

|
|
| Previous | Table of Contents | Next |
Before a virus attempts to infect the floppy disk, it must determine whether the disk has already been infected. Most often, the virus does so by loading the target FBR into memory and comparing it to its own contents. If the FBR virus ascertains that the target floppy disk isn’t yet infected, it proceeds with the infection process. Most FBR viruses attempt to save the original FBR in another sector on the floppy disk so that if the user ever boots from the disk, the virus can properly start up the operating system that resides on the disk.
FBR viruses almost always store the original boot record in one of two locations on the floppy disk: at the end of the infected floppy disk, or at the end of the sectors used to store the root directory structure of the floppy disk. If the virus is careless, storing the original FBR in either of these locations can cause data loss. The average 1.44 MB, 3 1/2-inch floppy disk has room for 224 files in the root directory. This reserved directory space requires 14 sectors of storage, most of which goes unused because few floppy disks have 224 files stored in the root directory. Many FBR viruses assume that the last sector of the root directory is unused and store the original boot record in this area. If these directory entries are not vacant, the associated files are lost during infection. Furthermore, if the user copies a number of files onto the disk, the overwritten directory entries might be used, overwriting the saved FBR. This results in a crash during subsequent bootups from the floppy disk.
Most other FBR viruses store the original boot record in one of the other final sectors of the floppy disk, also assuming that these sectors are unused. If a virus overwrites one of these sectors with the original boot record contents, it may overwrite existing file data on the disk, causing corruption. In addition, many viruses don’t update the FAT on the disk to indicate that the sector at the end of the disk is in use. If a user tries to copy additional files to the floppy disk, the original boot record may be overwritten by these files, causing subsequent bootups from the floppy disk to crash the computer.
Potential Damage the Virus Can Do
When an FBR virus infects other floppy disks by inserting a viral bootstrap routine into the FBR and storing a copy of the original FBR elsewhere on the floppy disk, it can overwrite other data. Many FBR viruses overwrite the last sector of the root directory structure. If this sector is in use, any file directory entries stored in this sector are destroyed. Luckily, disk tools such as the Norton Disk Doctor can be used to repair this damage.
Other boot viruses store a copy of the original FBR at the end of the floppy disk. If the floppy disk is full, the virus necessarily overwrites a sector in use by a file, destroying at least 512 bytes of its data. Unfortunately, after the virus overwrites a sector being used by a file on the floppy disk, the original contents of the sector can’t be recovered using conventional disk tools.
Almost all Floppy Boot Record (FBR) viruses infect the Master Boot Record (MBR) or the hard drive’s active Partition Boot Record (PBR). The PBR virus is another form of the FBR virus that resides in the boot record of a logical hard drive partition rather than in a floppy disk.
Note: Like the FBR virus, the PBR virus is a program that resides in the bootstrap area of the PBR. For the virus to activate, the PBR must be loaded and executed during the boot-up process.
Few FBR viruses infect the PBR of the active partition; most FBR viruses prefer to infect the MBR of the hard drive. The PBR virus isn’t necessarily inferior to the MBR infecting virus, but creating it is more difficult, which might be why fewer of these viruses exist. On the other hand, the Form PBR virus is one of the most common viruses in the world today.
How Boot Record Viruses Get Control
The typical PBR virus resides in the boot record of the active partition on the hard drive. During hard drive bootup, the ROM BIOS boot routine loads the MBR from the first physical sector of the hard drive. If the MBR contains a valid signature, the ROM program executes the bootstrap routine in the MBR.
The MBR bootstrap routine then locates the active partition and loads its PBR into memory; it does this by examining the four entries in the MBR’s partition table. If the PBR has a valid signature at the end of the sector, the MBR bootstrap routine transfers control to the PBR bootstrap routine and allows it to execute. In an infected PBR, the virus executes at this point during the bootup process and can install itself as a memory-resident driver in the same fashion as the FBR virus (see “When and How Floppy Boot Record Viruses Get Control”). See figure 15.16 for a graphical description of this process.
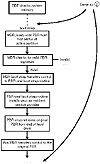
Figure 15.16 Bootup from hard drive with PBR infection.
Unlike FBR viruses, when a PBR virus executes, it doesn’t immediately try to infect other floppy disks. The typical FBR virus infects the hard drive during bootup because it wants to guarantee that future bootups from the hard drive allow the virus to execute and install itself as a resident driver. The PBR virus has no such requirement on the other hand, because it already resides on the hard drive; it uses the hard drive boot sequence only to install itself as a resident driver.
After the PBR virus executes and installs itself in memory during the bootup process, it loads a copy of the original PBR into memory and transfers control to its bootstrap program. This bootstrap program then loads the rest of the operating system normally and the user eventually receives a C: prompt.
As with the FBR virus, once the PBR virus has installed itself as a memory-resident driver, all disk system service requests are sent through the virus’ handler. The virus then can examine the service request and if it chooses, infect the disk being accessed. After the virus performs its mischief, it can redirect the request to the original ROM BIOS driver so that it can be properly serviced.
| Previous | Table of Contents | Next |