index_178
Router Security Configuration Guide
UNCLASSIFIED
178
UNCLASSIFIED
Version 1.0g
Cisco configuration). In the tabs at the top of this window, select “General”. Under
that tab at the bottom of the screen is a button for “Key Exchange using these
settings” with the word “Advanced” written on the button. Click that. The window
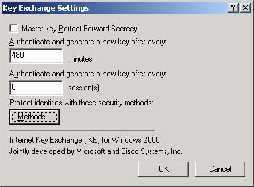
that appears contains the title “Key Exchange Settings”.
In this window, do not check the “Master key Perfect Forward Secrecy” button, and
any values for when to rekey are acceptable. To ensure everything is set up the same
as on the Cisco, click the “Methods” button, under “Protect identities with these
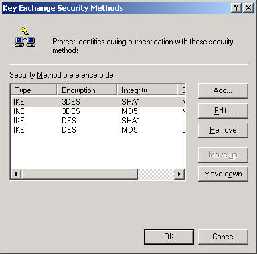
security methods”. Now you will see the following new window. Use the sideways
scroll bar to see if a security method exists with the same settings as on the router.
Those values are IKE negotiation (Cisco calls it ISAKMP, which is actually its older
name), 3DES encryption, SHA1 Integrity (the hashing algorithm), and “Medium (2)”
for the Diffie -Hellman size (which is Group 2, which is the 1024 bit Diffie -Hellman
option, not the 768 bit one). If such a method does not exist, either modify a
currently existing method by highlighting one and hitting the “Edit” button, or click
the “Add” button to create a new one. In either case, you probably should click on
the correct one (which will highlight it), and click the “Move up” button until it is the
first option on the list. The others can either be deleted or just left there.