

|
|
| Previous | Table of Contents | Next |
As mentioned, there are block ciphers (that is, cryptographic algorithms) and stream ciphers. These two different types of ciphers are outlined next. The description of popular ciphers given later defines ciphers as either block or stream.
The following discussion explains in the most general way how cryptographic algorithms work. This is not easy because cryptographic algorithms are necessarily complex. Remember that the plaintext input is methodically rearranged, inverted, and altered to produce unintelligible ciphertext. The process must be repeated exactly to restore the plaintext. To get an idea of this process, picture spilling water on the floor. No two glasses of water ever spill the same way or produce the same results. Now picture running a movie in reverse of the spill. Every drop of water goes back into place exactly as it came out and that is exactly what decryption must do.
Following this analogy, a block cipher works as if you spilled a glass of water one tablespoon at a time. A stream cipher is like a slow steady spill. Later, you will read about a different analogy, that of a weaving loom, to explain how plaintext is converted into ciphertext.
Block Cipher
In this scheme, plaintext is transformed into ciphertext, usually in blocks of 64 bits. Each block is usually processed multiple times, “scrambling” the original input over and over again to make it as unintelligible as possible. In each round, the key is applied in a unique way to mix up the input of each round. The more iterations that are performed, the longer the process takes but the more secure the resulting ciphertext.
Stream Cipher
Stream ciphers are typically much faster than block ciphers. Plaintext is streamed as raw bits through the encryption algorithm. While block ciphers will produce the same ciphertext from plaintext if the same key is used, the ciphertext produced by a stream cipher will vary under the same conditions.
There are several popular secret key encryption schemes, including the U.S. Government’s Data Encryption Standard (DES), Triple DES, IDEA (International Data Encryption Algorithm), and the Rivest Ciphers (RC2, RC5). This section covers DES. The next few sections cover the other popular methods.
DES was originally developed by IBM in the 1970s, but became U.S. Government standard in 1977 after NIST (National Institute of Standards and Technology) reviewed proposals and chose it as a national standard. It is defined in the U.S. Federal Information Processing Standard 46 (FIPS PUB 46). Although the U.S. Government has indicated that it may not recertify DES in 1998, it provides a good example of how an encryption algorithm works.
DES has the following features:
It is a good choice for in-house use where keys can be easily exchanged. It is often used to encrypt data streams over private network routers and to encrypt data stored on disk. To this day, DES has presumably remained secure, despite continuous brute force attacks against it. Brute force attacks are discussed later under Attacks and Cryptanalysis.
The DES algorithm is pictured in figure 10.14 and described in the steps below. Basically, the algorithm goes through 16 iterations (rounds) that interweave the blocks of plaintext and mixes in values obtained from the key. It helps to picture the algorithm acting like a loom that weaves threads together. The plaintext is split into two threads and the key acts as a dye that alters the threads colors during each round. The result is a multicolored interwoven cord.
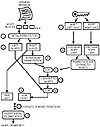
Figure 10.14 The DES algorithm goes through a 16 rounds to scramble and encrypt information.
The following example is meant to give you some concept of how inextricably woven the plaintext and key become. Complex details are left out, but you can read about them at the web sites listed later.
Here is a description of the process, starting with the plaintext on the left side of the diagram.
| Previous | Table of Contents | Next |