index_206
Router Security Configuration Guide
UNCLASSIFIED
206
UNCLASSIFIED
Version 1.0g
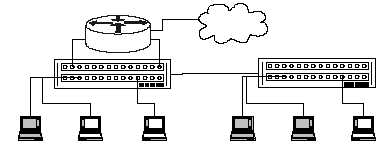
Figure 7-1: Virtual LAN Switching
More investigation is needed to determine the security roles and policies for
configuring VLANs, but it is clear that VLAN security will grow in importance in the
next few years.
LAN Switch 1
Router
LAN 1
14.2.3.0/24
Host A (14.2.3.2)
Host B (14.2.3.3)
Host C (14.2.3.4)
LAN 2
14.2.4.0/24
Host X (14.2.4.6)
Host Y (14.2.4.7)
Host Z (14.2.4.8)
LAN Switch 2
Router
Host A (14.2.3.2)
Host B (14.2.3.3) Host C (14.2.3.4)
Host X (14.2.4.6)
Host Y (14.2.4.7)
Host Z (14.2.4.8)
Virtual View
Real Construction
Internet
Internet