

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: Administrators
Under Windows NT, user groups are compilations of user accounts. Whenever a user account is added to a group, the user concerned receives all the rights and permissions which were granted to the group. In this way, designated users can easily be provided with common capabilities. If possible, the roles of employees should be reflected in groups and the access rights then allocated to these groups in accordance with their needs.
The use of groups, in place of the assignment of rights and permissions to individual users, makes administration easier, and, thanks to greater transparency, helps to increase system security. Groups should be formed even when there is a small number of employees. As a result, when there is an expansion, no fundamental restructuring of the rights structures has to be carried out.
Rights and permissions are additive. That means that for one user who is a member of several groups, the most extensive access right for a particular resource applies. However, there is an exception to this: If users are members of a group which has been given the access permission "No access" for a particular resource, then these users cannot access this resource, even if they are members of another group which has been granted the right "Full access" (see also S 4.53 Restrictive allocation of access rights to files and directories under Windows NT)
Example:
User Smith is member of groups "A" and "B". Group "A" has been granted the access permission "Read" the directory "Invoice", group "B" has been granted the access permission "Read and Write". User Smith has therefore the access permission "Read and Write" for the directory "Invoice".
The user group concept of Windows NT distinguishes between global and local groups.
Local groups
A group is called "local" if it can only be granted permissions and rights for the computer on which it was defined. On computers with the operating system Windows NT (i.e. both servers and workstations), which do not belong to a domain, all groups are local. In order to structure the allocation of rights and permissions, only this type of group is used on such computers.
If a computer under Windows NT belongs to a domain, local groups are also available. They can then contain user accounts from their own computer, global users, and global groups from their own domain or from trusted domains.
Local groups cannot receive permissions for resources of other domains. It is not possible for a local group to become a member of another local group. Local groups are represented in the User Manager by a group symbol with a computer.
Global groups
If a computer on which Windows NT is being run belongs to a domain, there is a further type of group for which access to the workstation can be made possible. This is the "global group", which can be used in several places: in its own domain, on servers, on workstations of the domain and in trusted domains. If a workstation belongs to a domain, it means that permissions and rights to the local workstation and membership of local groups of the workstation, can be granted to the global groups of the domain and the trusted domains. A global group can only contain user accounts from its own domain.
Global groups can only be defined on the primary domain controller. It is not possible for other groups to become members of a global group. Global groups are represented in the User Manager by a group symbol with a globe.
To sum it up, it is recommended to structure the system administration as follows:
Rights and permissions are assigned to local groups. Users become members of global groups and the global groups become members of local groups.
In addition to the distinction between local and global groups, there is also a distinction between pre-defined user groups, special groups and freely-defined user groups.
Pre-defined user groups
The actions a user can perform depend on the group memberships of his user account. Several groups are pre-defined in Windows NT and each group is granted a particular set of user rights as standard. Where required, additional groups can be created and defined via the User Manager. With these groups, access to individually-compiled resources is made possible for the users assigned to them.
In addition to the rights, pre-defined functions are allocated to some of the pre-defined local groups. Rights and access permissions can be granted directly to the groups and user accounts and withdrawn from them. On the other hand, the pre-defined functions cannot be administrated directly. Pre-defined functions can only be provided for a user if the user is made member of a suitable local group.
On computers which are configured with the operating system Windows NT as member server (a server which does not have the function of a domain controller) or as a workstation, the following local groups are set up during installation by default.
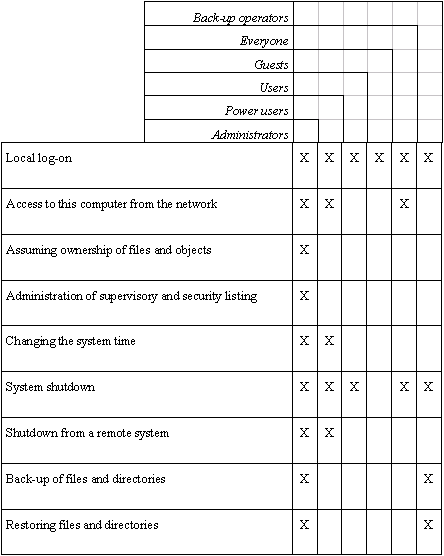
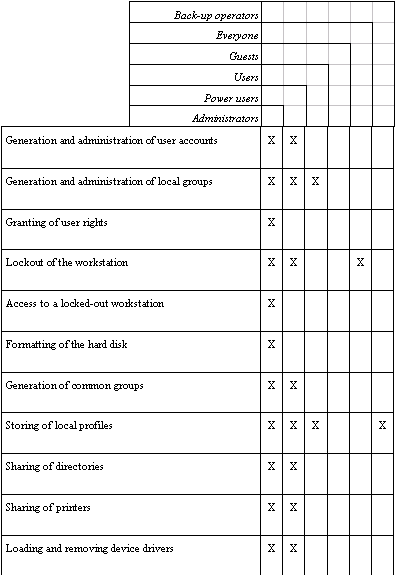
Under Windows NT, on workstations and servers which are not configured as domain controllers, the rights and functions which are granted to designated, pre-defined local groups are listed in the following table:
On servers which are configured as domain controllers under the operating system Windows NT, the following local groups are set up during installation by default.
