

|
|
| Previous | Table of Contents | Next |
The larger Windows component of the program follows the short DOS memory image in the EXE file. Therefore, even if the Windows component is 5 MB, if the user runs the program from DOS, only 2,048 bytes of the executable are read into memory and executed. If the user runs the program from Windows, however, Windows properly identifies the file as a special Windows executable file type and properly loads and executes the Windows portion as opposed to the “DOS stub.”
Some file viruses don’t take the above into account when infecting overlaid EXE files. These viruses can inadvertently overwrite the overlaid data or code following the load image, or improperly compute the new viral entry point because of the discrepancy between the actual file size and the program’s memory image size. This can result in the program becoming totally corrupted or functioning erratically.
Finally, many file viruses contain random bugs that cause them to improperly infect certain files. During infection by a particular virus, random corruption can occur. This corruption might or might not be consistent, and can be explained only on a per-virus basis.
Macro viruses, which target data files with macro capabilities, have only recently been introduced into the wild. To date, these viruses have only affected the Microsoft Word for Windows and Excel products. They are a potential threat, however, to any application that supports sophisticated macro capabilities.
These viruses are platform independent and can infect documents and templates on DOS, Macintosh, Windows 3.x, Windows 95, and Windows NT operating systems. They use the same basic techniques in their infection process. This section describes in detail how one, the virulent Word for Windows Concept virus, works, and explains why it has been so widespread.
Under Word for Windows, normal documents can’t have macros attached to them. Only template files (usually named *.DOT) can have local macros attached to the file. Template files are most often used to specify default style and word processing settings for the user. Word for Windows macro viruses can exist only within template files, because macros are required for virus activity.
How and When the Virus Gains Control
The Concept virus has two primary means of gaining control and executing. In the first scenario, the virus has not yet infiltrated the Word for Windows environment. A user opens an infected document for the first time. The document looks like a standard Word for Windows .DOC file; however, it is actually a template file (.DOT format) disguised as a .DOC file. Only a few differences exist between DOC and DOT files as far as the end user is concerned, and the user receives no indication that he or she is opening a template rather than a standard document.
Anytime a user opens a template file, Word for Windows checks to see if the template contains local macros. If it contains a special local macro named AutoOpen, Word for Windows executes the instructions in this macro the moment the file opens. Template files infected with the Concept virus have a specially written “viral” AutoOpen macro. Like the normal AutoOpen macro, Word for Windows automatically executes the viral macro anytime a user opens an infected template file. When the user opens an infected file, the viral macro executes and moves all the various macros of which the Concept virus is comprised from the template file’s local macro pool to Word for Windows’ global macro pool. This occurs automatically and without the user’s permission.
After the user finishes the word processing session and exits Word for Windows, Word for Windows automatically saves all modifications to the global macro pool in a special file called NORMAL.DOT. The NORMAL.DOT file contains default style information, such as the default startup font, as well as all default global macros the system uses. Anytime this information is modified within the Word for Windows environment (for example, by adding new global macros), Word for Windows automatically saves the updated information to the NORMAL.DOT when the user quits the word processor.
Unfortunately, these modifications are saved without any interaction on the part of the user, and the user isn’t informed of any changes! When the user exits the application, Word for Windows prints the normal “Saving file” message on-screen as it saves NORMAL.DOT. However, Word for Windows does this so quickly that most users never notice it.
After the virus updates the global pool, including the NORMAL.DOT file, the virus automatically loads into the global pool every time the user launches Word for Windows. This is the case because whenever Word for Windows starts up, it automatically loads the default stylistic settings and global macros from the NORMAL.DOT template file.
After the initial infection, the NORMAL.DOT file contains all the Concept virus macros, including a copy of the same AutoOpen macro that first infected the computer. When NORMAL.DOT opens during Word for Windows startup, NORMAL.DOT’s viral AutoOpen macro executes just as it would in any template file. Every time the user launches Word for Windows, the virus automatically executes and copies itself to the global macro pool. This is the second way in which the virus gains control in the Word for Windows environment. Figure 15.30 shows the macro virus infection process.
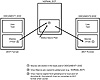
Figure 15.30 Macro virus propagation.
| Previous | Table of Contents | Next |