
nt-part2_70

 Analysis of the Security of Windows NT
1 March 1999
70
8.4 Summary
When we summarize the comparison above we see that all weaknesses in NT have
their counterpart in UNIX with the following exceptions:
• 8.3.3 Undocumented system variables and functions
• 8.3.4 SMB challenge response
• 8.3.6 Non NTFS file systems
The two last ones, (8.3.4) and (8.3.5), fall within the area of specific system design, for
which there is no direct counterpart with any feature of the design of UNIX.
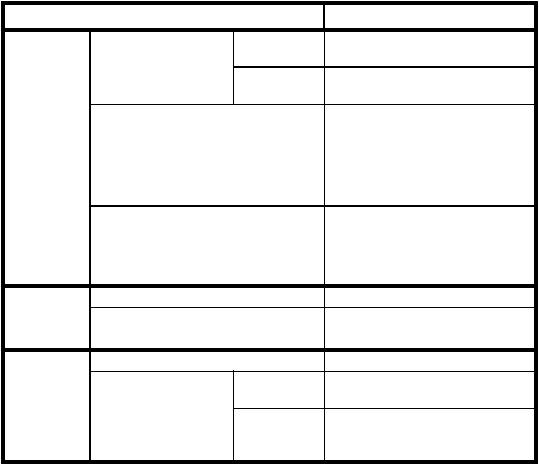
A classification corresponding to that of Table 5 in section 7.8 is found in Table 6. By
comparing the two tables we can see that it has been possible to find a UNIX counter-
part to all NT categories.
The similarities between UNIX and NT demonstrated above support the hypothesis
that the security behavior of the two operating systems is very similar.
TABLE 6. Classification of UNIX weaknesses
Category
Weakness
NP5
Bypassing
Intended
Controls
Password attacks
Capture
Plain-text passwords over the net-
work 8.3.6
Guessing
Password cracking via the network
(L0phtCrack) 8.3.17
Spoofing privileged programs
Failed parameter checks on critical
system calls 8.3.3
NTCrash 8.3.10
Teardrop 8.3.9
GetAdmin 8.3.15
Utilizing weak authentication
NTFSDOS 8.3.13
ERD-Commander/NTRecover/
NTLocksmith 8.3.14
RedButton 8.3.12
NP6 Active
misuse of
resources
Exploiting inadvertent write permissions
Installation Problems 8.3.1
Resource exhaustion
CPUHog 8.3.11
Teardrop2 8.3.9
NP7 Passive
misuse of
resources
Manual Browsing
Automated searching
Using a per-
sonal tool
Using a pub-
liclyavailable
tool
Analysis of the Security of Windows NT
1 March 1999
70
8.4 Summary
When we summarize the comparison above we see that all weaknesses in NT have
their counterpart in UNIX with the following exceptions:
• 8.3.3 Undocumented system variables and functions
• 8.3.4 SMB challenge response
• 8.3.6 Non NTFS file systems
The two last ones, (8.3.4) and (8.3.5), fall within the area of specific system design, for
which there is no direct counterpart with any feature of the design of UNIX.
A classification corresponding to that of Table 5 in section 7.8 is found in Table 6. By
comparing the two tables we can see that it has been possible to find a UNIX counter-
part to all NT categories.
The similarities between UNIX and NT demonstrated above support the hypothesis
that the security behavior of the two operating systems is very similar.
TABLE 6. Classification of UNIX weaknesses
Category
Weakness
NP5
Bypassing
Intended
Controls
Password attacks
Capture
Plain-text passwords over the net-
work 8.3.6
Guessing
Password cracking via the network
(L0phtCrack) 8.3.17
Spoofing privileged programs
Failed parameter checks on critical
system calls 8.3.3
NTCrash 8.3.10
Teardrop 8.3.9
GetAdmin 8.3.15
Utilizing weak authentication
NTFSDOS 8.3.13
ERD-Commander/NTRecover/
NTLocksmith 8.3.14
RedButton 8.3.12
NP6 Active
misuse of
resources
Exploiting inadvertent write permissions
Installation Problems 8.3.1
Resource exhaustion
CPUHog 8.3.11
Teardrop2 8.3.9
NP7 Passive
misuse of
resources
Manual Browsing
Automated searching
Using a per-
sonal tool
Using a pub-
liclyavailable
tool