In this configuration, the following global groups are also created during installation:
The rights and functions which are granted under Windows NT on domain controllers to designated, pre-defined local groups, are detailed in the following table:
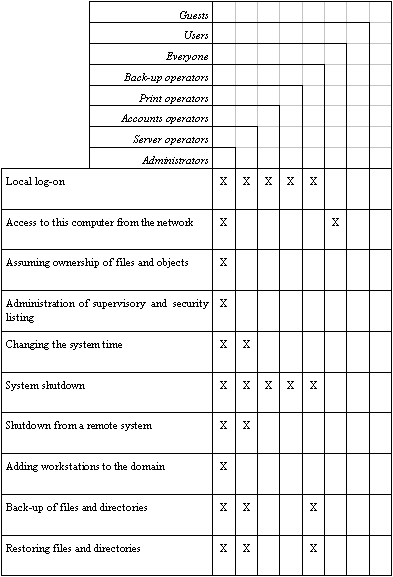
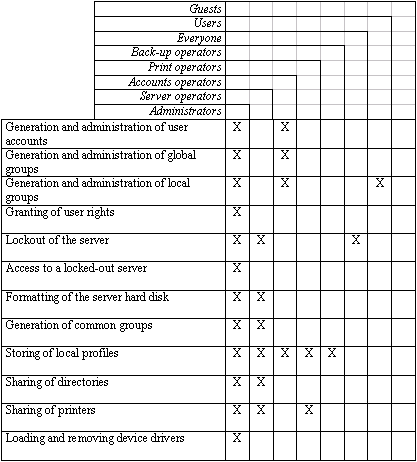
Note: The rights outlined above, which are allocated under Windows NT as standard, must all be reviewed separately with a view to determining whether they are compatible with the security strategy laid down (see S 2.91 Determining a security strategy for the Windows NT client-server network). Thus, for example, the right "Access to this computer from the network" should be withdrawn from the group "Everyone". Whether it is granted alternatively to the group "Users" must be clarified in detail.
The following pre-defined groups are available under Windows NT:
However, power users cannot change or delete the groups "Administrators", "Domain admins", "Accounts operators", "Back-up operators", "Print operators" and "Server operators", neither can they change or delete any administrators' user accounts.
Note: This group should be used to define sub-system administrators who relieve system administrators of the burden of certain routine tasks, especially in connection with the administration of user accounts without, however, receiving full control over the system.
Note: All users who do not require any extended rights should usually only belong to this pre-defined group and to suitable freely-defined groups which reflect the organisational structure. Allocations to other pre-defined groups should only be made in justified individual cases. This also means that users should not receive any administrator rights on their workstation computers.
Note: If possible, no further user accounts should belong to this group apart from the pre-defined guest account, and the pre-defined guest account should be locked out (see S 4.55 Secure Installation of Windows NT). As an additional precaution it should be provided with a password to prevent unauthorised access in case it is unlocked for a short time.
Note: Data back-ups and the recovery of saved data should be carried out by a member of this group. For this it is not necessary to use an administrator account.
Note: The administration of printers should be carried out by members of this group in order to avoid the unnecessary use of administrator accounts.
Note: Routine tasks involved in controlling the domain controllers should be carried out by members of this group, insofar as they can be carried out with the rights of this group. Only tasks which require full control over the system should be carried out from administrator accounts.
Note: No users accounts should be added to this group, and the user account present there should not have the rights "Local log-on" and "Access to this computer of the network".
Special groups
In addition to the above-mentioned pre-defined groups, Windows NT creates a number of special, internal groups which are not listed by User Manager. In a good many cases, however, they are listed in the group list, for example when permissions are assigned to directories, files, released network directories or printers.
Freely-defined user groups
With the help of freely-defined user groups, it is possible to map the organisational structure of an institution to the rights structure. For each organisational unit, e.g. for every project or every department, a group can be created which contains all the users of the organisational unit. The groups are then granted the necessary permissions to resources. If project groups are created within the institution for temporary tasks, they can be mapped to a suitable freely-defined group which contains all the members of the project group.
When freely-defined user groups are created on the primary domain controller, it must be specified whether they are local or global groups.
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |