index_19
Auerbach Publications
© 2001 CRC Press LLC
08/01
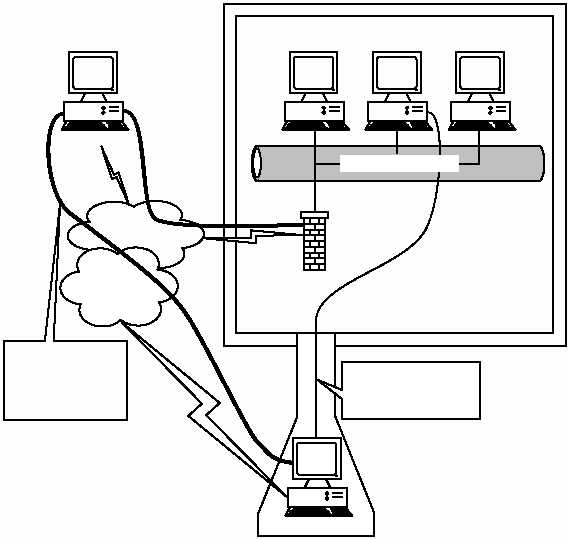
From the point of view of the attacker, the information is simply on
the Internet as is the corporate connection; therefore, the access process
and medium have not changed, just the level of security. The result is
that the information is presented to the attacker, and direct access
through a much more complicated path is not required. If it were not for
the Internet connection, the remote hosts would have increased func-
tionality, speed, and protection compared with legacy remote access
with modems. Regrettably, the Internet is the link to the extended func-
tionality as well as the link to ultimate insecurity.
Logically, this is a disaster for information security. We have invested
monumental amounts of time, research, and money into the evolution of
security and the mitigation of risk associated with connecting to a global,
unrestricted network. We have built massive walls of security with bricks
of technology ranging from basic router filtering, firewalls, and intrusion
detection systems to system hardening, DMZs, and air-gaps. Now that we
have a plethora of defense mechanisms pointed at the Internet, we are
EXHIBIT 7 — Attacker Obtains Data From a Much Less Protected Point
on the Internet
Internet
Firewall
Remote User
Established Security Envelope
Attacker
Phone
Cable
xDSL
Data is Accessed
or Copied from
Protected Network
Attack against
an Unprotected
System on the
Internet
Internet Network