index_12
Auerbach Publications
© 2001 CRC Press LLC
08/01
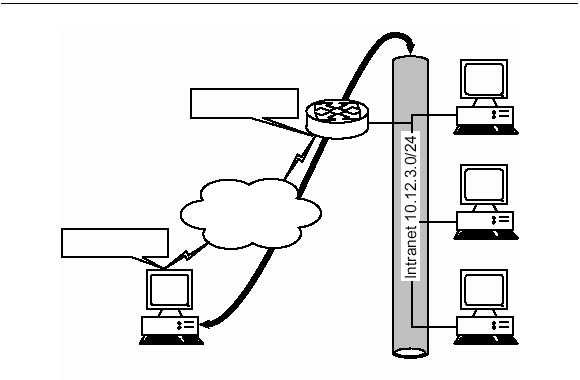
were no intermediary. An example, shown in Exhibit 5, is a remote sys-
tem that creates a datagram that would operate normally on the internal
network; instead, it is encapsulated and forwarded over the Internet to a
system at the corporate office that de-encapsulates (and decrypts if nec-
essary) the original datagram and releases it onto the internal network.
The applications and end systems involved are typically never the wiser.
The goal for some VPN implementations is to provide communica-
tions for remote users over the Internet that emulate intranet services as
closely as possible. Many VPN solutions are critiqued based on the capa-
bilities to allow services to the client systems that are usually only avail-
able internally. With the adoption of broadband Internet access there is
less stress on pure utilitarian aspects normally seen with dial-up solu-
tions, where various limitations are assumed because of the limited band-
width. To allow for the expanded communication requirements, many
VPN solutions integrate into the environment in a manner that remains
transparent not only to the user but to the applications that utilized the
connection. Therefore, the protection realized by the VPN is extended
only to the actual transport of data — exactly its purpose.
For the most part, prior to encapsulation or encryption, anything goes,
and the VPN simply protects the transmission. The connection is protect-
ed but that does not equate to the communication being protected. To
detail further, systems on internal networks are considered a community
with common goals that are protected from the Internet by firewalls and
other protection measures. Within the trusted community, data flows
EXHIBIT 5 — Attacker Must Attempt Access to Corporate Data Directly,
the Most Difficult Path
10.12.3.1
10.12.3.2
10.12.3.3
Remote User
(10.12.3.4)
Internet
143.67.89.2
199.12.33.12