

|
|
| Previous | Table of Contents | Next |
MBR Virus Example
NYB, also known as the B1 virus, is a simple memory-resident, stealthing boot record virus. It does not infect files. It infects hard drive Master Boot Records when a user attempts to boot from an infected floppy. The virus goes memory-resident when a computer boots from the hard drive or an infected floppy disk.
While the virus is memory-resident, it infects any non–write-protected disk the computer accesses. NYB reserves 1 KB of space in upper memory by decreasing the amount of system memory specified in the BDA’s “Total memory in K-bytes” field. Infected hard drives have their original MBR stored at track 0, head 0, sector 17. A complicated algorithm is used to determine where the original boot record is stored on floppy disks. The results of this algorithm are listed below. The virus intercepts the BIOS disk system service provider to infect other media, and to hide or “stealth” itself by redirecting disk reads.
This virus does not activate in any way, but at random times it performs a series of random reads. This virus does corrupt data, apparently with random reads and writes, and by being overwritten with the original boot sector/partition table.
Unlike the Form virus, the NYB virus displays no text messages on the computer screen.
This analysis was performed by John Wilber of the Symantec AntiVirus Research Center.
Program file viruses (hereafter called just file viruses) use executable files as their medium for propagation. They target one or more of the three most common executable file formats used in DOS: COM files, EXE files, and SYS files.
The basic file virus replicates by attaching a copy of itself to an uninfected executable program. The virus then modifies the new host program so that when the program executes, the virus executes first.
Most file viruses are easy for antivirus programs to detect and remove. First, in all but a few exceptions, file viruses infect at or near the entry point of executable files. The entry point is the location in the file where the operating system begins executing the program. Infecting at the entry point guarantees the virus control of the computer when the program executes.
Viruses that don’t infect at the entry point of an executable file are not guaranteed to gain control of the computer. The virus might insert itself in a data section of the program that ends up never executing; this can corrupt or change the host program’s behavior. These and other problems make infection at arbitrary locations in the program unappealing to virus writers.
The file-infecting virus can only gain control of the computer if the user or the operating system executes a file infected with this virus. In other words, infected files are harmless as long as they are not executed; they can be copied, viewed, or deleted without incident.
A virus chooses a method of program file infection based on the executable file’s type (COM, EXE, or SYS). The following sections describe the six common program file infection techniques.
COM Infections
COM programs have the simplest format of any of the DOS executable file formats; they also have the simplest loading sequence: DOS reads the program directly into memory, then jumps to the first instruction (at the first byte) of the program image. When this action occurs, the program has complete control of the computer, until it relinquishes control back to DOS upon termination.
Prepending COM Viruses
File viruses infect COM files by modifying the machine-language program at the start of the executable image. A virus can ensure that it gains control in at least four different ways, because execution in a COM file must begin at the first byte in the executable image. First, a virus can insert itself at the top of the COM file, moving the original program down after the viral code. The entire virus is then located at the top of the executable image, and is the first to execute when the program is loaded. This method of infection is known as prepending, because the virus affixes itself to the beginning of the host COM program (see fig. 15.18).
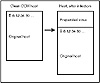
Figure 15.18 Prepending COM virus infection.
Appending COM Viruses
A virus can modify the machine-language program at the top of the executable image of the COM file to transfer control to the virus, which can be located elsewhere in the executable file. The virus often attaches itself to the end of the infected program and changes the first few instructions at the top of the executable image so that they transfer control to the viral code.
Before the virus changes the first few program instructions, it must record what the host program’s original entry instructions were so that it can repair the host program after it has completed. Without preserving these instructions, when the virus transfers control to the host program, the PC would most likely crash or work incorrectly, foiling the virus’ attempts to remain undiscovered. This method of infection is known as appending, because the virus affixes its bulk to the end of the host program (see fig. 15.19).
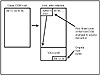
Figure 15.19 Appending COM virus infection.
Overwriting COM Viruses
The third technique used to infect COM files is known as overwriting. Viruses that use this technique often are crudely written. They infect COM programs by entirely overwriting the start of the host program with the viral code (see fig. 15.20). They don’t attempt to save a copy of the host’s bytes that have been overwritten. As a result, the original program can’t work after the virus executes. If a computer becomes infected with a virus of this type, the only way to repair the infected files is to restore them from backups created before the infection.
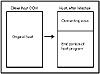
Figure 15.20 Overwriting COM virus infection.
After overwriting viruses infect program files, they either crash or display a bogus error message such as Not enough memory to execute program. Such error messages appear in an attempt to convince the user that the PC has a memory management problem rather than a virus.
| Previous | Table of Contents | Next |