

|
|
| Previous | Table of Contents | Next |
Incoming ftp connections can be logged under Windows NT, but only after changes have been made in the Registry. You can specify whether NT should log connections made by anonymous ftp users, by normal ftp users, or by both. These log entries can be viewed in the System Log by using the Event Viewer.
Warning: You can seriously disable Windows NT if you make incorrect changes to the Registry when using the Registry Editor. Windows NT provides no error warnings when you improperly change values with the Registry Editor. Exercise caution when using this utility.
To enable logging with ftp, perform the following tasks:
\SYSTEM\CurrentControlSet\Services\ftpsv\Parameters
The NT httpd service enables administrators to log access attempts to a specified file. The logging feature can be activated by selecting a check box on the httpd configuration utility, found in the Control Panel (see fig. 4.5). The httpd server adds entries to the Application Log and maintains its own logs in a filename specified during configuration.
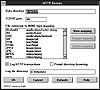
Figure 4.5 The NT HTTPD configuration dialog box.
Other NT-based applications that utilize the TCP/IP suite of protocols can provide the administrator with valuable auditing information. This section offers an overview of these applications.
SNMP
The Windows SNMP service can provide the administrator with useful traffic statistics from the local network, from the server itself, and from applications that use TCP/IP.
The application also can be configured to accept SNMP information from only certain IP addresses and to send traps for failed SNMP authentications. Only the administrator can configure SNMP options.
SQL Server
The SQL Server for NT automatically logs its transaction requests in the Application Log.
Systems Management Server
The Systems Management Server (SMS) product contains an application called Network Monitor that enables the administrator to monitor all TCP/IP traffic. Network Monitor is an ethernet sniffer program similar to Novell’s Lanalyzer product. You can configure it to record data based on protocol type, source address, and destination address. This utility can be a valuable tool in monitoring suspicious traffic both to and from the LAN.
Because access to the network in many installations comes from DOS-based workstations, administrators might want to begin tracking all usage from the moment end users turn on their PCs. In many cases, however, this tracking might be more work than is desired; maintaining logs on multiple machines requires a great deal of logistical planning on the part of the administrator.
A large number of PC-auditing packages are available on the market. Some are even available as shareware. These programs generally allow for multiple-user logins or multiple-security levels; device control, such as keyboard locking, serial port locking, and screen blanking; boot control; encryption; file access control; and audit trail features.
Mergent International’s PC/DACS product maintains logs pertaining to three types of events:
The session events logged include logins, logouts, user time-outs, and logins generated after system time-outs.
Operation events tracked include program executions (normal or TSRs); subdirectory creation and deletion; user additions and deletions; changes to access rules; COM and LPT port accesses; and file attributes.
Violations tracked include invalid user ids, invalid passwords, unauthorized attempts to write to COM and LPT ports, and unauthorized file and directory accesses or modification attempts.
PC/DACS enables the administrator to generate standard reports based on system events mentioned previously. It also has the option to extract various audit log information to a text file.
Fisher’s Watchdog product audits user command activity, directory accesses, program execution, date and time changes, and illegal and legal login attempts.
Audit trail reports can be displayed to the screen, printed, or saved to a file. The package has a report generator that enables the administrator to predefine multiple-report formats for later use.
Secure Computing’s LOCK, a shareware product, offers many of the same features as the commercial products. It enables user authentication; access control over files, directories, and ports; encryption; and audit trail features.
LOCK’s auditing features enable administrators to track command execution, invalid login or password entries, unauthorized file or directory access, and changes to any settings.
Because daily system upkeep and user support is so overwhelming at times, many administrators cannot undertake all the security-related duties they would like. When a system is properly configured to monitor and log user and network activity, however, discovering intrusion attempts is much easier.
By implementing a combination of logging utilities, such as process accounting and TCP wrappers (along with the regular verification of standard system logs), an administrator can almost certainly detect any suspicious activity.
| Previous | Table of Contents | Next |