

|
|
| Previous | Table of Contents | Next |
When you first think about using plug-gw with the TIS plug-gw application, the obvious question that comes to mind is “How do I configure things for authentication?” The trick is to remember which machine is actually performing the authentication. The firewall using plug-gw does no authentication. It merely accepts the incoming connection on the named port, and establishes a connection from itself to the named system on the same or different port.
To see this in operation, you can establish a telnet connection to the POP port. Consider the sample output shown here:
$ telnet 206.116.65.3 110 +OK UCB Pop server (version 2.1.2-R3) at 198.53.64.14 starting. USER chrish +OK Password required for chrish. PASS agdfer +OK chrish has 0 message(s) (0 octets). QUIT Connection closed by foreign host. $
Notice that the connection to the firewall was established at 206.116.65.3. The remote system [198.53.64.14] does not normally list its IP address in the output; a modified version of the POP server was used to show the IP instead of the name.
Unfortunately, simply adding the entries to the netperm-table file is not enough. Like NNTP, inetd must be configured to accept connections on the POP service port, 110. This is done by adding the following line to the /etc/inetd.conf file and restarting inetd:
pop stream tcp nowait root /usr/local/etc/plug-gw plug-gw 110
With the firewall now accepting POP service requests, plug-gw must be configured to redirect those POP requests to the appropriate server. This is done by adding this next line to the netperm-table file:
plug-gw: port 110 206.116.65.* -plug-to 198.53.64.14
After it is added, POP service requests received by the firewall are redirected to the specified server.
The preceding example shows the process of establishing a POP session using telnet, but how do you configure a workstation that relies on POP to pass traffic through the firewall? Figure 6.6 shows a configuration screen from the Eudora 1.52 shareware e-mail package:
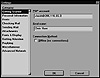
Figure 6.6 Setup for a POP e-mail package.
In this example, the user@hostname specification for the POP server identifies the real user name, but specifies the IP address for the firewall. The IP or name of the firewall can be used interchangeably in this field. The only reason for using the IP address rather than the name is if you have a DNS reliability problem, or to ensure that you connect to the correct host.
Consequently, when the incoming connection is received on port 110, plug-gw starts a session to the remote host specified in the plug-gw rule. This results in the mail being transferred from the remote end through the firewall to the workstation.
Incidentally, the POP mail client in use is irrelevant. The plug-gw configuration has been tested with Eudora, Microsoft Exchange, and Pegasus Mail; every package tested functions properly.
A set of support tools are included with the TIS Toolkit to assist in the setup and ongoing administration of the firewall. These include a port scanner, a network subnet ping manager, and log analysis and reporting tools.
Note: Depending upon the version and completeness of the Toolkit you downloaded, some services and programs may not be installed or compiled automatically. It is strongly suggested that you retrieve the latest version and patches directly from the TIS FTP site.
The portscan program attempts to connect to every TCP port on a given machine. The default operation is to connect to each port in sequence on the named host/. The portscan program’s scan of the machine pc.unilabs.org, for example, was answered by the following ports:
pc# ./portscan pc.unilabs.org ftp telnet gopher httpd pop nntp who 2021 2023 2120 7777 pc#
You can see from the output of portscan that very few ports are in fact in operation on the machine that was contacted.
This is a network ping program. It accepts as an argument a network address and starts to ping each address on the network. Its default output is a list of each of the addresses that responded to the ping, along with the host’s name. The use of netscan in default mode is shown in this example:
pc# ./netscan 198.53.32 198.53.32.5 Vaxxine-GW.Toronto.fonorola.net (198.53.32.6) 198.53.32.9 Harte-Lyne-gw.Toronto.fonorola.net (198.53.32.10) 198.53.32.13 Globe-n-Mail-GW.Toronto.fonorola.net (198.53.32.14) ^C pc#
This output shows that the first host that responded to a ping was 198.53.32.5. Notice that even though the program pings each address in turn, there is not always a response. This indicates that either no device exists, or netscan attempted to contact a device that does not respond to pings.
A verbose mode is also available with netscan. In verbose mode, addresses that respond to a ping are placed with their name or address flush left; addresses that did not respond are indented one tab space. This mode is enabled by using the -v option on the command line:
pc# ./netscan -v 198.53.32
trying subnet 198.53.32
198.53.32.1
198.53.32.2
198.53.32.3
198.53.32.4
198.53.32.5
Vaxxine-GW.Toronto.fonorola.net (198.53.32.6)
198.53.32.7
198.53.32.8
198.53.32.9
Harte-Lyne-gw.Toronto.fonorola.net (198.53.32.10)
198.53.32.11
198.53.32.12
198.53.32.13
^C
pc#
This tool helps determine what hosts are on a network, which may affect how you specify the configuration rules for your network.
| Previous | Table of Contents | Next |