

|
|
| Previous | Table of Contents | Next |
At the time of this writing, several different viruses have been written in the WordBasic macro language.
The emergence of macro viruses can be attributed to a number of key factors. First of all, many popular applications, such as desktop publishing, word processing, and spreadsheet programs, include macro capabilities. Such widespread usage is attractive to a macro virus from the standpoint that chances for continued self-replication are high.
Secondly, it is far easier to write macro language programs than assemble language programs. The art of virus writing is no longer limited to the technically astute.
Yet another reason: executable program viruses rely upon a system’s CPU to directly execute its instructions, whereas macro viruses don’t. Because of this, macros are platform independent. The same macro that runs in a Windows-based word processing program, for example, can also function in its Macintosh and Unix counterparts.
Finally, because most antivirus programs to date have focused on viral activity in boot records and executable program files, macro viruses avert detection by storing themselves in a new, less frequently scrutinized realm.
The following list describes the three basic types of viruses:
A disk doesn’t have to be bootable to be able to spread a boot record virus. All floppy disks have boot record programs that are created during formatting.
If a disk has a boot record virus, the virus activates when the PC attempts to boot from the floppy disk or hard disk. Even if the PC can’t start up from an infected disk (such as when the floppy disk does not contain the proper DOS system files), it attempts to run the bootstrap routine, which is all a virus needs to activate. Like a terminate-and-stay-resident program, most boot record viruses install themselves in the host computer’s memory and hook into the various system services provided by the computer’s BIOS and operating system. They remain active in RAM while a workstation remains on. As long as they stay in memory, they can continue to spread by infecting the floppy disks that a computer accesses.
Boot record viruses compose roughly 5 percent of the total collection of IBM PC viruses, yet they account for more than 85 percent of the actual end-user infections reported each year.
See the section “Most Likely Targets,” earlier in this chapter, for details about hardware and software involved in the bootup process.
Most floppy boot record viruses can infect the hard drive MBR or the active partition boot record, in addition to the floppy disk boot record. The floppy disk serves as a carrier for the virus, allowing it to spread from one hard drive to another. After the virus places itself on the hard drive, it can then infect other floppy disks that inevitably make their way to other machines.
When and How Floppy Boot Record Viruses Get Control
Floppy boot record (FBR) viruses seize control of the computer during system reset (see fig. 15.9). During the bootup sequence, the BIOS on most PCs determines whether a floppy disk is present in the floppy drive from which the computer is configured to boot. If the BIOS finds a disk in the drive, it assumes that the user wants to boot from this disk. After it locates the disk, the BIOS loads the floppy boot record into the computer’s memory and executes its bootstrap program.
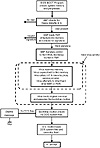
Figure 15.9 The boot sequence from an infected floppy diskette.
On an infected floppy disk, the boot record the BIOS loads is a viral bootstrap routine rather than the usual operating system bootstrap routine (see fig. 15.10). During a bootup, the BIOS grants complete control of the computer to the viral program rather than the normal bootstrap program. After control transfers to the virus, it gains exclusive access to all resources on the computer; the operating system, if one is present on the floppy disk, has not yet been loaded and can’t prevent the virus’ actions.
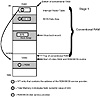
Figure 15.10 BIOS boot program loads viral boot record into RAM and transfers control to the virus bootstrap routine.
Most FBR viruses attempt to install themselves as a memory-resident driver at this point in the bootup sequence. In this way, the virus can monitor all disk service requests during the operation of the computer and infect additional floppy disks at will (see fig. 15.11).
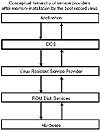
Figure 15.11 Conceptual hierarchy of service providers after memory installation by the boot record virus.
All PCs contain a reserved region of memory known as the BIOS Data Area (BDA). During the initial stages of the computer’s bootup sequence (before control transfers to the bootstrap routine) the BIOS bootup program updates the BDA with information about the configuration and the initial state of the computer. DOS relies on the information stored in the BDA of memory to properly use the peripherals and memory attached to the computer. Almost all FBR viruses exploit DOS’s dependence on the BDA and update its contents to install themselves into memory.
For FBR viruses, the most important field in the BDA is the “Total memory in kilobytes” field, which specifies how much conventional memory is available for operating system use, normally 640 KB. If DOS loads later during bootup, it uses this field to determine how much memory can be safely allocated to itself and other DOS applications. FBR viruses reserve space for their routines and data in memory by decreasing the number in this field. To reserve 2 KB of memory for itself, for instance, a virus decreases the number to 638 (see fig. 15.12). When DOS loads, it determines that only 638 KB of memory is available for its use, and doesn’t read, modify, or update the final kilobyte. The virus then can use this memory without fear of corruption.
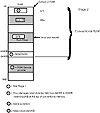
Figure 15.12 Virus reserves 2 KB at top of conventional RAM.
| Previous | Table of Contents | Next |