

|
|
| Previous | Table of Contents | Next |
A plethora of monitoring and logging utilities have been written in recent years to help system administrators keep track of potential break-in attempts and other problems.
Many such utilities are available for free in various ftp archive sites on the Internet, and new ones are released continuously.
asax
The advanced security audit trail analyzer on Unix (asax) utility helps system administrators process and analyze data maintained in log files. Sorting through numerous large files of logged data can be extremely tiresome and difficult. asax is designed to remove some of that burden.
asax can be found at the following ftp site:
ftp.fc.net /pub/security/asax-1.0.t.gz
chklastlog and chkwtmp
chklastlog and chkwtmp analyze the lastlog and WTMP files to ensure that no entries have been deleted.
These two utilities can be found at the following ftp site:
ftp.fc.net /pub/security/chklastlog-1.0.tar.gz /pub/security/chkwtmp-1.0.t.gz
lsof
lsof lists all open files being used by running processes. Based on the files that the process accesses, this utility can clearly illustrate whether a particular process is actually benign or a disguised piece of malicious software.
The lsof utility can be found at the following ftp site:
ftp.uic.cc.purdue.edu/pub/tools/unix/lsof/lsof_3.02.tar.gz
netlog
netlog is an advanced sniffer package containing three utilities:
Administrators at Texas A&M University developed and implemented these programs.
The netlog package can be found at the following ftp site:
ftp.fc.net/pub/security/netlog-1.2.tar.gz
NFS watch
The NFS watch utility monitors NFS requests to specific machines or to all machines on the local network. Its main function is to monitor NFS client traffic, but it also logs reply traffic from NFS servers to measure traffic statistics, such as response times.
NFS watch can be found at the following ftp site:
ftp.fc.net /pub/security/nfswatch4.1.tar.gz
TCP wrapper
Wietse Venema’s TCP wrapper utility enables the administrator to easily monitor and filter incoming TCP traffic to network services such as systat, finger, ftp, telnet, rlogin, rsh, talk, and others.
This program can be found at the following ftp site:
ftp.cert.org /pub/tools/tcp_wrappers/tcp_wrappers_7.6.tar
tripwire
tripwire is a useful tool that measures all changes to a Unix file system. It keeps a database of inode information and logs of file and directory information based on a user-defined configuration file. Each time it is run, tripwire compares the stored values against flags set in the configuration file. If any deviations from the original value show up, the program alerts the administrator.
tripwire can be found at the following ftp site:
ftp.cert.org /pub/tools/tripwire/tripwire-1.2.tar.Z
Almost every transaction under Windows NT can be audited to some degree. Administrators, therefore, should choose carefully the actions they want to audit so as not to tie up system resources and needlessly fill up disk space.
Auditing can be turned on in two places under Windows NT—Explorer, and the User Manager. Under Explorer, choose Security and then Auditing to activate the Directory Auditing dialog box (see fig. 4.1). From this window, the administrator can select to track both valid and invalid file accesses.
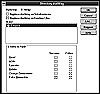
Figure 4.1 Configuring file-access auditing under Windows NT.
Under the User Manager, the administrator has the option to select audit policy based on the success and failure of several user events, such as login and logout, file access, rights violations, and shutdowns (see fig. 4.2).
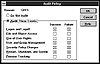
Figure 4.2 Setting user audit policy under Windows NT.
Windows NT stores its log files in a special format that can be read using the Event Viewer application. The Event Viewer is found in the Administrative Tools program group. The Event Viewer’s Filter option enables the administrator to select the log entries he or she wants to view based on criteria such as category, user, and message type (see fig. 4.3).
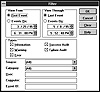
Figure 4.3 Selecting filter criteria under the Event Viewer.
The Event Viewer (see fig. 4.4) differentiates various types of messages by using small icons, each representing one of five distinct types of entries:
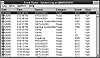
Figure 4.4 One of the three Windows NT auditing logs under NT Event Viewer.
Windows NT stores auditing information in three separate log files:
The Application Log contains information generated by applications registered with the NT Security Authority.
The Security Log contains information about system accesses through NT-recognized security providers and clients. Other events—such as illegal file accesses, invalid password entries, access to certain privileged objects, and account name or password changes—can be tracked as well if the administrator chooses to do so. Individual applications also can assign their own security events, which appear in both the Security Log and the Application Log.
The System Log contains information on all system-related events, some of which might also be in the Security Log, the Applications Log, or both. The System Log acts as a default storage file for much of the regularly generated Windows NT auditing information.
| Previous | Table of Contents | Next |