithm)
IDEA is a block-oriented secret key encryption algorithm developed by the Swiss Federal Institute of Technology. It uses a 128-bit key compared to DES’s 56-bit key and encrypts one 64-bit block at a time. The algorithm was strengthened to protect against a particular kind of attack called differential cryptanalysis, which is discussed under Attacks and Cryptanalysis. The algorithm is readily available to everybody—its security is based not on hiding the algorithm but on keeping a secret key.
Some additional features are:
As of this writing, there have been no successful attacks against IDEA. A brute force attack could be tried, but with the extended key length of 128 bits, it has been estimated that trying 1 billion keys per second for over a billion years would still not find the key. Therefore, brute force attacks are ruled out as a problem with IDEA.
To illustrate how an alternative algorithm works, the IDEA algorithm is pictured in figure 10.15 and described in the simplest way.
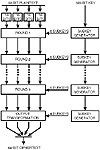
Figure 10.15 The IDEA algorithm goes though eight rounds to scramble and encrypt information.
Of course, these operations are greatly simplified to show the basic progression of the algorithm. As mentioned, sub-blocks are crossed over during the iteration stages to mix up the bits. Also, the subkey generator produces 52 distinct 16-bit subkeys to use during the entire process—six for the eight rounds and four for the final output transformation.
ASCOM has additional information about IDEA at their web site: http://www.ascom.ch/web/systec/security/page1.htm.
RC2, RC4, and RC5
The RC ciphers were designed by Ron Rivest for RSA Data Security (http://www.rsa.com), now owned by Security Dynamics (http://www.securid.com). RC is said to stand for “Ron’s Code” or “Rivest’s Cipher.” Rivest designed RC2 as a “drop-in” replacement for DES that is more secure. It is a block cipher with a variable key size that employs a confidential and proprietary algorithm.
An advantage of RC2 and RC4 is that they have special export status with the United States government, meaning that export approval is quick and easy. However, key size is limited to 40 bits (56 bits for foreign subsidiaries and overseas offices of United States companies). RC2 and RC4 are commonly used in products that are exported while DES is almost never approved for export, according to “Frequently Asked Questions About Today’s Cryptography,” available at the RSA web site: http://www.rsa.com.
Note that RC4 is a stream cipher with a variable key-size and a byte-oriented operation (as opposed to bit-oriented like other stream ciphers). While the algorithm is confidential and proprietary, it is known to randomly permutate data. RSA Data Security claims that it has been scrutinized under conditions of non-disclosure by independent analysts and it is considered secure.
RC5 is a block cipher built for speed. The block size, key size, and number of iterations (rounds) are all variable. In particular, the key can be as large as 2,048 bits. The algorithms used by RC5 help to defeat differential and linear cryptanalysis. Further information on RC5 can be obtained at http://www.rsa.com/rsalabs/pubs/cryptobytes/spring95/rc5.htm.
| Previous | Table of Contents | Next |