

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: Administrators
Under Windows NT, a distinction is made between access rights at the share level, and access rights at the file and directory level, termed NTFS rights in the following. Access rights at the share level are described in S 2.94 Sharing of directories under Windows NT.
As opposed to share rights, access rights at the file and directory level are only available on data media with the NTFS file system. As a rule, these rights are assigned by the creator or owner of an object (directory or file). On servers, this is usually done by the administrator. Under Windows NT 4.0, NTFS permissions are granted typically using the Windows NT Explorer or "My Computer" desktop symbol. The menu item designated "Attributes / Security" is to be selected in the context menu of the related directory or file. The following access control list is then invoked:
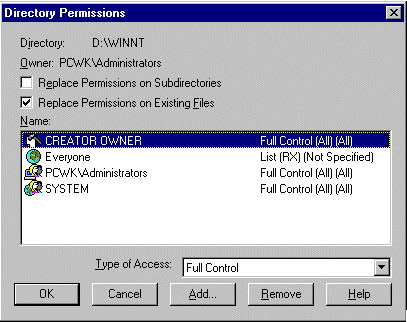
Under Windows NT 3.51, the access control list is to be found under "Security / Authorisations" in the File Manager. Existing user groups and users can be added to this list; furthermore, rights can be granted to, and withdrawn from, every user group and user here. It is also possible to remove user groups and users from the access control list. By activating the option labelled "Replace permissions on existing files", the rights specified for the directory can be transferred to all the files located therein. If the option labelled "Replace permissions on subdirectories" is selected, the specified rights are also transferred to all subdirectories. This allows easy realisation of standard permission profiles.
NTFS permissions initially become effective during local access. For example, if several users need to work on a computer, file and directory access rights can be granted appropriately to ensure that each user only has access to the data intended for him/her.
NTFS permissions also become effective during access via the network. However, a prerequisite for access via a network is that the directory which needs to be accessed or which contains the required subdirectory or file must be shared and assigned a corresponding share permission beforehand (refer to S 2.94 Sharing of directories under Windows NT). During the interplay between share permissions and NTFS permissions, it must be noted that the more restrictive permission is conclusive in each case. NTFS permissions can be graded more finely than share permissions. In particular, it is possible to assign separate NTFS permissions for each subdirectory and file. Consequently, it is also possible to assign shares with the "full access" share permission for the user groups and domain users, and allocate the effective access rights via the NTFS permissions.
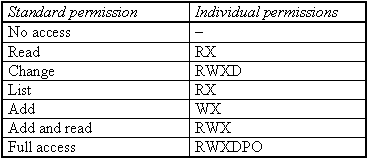
NTFS permissions are classified as specific (or individual) permissions or predefined, standard permissions which constitute combinations of the specific access permissions.
The following individual permissions are possible:
From these individual permissions, default standard permissions have been combined under Windows NT.
Every owner of a file or directory has the right to grant and withdraw permissions for that file or directory. Every user who creates a file or directory automatically assumes ownership of this resource. Ownership of a file or directory can be transferred by means of the "Transfer ownership" option (O) to other users. However, this ownership only becomes effective once it has actually been obtained by the recipient. In contrast to other operating systems, it is not possible to give away files and directories. Irrespective of the entries in the access control list, administrators can assume ownership of any file or directory.
Note:
The safeguards mentioned in the following sections apply mainly to files and directories for which the administrator is responsible, i.e. to those which are either important for all users or useful for administration purposes. It is not sufficient to check the rights of one program. The rights allocation of all programs which are called up from this program must also be checked (in particular to avoid Trojan horses).
The attributes of all system files should, as far as possible, be set in such a way that only the system administrator has access to them. Directories should provide no more than the required privileges for users.
Directories of the operating system and the application programs
The files and directories of the operating system itself must be adequately protected against illicit accesses. Immediately following installation of the system, the standard access rights specified should be adjusted to more restrictive forms of access control for the relevant files and directories (the Windows directory, %SystemRoot%, e.g.\WINNT, the Windows system directory %SystemRoot%\SYSTEM32and any further program directories, e.g. \MsOffice and\Programs, and all sub-directories).
At this point, however, it should be noted that quite a number of programs, particularly 16-bit programs but also MS Winword 7.0, create initialisation and configuration files in the Windows directory and/or in the program directory. If such programs are to be used it can become necessary to give users the access right "Change" for the relevant directories and files.
Only administrators should have write access to these directories. All other users should only have read and execute permissions (RX).
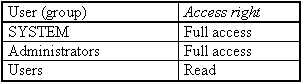
Where necessary, access to executable files (.EXE, .COM and .BAT) can be restricted still further, so that only executable (X) access to these files is possible. In a similar manner, the files which are of critical importance in starting the system, namely\BOOT.INI, \NTDETECT.COM, \NTLDR, \AUTOEXEC.BAT and \CONFIG.SYS, must be protected against unauthorised amendment by non-privileged users.
However, checks should also be carried out - preferably in a test environment - to determine whether all application programs are still able to run with this restrictive setting, or whether individual access controls still have to be supplemented by further access capabilities, in order to permit, for example, the storage of temporary files or configuration information in a program directory. Generally, however, access to the program files themselves (.EXE-files) and to dynamic libraries (.DLL-files) for the group "Everyone" should be restricted to read access, especially as this safeguard also offers a certain protection against the spread of viruses.
Temporary files
Temporary files, which are used by various application programs for the relocation and intermediate storage of data, are filed under Windows NT in the directory %TEMP% (usually C:\TEMP). All users also need the right to store files in this directory, but, at the same time, users must be prevented from gaining access to temporary files of other users. The access rights for the directory should therefore be changed to the following value:
Registration
The registry of Windows NT is located in the sub-directory CONFIG of the Windows system directory%SystemRoot%\SYSTEM32, i. e. in general in the directory C:\WINNT\SYSTEM32\CONFIG. The user must have access to this directory, as the registry is automatically changed by settings of the user in application programs. If the user cannot access this directory, it leads to system errors or to the crashing of the system. Under version 3.51, the standard rights set for this directory, which, as far as possible, should not be amended, are:
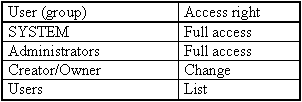
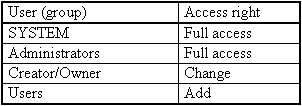
As from version 4.0, the standard rights are:
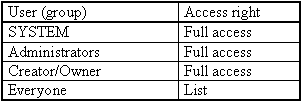
However, the group titled "Everyone" should be replaced by the group titled "Users". Only if guests have access to this directory, should the group titled "Everyone" be assigned the permission titled "List".
During installation, Windows NT creates the directory %SystemRoot\REPAIR for the purpose of storing configuration information which might be required for repairing an existing installation. These files are updated with the help of the RDISK utility program (also refer to S 6.42 Creating start-up disks for Windows NT). As these files, together with disruptive software, can be used to disable the security features of Windows NT, rights to access this directory and all the files contained therein should be set as follows:

