

|
|
| Previous | Table of Contents | Next |
Everybody knows that if you want to keep something private, you’ve got to hide it. To send a private message to a friend, you put it in a sealed envelope. But Secure Chif the message is really private, you’ll want to make sure that someone breaking the seal can’t read the enclosed message. In modern times, this feeling of security is even more important as the usage of e-mail and the Internet increases.The current security solution for such dilemmas is encryption. This chapter will provide you with a broad range of topics concerning cryptography. There are three main categories of encryption, as follows:
After discussing these three categories, the chapter will go on to discuss how cryptography is commonly used for storing and transporting information in electronic commerce and for legal purposes. Encryption algorithms are then discussed followed by a discussion of cryptanalysis, which is the practice of breaking encryption schemes.
Encryption is based on algorithms that scramble information into unreadable or non-discernable form. Decryption is the process of using the same algorithm to restore the scrambled information to its original form. The algorithm is a set of carefully devised procedures that must effectively produce an encrypted result that cannot be restored by someone, whether or not they have the original algorithm.
The algorithm can be quite simple. For example, you could devise an algorithm we’ll call character+3 in which A becomes D, B becomes E, C becomes F, and so on. It’s simple and useful for this example, but relatively easy to break. You wouldn’t want your government to use this technique to hide ballistic missile launch codes! Still, it illustrates the steps of encryption; the original message (called plaintext in crypto-speak) is converted by the character+3 algorithm into ciphertext (crypto-speak for the encrypted results). The algorithm to decrypt the message is the reverse function character-3.
A more common encryption method is to use an algorithm and a key. In the above example, you could change the algorithm to character+x, where x is a variable that serves as a key. So now you can tell all your friends that you use the character+x algorithm, but that you will use a different key with each message. One day the key might be 3 and the next day the key might be 9. The key must be kept separate from the encrypted message and sent to the recipient in secret. Because one key must be kept secret, this technique is often called symmetric (single key) or secret key cryptography. Most computerized cryptographic systems use common algorithms that are publicly available.
There is one big problem with using symmetric key encryption techniques; you need a safe and reliable way to get a copy of the key you used to encrypt the message to the recipient so the message can be decrypted.
Obviously, you can’t send the key with the original message. Anyone that intercepts it will then know how to break the code. If the person is a friend, you may have agreed on a key in advance, or you could just call them and tell them the key. But what if your phone is bugged? You could send the key in a separate envelope, but that envelope might be intercepted as well. Do you trust your delivery people?
Paranoid? Perhaps, but information that involves national security, company trade secrets, or financial information is a target for foreign agents, industrial spies, and thieves in general. They will do almost anything to get keys that will open encrypted messages.
To get around the secret key problem, a couple of security “experts” named Whitfield Diffie and Martin Hellman developed the concept of public-key cryptography. The scheme, also called asymmetric encryption, is quite simple in its basic concept, but revolutionary in its scope.
Note: The details of the RSA public key cryptosystem are explained later under Asymmetric (Public-Key) Cryptography. It should be mentioned that Diffie and Hellman developed the concept of public-key cryptography in 1976. However, an actual public key cryptosystem was developed in 1977 by Ron Rivest, Adi Shamir, and Leonard Adleman, all partners in RSA Data Security, now owned by Security Dynamics. RSA developed the algorithm for generating key pairs, making the technique commercially viable.
As shown in figure 10.1, each person gets a pair of keys—a private key and a public key—that are associated mathematically, but different in function. Here’s the “key” concept:
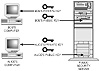
Figure 10.1 Public key cryptography uses two keys, one held privately and one made publicly available.
The private key is held in secret by the owner while the public key is given out by the owner or posted on a public key server where it is freely available. The U.S. Postal Service is providing public key distribution in the form of certificates (digital IDs) as discussed later. Organizations may have their own internal key distribution systems as well.
Here’s how it works. If I want to send you an encrypted message, I get a copy of your public key and use it to encrypt the message. When you receive the message, you decrypt it with your private key. Here’s another major point:
No private key ever needs to be transmitted or shared, so you no longer need to trust a communication channel or establish some relationship with the recipient in advance. In fact, you can safely send encrypted messages to people you’ve never met by first encrypting the messages with the recipient’s public key. The scheme can also be used to securely exchange business documents and perform electronic transactions, opening up the potential for secure global electronic commerce on the Internet.
| Previous | Table of Contents | Next |