
nt-part2_36

 Analysis of the Security of Windows NT
1 March 1999
36
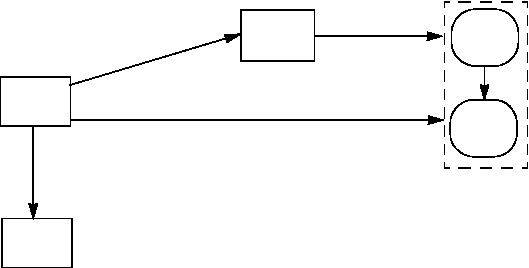
FIGURE 12. Schematic view of the login procedure: step 1 (Numbers state chain of events)
When a user presses the Ctrl-Alt-Delete key combination (called the Secure Attention
Sequence (SAS)) WinLogon initiates the identification and authentication process and
brings up a secure Desktop that prompts for username and password, see Figure 13.
The password is collected by Win32 which encrypts the password with an internal
encryption, later decrypts it and passes the password to WinLogon, see Figure 14.
When WinLogon receives the username and the password it collects the domain of the
user, creates a unique logon SID, creates and suspends a new process, and calls LSA,
see Figure 15.
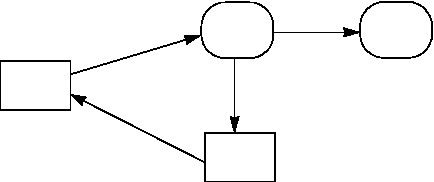
FIGURE 13. Schematic view of the login procedure: step 2 (Numbers state chain of events)
1. Reg
ister as
Logon
Process
2. Creates Window Sta-
tion and Logon Desktop
(Secure Desktop)
3.Change ACL
Win
Logon
Win32
LSA
4. Register as Logon Process
Window
Station
Logon
Desktop
1.SAS pressed
2.
SA
S
p
re
s
se
d
3. Acti
vate
Logon
Deskto
p
Win
Logon
Win32
Window
Station
Logon
Desktop
Analysis of the Security of Windows NT
1 March 1999
36
FIGURE 12. Schematic view of the login procedure: step 1 (Numbers state chain of events)
When a user presses the Ctrl-Alt-Delete key combination (called the Secure Attention
Sequence (SAS)) WinLogon initiates the identification and authentication process and
brings up a secure Desktop that prompts for username and password, see Figure 13.
The password is collected by Win32 which encrypts the password with an internal
encryption, later decrypts it and passes the password to WinLogon, see Figure 14.
When WinLogon receives the username and the password it collects the domain of the
user, creates a unique logon SID, creates and suspends a new process, and calls LSA,
see Figure 15.
FIGURE 13. Schematic view of the login procedure: step 2 (Numbers state chain of events)
1. Reg
ister as
Logon
Process
2. Creates Window Sta-
tion and Logon Desktop
(Secure Desktop)
3.Change ACL
Win
Logon
Win32
LSA
4. Register as Logon Process
Window
Station
Logon
Desktop
1.SAS pressed
2.
SA
S
p
re
s
se
d
3. Acti
vate
Logon
Deskto
p
Win
Logon
Win32
Window
Station
Logon
Desktop



