

|
|
| Previous | Table of Contents | Next |
Now suppose you want to send someone a message and you want to provide some proof that the message is actually from you. In this case, you reverse the normal procedure and encrypt the message with your private key. When the recipient receives the message, he decrypts it with your public key. Since only your public key can decrypt the message, this step proves that the message is from you.
The above scheme assumes that the message contents do not need to be hidden during transmission. To keep a message private and provide proof it is from you requires two encryptions. One way to do this is to do a special encryption on the text of the message with your private key, then encrypt it again with the public key of the recipient. This way only the recipient can open the message with his or her private key. Then the recipient uses your public key to verify the contents. This is the essence of a digital signature.
There is one more important encryption technique worth mentioning up front and that is the one-way function. It is basically a non-reversible “quick” encryption. In other words, encrypting is easy but decrypting is not easy. While encryption may take only seconds, any attempts to break the encryption could take hundreds, thousands, or millions of years using the most powerful computers, depending on the method used for encryption.
One-way encryptions are used for a number of useful purposes. Assume you have a document to send someone or store for the future and you need a way to prove at some time that the document has not been altered. You run a one-way function, which produces a fixed-length value called a hash (also called a message digest). The hash is a unique signature of the document that you can keep and send with the document. The recipient can run the same one-way function to produce a hash that should match the one you sent with the document. If the hashes do not match, the document has been altered or corrupted.
Note that secret (symmetric) key cryptography is not outmoded by public/private key encryption. In fact, it is very much alive. It is used for storing information on disk or exchanging secret files with people in the same office where you can just hand them the file and the key.
Figure 10.2 illustrates the three primary cryptographic techniques discussed so far and which are discussed in further detail later. Table 10.1 summarizes the cryptographic methods discussed in this chapter.
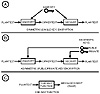
Figure 10.2 The three primary cryptographic techniques are symmetric cryptography, asymmetric cryptography, and one-way functions.
| Cryptographic Technique | Where Applied |
|---|---|
| Secret key symmetric cryptography | Use in environments where the single key can be easily exchanged, such as the same office. Also used to encrypt information for storage on disk. |
| Public key asymmetric cryptography | Primarily used on public networks such as the Internet where key exchange would normally be difficult. An enabling technology for digital certificates and signatures. |
| One-way functions | Digital signatures and certificates. Used to prove the authenticity of document contents. Often used in conjuntion with public key systems. |
Next, this chapter moves on to explain some of the terminology used in the world of cryptography. From there, you’ll learn how the different cryptographic techniques can be applied to private communications, electronic commerce, and information storage. Then the chapter moves on to a more technical discussion of the algorithms used in secret key and public key cryptography.
Following these topics is a discussion of cryptanalysis and methods of attack on popular encryption techniques.
Cryptography is the “art” of hiding and securing information for storage and transmission. The purpose of cryptography is to make information unreadable except by people who are authorized to see it. Note that the following discussion assumes that text is what most people are trying to hide, but any digital information including pictures, sound, and video can be encrypted. Following is a list of terms and definitions you’ll need to know for the discussion of cryptanalysis.
| Previous | Table of Contents | Next |