index_18
Auerbach Publications
© 2001 CRC Press LLC
08/01
created by the security measures. Therefore, to get to the information, an
attacker would have to penetrate, circumvent, or otherwise manipulate
operational conditions to obtain the data or the means to access if more
directly (see Exhibit 6).
With the advent of VPNs, the remote system is permitted a protected
connection with the corporate data, inside the enclave of known risks
and threats. It is assumed that the VPN protects the communication and
stretches the security outward from the corporate to the remote location.
Unfortunately, this assumption has overlooked an essential component
of VPNs — the Internet. Now, as shown in Exhibit 7, an attacker can ac-
cess corporate data on a system completely exposed and in control of a
common user — not under the protection of technology or experience
found at the corporate site.
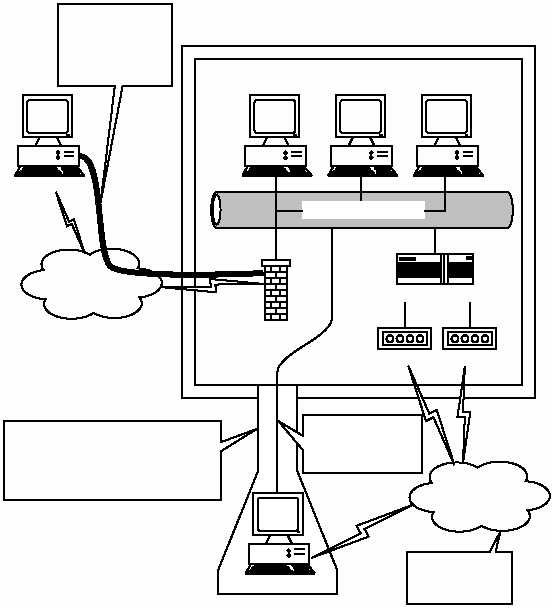
EXHIBIT 6 — Attacker Must Attempt Access to Corporate Data Directly,
the Most Difficult Path
Internet Network
Modem
Phone
System
Internet
Access Device
Modem
Firewall
Remote User
Established Security Envelope
Attacker
Internet-Based
Attacks on
Corporate
Information
Extended Security Envelope
(Reduced Slightly)
Added Risk Associated with
Connection at Corporate Site
Access to
Internal Network
and Data
Isolated
Point-to-Point
Connection