Profiles
In order to store the data which the user interface and entries in the START menu describe from version 4.0 onwards, Windows NT creates a personal profile directory for each user of the system in the sub-directory Profiles of the Windows directory %SystemRoot% (generally C:\WINNT\PROFILE). Under version 3.51, profiles are stored in sub-directories of the system directory %SystemRoot%\SYSTEM32\CONFIG or in directories explicitly specified for individual users.
The user must have full access to these directories provided that he is supposed to be able to alter his user interface himself. However, this is not always desired (cf. S 4.51 User profiles to restrict the usage capabilities of Windows NT). When the user first logs on, his user profile is automatically generated by the system. The standard access rights for the directory appear as follows:
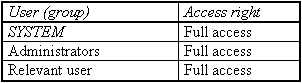
Besides the profile directory for the individual user there is a further directory for all users ( All Users) and a directory as a model for new users ( Default User). Only system administrators should have write access to these directories. Access rights should be set as follows:
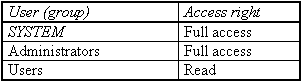
These settings should only be altered if you wish to take away the user's right to alter his user interface.
User directories
The directories for the data of individual users should, in general, be protected in such a way that only the users concerned can access their files. Other users, even administrators, do not in general require access to the data of a user, unless the latter explicitly allocates additional access rights himself. Accordingly, in most cases the following pre-setting is adequate for access rights to user directories:

Users who want to make individual files or directories accessible to other users, should set up directories outside their base directory for this purpose. Likewise, special directories should be set up for project groups working jointly on designated files. Again, access rights to such directories should also be explicitly limited to the users in these groups.
Lockout of access rights for guests
The access control lists described above are based on the assumption that no users of the group titled "Guests" group are to be authorised. For this reason, the group titled " Everyone " should be replaced by the group titled " Users ". This safeguard effectively deprives guests of any possibility of working with the system and of accessing data. However, as this may possibly lead to a situation in which certain application software no longer runs correctly, any change of this sort should first be made on a test system and scrutinised in terms of its effects before being implemented generally.
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |