Threats against enterprises are wide and varied,
including all manner of attack, such as outsider penetration, insider abuse
of privilege, and denial of service from poorly trained users.
Windows NT is vulnerable to many threats, as I
discussed in my last column ["NT Vulnerabilities," November 1998,
p. 23]. There are many things you can do, both organizationally and technically,
however, to protect yourself from attack. This is known as "hardening"
a system, and it can be very effective for repelling hackers and deterring
misuse.
Hardening is accomplished through establishing
security procedures, correct system configuration, physical security, and
the addition of third-party products. Each type of hardening protects against
a class of risk. Hardening can be a selective process that reduces the amount
of work necessary for effective protection. Remember, all threats are not
relevant to all computers or all organizations. You can save your company
time and money by protecting your network from relevant risks instead of
all risks.
Windows NT Configuration
The most obvious and well-known hardening technique
is to configure your Windows NT system properly. This is a multiple-step
process that covers password policies, account policies, Registry configuration,
networking configuration, and a list of miscellaneous items that don't fit
well into any specific category.
Password Policies
Guessing passwords is still an effective way to
break into systems, and password theft is a major problem. Password policies
force users to select good passwords and to change them often, which makes
it more difficult to penetrate a computer from the outside. The following
recommendations will harden your system against someone who tries to guess
or steal passwords:
- Maximum password age: 90 days. This forces users
to change their passwords every 90 days. A longer time period opens a large
window in which successfully broken or stolen passwords can be used before
being changed. A shorter time period may annoy your users and cause rebellion.
- Minimum password age: one day. Minimum password
age prevents users from changing their password and immediately changing
it back to the old password, effectively eliminating the requirement to
change passwords.
- Minimum password length: eight characters. Longer
passwords take longer to break and guess.
- Password uniqueness: five passwords. This is
the number of remembered passwords for each user. Users can't reuse a password
until they have used five different new passwords. If the minimum password
age is one day, it would take users five days of changing their password
every day before they could reuse a password. This is intended to discourage
the use of repeat passwords, and it is very effective.
- Account lockout: lockout after five failed attempts;
reset count after ten minutes. This simply reduces the number of tries
that a brute-force password-guessing attack can make over a given period
of time. Account lockouts can be detected and tracked to indicate a brute-force
password-guessing attack.
- Lockout duration: 15 minutes. Remember, you are
just trying to discourage the guessing attack, and an employee will be
idle during this time. Selecting the reset to forever will force an administrator
to unlock the account. This is not recommended and is probably overkill.
The costs really mount up when you consider an idle employee and the time
of the administrator who must unlock the account.
Account Policies
Windows NT has some special accounts that should
be secured. The most important of these, of course, is the Administrator
account. The following procedures will harden your system against attacks
on the Administrator and other accounts:
- Rename the Administrator account and establish
a decoy. By renaming the Administrator account you will frustrate outside
attackers who are after the most privileged account in the system. To further
frustrate them, create a decoy account named Administrator that has no
privilege. Set full auditing on the decoy account, and if you have a third-party
monitoring tool, set it to page you when this account is accessed.
- Replace the Everyone group with the Authenticated
Users group on every network share and common-use directory. The Everyone
group allows even unauthenticated users on the network to access resources
with this access control designation.
- Disable the Guest account. The Guest account
is required by some third-party applications, but it should be disabled
if it is not required. The Guest account has traditionally been used as
a shared account for temporary users such as partners, suppliers, and contractors.
The use of shared accounts results in a complete loss of accountability.
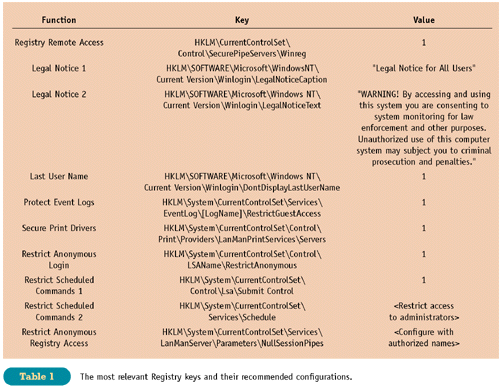
The Registry
The Registry controls how Win-dows NT is configured.
A number of Registry keys are relevant to security and must be configured
with care. The following procedures involve Registry entries and will harden
your system against myriad threats. See Table 1 for the actual keys and
recommended values.
- Control remote access to the Registry. Microsoft
provides the ability to administer the Registry from a remote location.
This is the single largest security hole in NT and one of the first holes
sought by any hacker.
- Set a legal notice. The legal notice is required
to warn potential attackers that they can and will be prosecuted for misuse
of the computer system.
- Prevent the last logged-in user name from being
displayed. When you press Ctrl-Alt-Del, a login dialog box appears that,
more often than not, displays the name of the last user who logged in to
the computer. This makes it easy to discover a user name for a password-guessing
attack.
- Protect the security event log. The event log
files are not protected by default. Permissions should be set on the event
log files to allow access to Administrator and System accounts only. Access
by the Guest account should be restricted through the use of a Registry
key.
