index_36
Router Security Configuration Guide
UNCLASSIFIED
36
UNCLASSIFIED
Version 1.0g
3.3. Managing the Router
3.3.1. Access Mechanisms for Administrators
Determining access to the routers by administrators is an important issue. There are
two types of access: local and remote. Local access usually involves a direct
connection to a console port on the router with a dumb terminal or a laptop computer.
Remote access typically involves allowing telnet or SNMP connections to the router
from some computer on the same subnet or a different subnet. It is recommended to
only allow local access because during remote access all telnet passwords or SNMP
community strings are sent in the clear to the router. If an attacker can collect
network traffic during remote access then he can capture passwords or community
strings. However, there are some options if remote access is required.
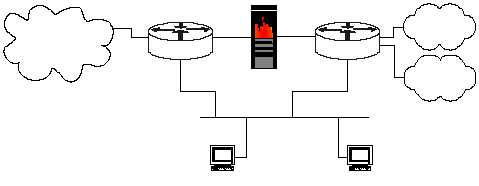
1. Establish a dedicated management network. The management network
should include only identified administration hosts and a spare interface
on each router. Figure 3-3 shows an example of this.
Figure 3-3: Using a Management LAN for Administration
2. Another method is to encrypt all traffic between the administrator’s
computer and the router. In either case a packet filter can be configured
to only allow the identified administration hosts access to the router.
(Section 5.2 shows an example of doing this with a Cisco router and
Windows 2000.)
In addition to how administrators access the router, there may be a need to have more
than one level of administrator, or more than one administrative role. Define clearly
the capabilities of each level or role in the router security policy. For example, one
role might be “network manager”, and administrators authorized to assume that role
may be able to view and modify the configuration settings and interface parameters.
Another role might be “operators”, administrators authorized to assume that role
might be authorized only to clear connections and counters. In general, it is best to
keep the number of fully privileged administrators to a minimum.
Internet
Router
LAN 1
Firewall
Router
LAN 2
Management
LAN
Administration Host
Logging Host