Securing-Optimizing-RH-Linux-1_2_237
Comments and suggestions concerning this book should be mailed to gmourani@videotron.ca
© Copyright 1999-2000 Gerhard Mourani and Open Network Architecture ®
237
NOTE: The “named” binary program must be in a directory listed in your PATH environmental
variable for this to work. For the rest of the documentation, I'll assume the path of your original
named program is “/usr/sbin/named”.
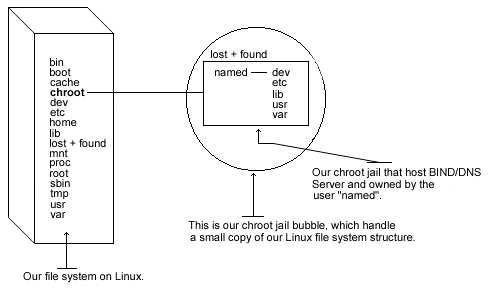
The following are the necessary steps to run BIND/DNS software in a chroot jail:
Step 1
We must find the shared library dependencies of named (named is the DNS daemon). These will
need to be copied into the chroot jail later.
·
To find the shared library dependencies of named, execute the following command:
[root@deep /]# ldd /usr/sbin/named
libc.so.6 => /lib/libc.so.6 (0x40017000)
/lib/ld-linux.so.2 => /lib/ld-linux.so.2 (0x40000000)
Make a note of the files listed above; you will need these later in our steps.
Step 2
Add a new UID and a new GID for running the daemon “named”. This is important because
running it as root defeats the purpose of the jail, and using a different user id that already exists
on the system can allow your services to access each others' resources.
Check the “/etc/passwd” and “/etc/group” files for a free UID/GID number available. In our
example we'll use the number “53” and the name “named”.
[root@deep /]# groupadd -g 53 named
[root@deep /]# useradd -g 53 -u 53 named
Step 3
Now we must set up the chroot environment, and create the root directory of the jail. We've
chosen “/chroot/named” because we want to put this on its own separate file system to prevent