- Secure print drivers. Restricting control of
print drivers to administrators and print operators reduces the risk of
unauthorized printing. This is particularly important if the printer contains
sensitive documents, such as blank checks or invoices.
- Restrict anonymous logins. NT allows anonymous
connections to list account names. Setting this Registry key restricts
this capability.
- Restrict scheduling commands. Administrative
privileges may be requested by users with the AT command. Access should
be restricted to administrators only.
- Restrict anonymous Registry access. Restricting
anonymous (null session) logins to specific named pipes is another important
way of restricting remote access to the Registry.
Networking
The network is the hacker's way into your system.
If your network is not securely configured, a hacker can move freely between
the systems on your network and find weaknesses in other aspects of your
security. Good network security is the first (but not the only) line of
defense you have against outsiders breaking into your systems. The following
procedures will harden your system against a network hacker:
- Turn off the following services if they are not
needed: FTP, RAS, IP Forwarding, and GOPHER.
- Disable protocols that are not needed, including
TCP/IP, NetBIOS, and NetBEUI.
- Disable Server, Alerter, and Messenger services.
- Block RPC port 135 at your firewall.
- Block nbname port 137 at your firewall.
- Block nbdatagram port 138 at your firewall.
- Block nbsession port 139 at your firewall.
Miscellaneous
Here are a few other important points regarding
configuration that you should consider:
- Install the latest service packs and hot fixes.
Microsoft regularly updates Windows NT security features in hot fixes and
service packs. While this process has also been known to introduce holes,
it is still recommended that you install the latest software.
- Remove ROLLBACK.EXE. This application was mistakenly
distributed by Microsoft and can destroy essential system files.
- Disable floppy and CD-ROM drives on crucial servers.
- Use NTFS only. File Allocation Table (FAT) file
systems do not have security or access controls. These necessary components
of security are provided only through NTFS.
- Set Access Control Lists (ACLs) on essential
files to allow access to authorized individuals only. The best security
mechanisms available are worthless if they are not used. The ACL capability
is typically not used to its fullest potential.
Procedural
The weakest link in any security plan is people.
There are many good mechanisms for protecting computers that are not used,
simply because of a lack of policy, process, and procedure. ACLs in NTFS
are an excellent example. All users on the system have the ability to protect
their files using ACLs, but in most environments the vast majority aren't
even aware of their existence, or if they are aware, they may not know how
to use ACLs properly. A good training and security-awareness program is
crucial to good security. The following procedures will harden your users,
which will ultimately harden your NT systems against all forms of attack:
- Limit the use of internal modems and absolutely
confirm that they are not set to auto-answer.
- Require people to enable a locking screen saver
to prevent security breach incidents when they leave their desks for extended
periods while still logged in.
- Create two accounts for administrators, so that
they have one account without privileges for reading their mail and doing
everyday work and another with privileges for handling NT administrative
tasks.
- Restrict execution of programs downloaded from
the Internet to keep viruses from infecting your system.
- Institute a backup procedure in which your organization
does a full backup at least once a week.
Physical Security
Physical security has two aspects: theft of computers
(including their local information) and misuse threats associated with physical
access. Information typically has a greater value than the computer on which
it resides.
Good facility security is always important, but
you should also consider training your executives who carry laptops about
the value of information and instituting a property-pass program for equipment
entering and leaving your facility. In addition, servers should always be
placed in a secure location to prevent physical access.
Third-Party Products
Windows NT security and procedures are not comprehensive
enough to provide total protection. A number of third-party products provide
services that are important for protecting your business. The following
families of products should be considered when creating a security plan:
- Authentication. Windows NT 5.0 will contain Kerberos
authentication, but until you have NT 5.0 rolled out to your entire enterprise,
you may want to consider products such as Entrust Public-Key Infrastructure
software from Entrust Technologies (www.entrust.com) to harden authentication.
- Encryption. Sending sensitive data over the wires
and maintaining it in clear text isn't a necessary risk anymore. A number
of encryption products on the market provide virtual private networks (VPN),
e-mail encryption, and file encryption.
- Monitoring. Once you've set up your security
configuration, be sure to monitor its compliance, detect intrusions, discover
the suspicious behavior of insiders, and perform damage assessment with
information risk-management tool sets from third-party vendors.
- Antivirus programs and firewalls. Although available
in commercial products, these two capabilities are being absorbed into
the operat-ing system, but they aren't completely effective yet. There
are a number of excellent third-party vendors for both services.
Conclusions
Windows NT does not arrive completely secure when
it is installed out of the box. It takes effort to configure it and use
it securely. The information I have provided in this article is far from
complete, and I strongly recommend that you follow up with other sources.
The best advice I can give you is to determine
what level of hardening is required for your organization and write it down.
Then put the title "Security Policy" on the document, and your
organization will already be light-years ahead of most other organizations.
Security policy will be the subject of my next column.
Paul E. Proctor has worked in computer security
on many varieties of Unix and NT systems for more than 12 years. He is chief
technology officer at Centrax Corp. in San Diego, California. You can contact
him at proctor@centraxcorp.com. |

