index_101
UNCLASSIFIED
Implementing Security on Cisco Routers
Version 1.0g
UNCLASSIFIED
101
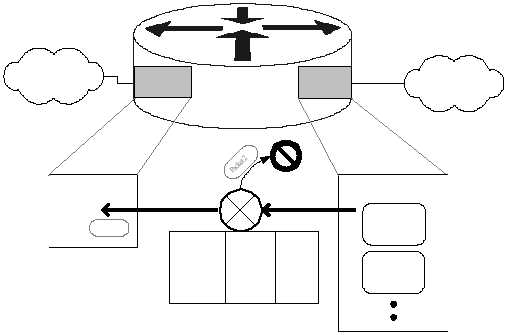
Figure 4-5: IP Unicast RPF Verification
Because unicast RPF verification uses the routing table, it automatically adjusts to
most to changes in network structure. Access lists, while more broadly applicable,
also require more maintenance.
When to Use Unicast Reverse-Path Verification
This facility can be very useful for rejecting packets with improper IP source
addresses, but only when the network architecture permits it to be used. You should
not use unicast RPF verification if any of the following conditions apply.
§ Router uses asymmetric routes –
if any of the interfaces on the router participate in asymmetric routes (one
interface for sending, and a different one for receiving), then unicast RPF
verification must not be used. It will incorrectly reject packets arriving on
the receive le g of the asymmetric route. Cisco has stated that future
versions of IOS will perform unicast RPF correctly in these cases [11].
§ Router does not support CEF –
according to the Cisco documentation, unicast reverse-path verification
depends on Cisco Express Forwarding. If your router does not or cannot
support CEF, then you cannot use unicast RPF.
Unicast RPF verification is best suited for routers that act as part of the security
boundary between two networks (e.g. a filtering router between a LAN and the
Internet). Used properly, it can provide better performance than an access list for
Central
14.1.0.0/16
14.2.9.0/24
Eth0/1
14.2.9.250
Eth0/0
14.1.15.250
Interface Eth0/0
Interface Eth0/1
Trash
Destination
14.2.9.0/24
14.2.10.0/24
14.2.6.0/24
14.1.0.0/16
0.0.0.0/0
Gateway
--
14.2.9.64
14.1.1.20
--
14.1.1.250
Interface
Eth 0/1
Eth 0/1
Eth 0/0
Eth 0/0
Eth 0/0
Routing Table
Packet 1
src=14.2.10.2
dest=10.6.5.9
Packet 2
src=7.12.1.20
dest=7.12.1.20
Packet 1