index_32
Router Security Configuration Guide
UNCLASSIFIED
32
UNCLASSIFIED
Version 1.0g
3.2. Protecting the Network with the Router
3.2.1. Roles in Perimeter Security and Security Policy
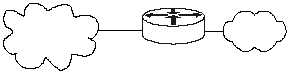
A router provides a capability to
help secure the perimeter of a
protected network. It can do this
by itself. The diagram at right
shows a typical topology with the
router being the component that
connects the protected network to
the Internet.
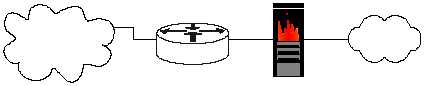
A router can also be used as part of defense-in-depth approach as shown in the
diagram below. It acts as the first line of defense and is known as a screening router.
It contains a static route that passes all connections intended for the protected
network to the firewall. The firewall provides additional access control over the
content of the connections. It can also perform user authentication. This approach is
recommended over using only a router because it offers more security.
Figure 3-1: Typical One-router Internet Connection Configuration
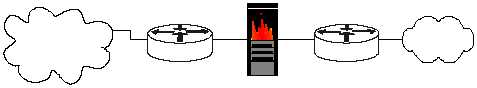
Another approach is to position one router at the connection between the local
premises and the Internet, and then another router between the firewall and the
protected network. This configuration offers two points at which policy can be
enforced. It also offers an intermediate area, often called the de-militarized zone
(DMZ) between the two routers. The DMZ is often used for servers that must be
accessible from the Internet or other external network.
Figure 3-2: Typical Two-router Internet Connection Configuration
Internet
Router
Protected
Network
Firewall
Internet
Router
Protected
Network
Firewall
Router
Premises or
Gateway router
Internal or
Local net router
Internet
Router
Local
Network