

|
|
| Previous | Table of Contents | Next |
When you turn on a computer and place a disk in a floppy drive, the Basic Input/Output System (BIOS), a firmware program on a ROM chip, takes control and starts running. The BIOS enables information transfer between the computer’s hardware, such as memory, hard disks, and the monitor. It performs a number of key tasks, such as verifying no memory errors, checking for the hard drive, and setting up the clock. It also determines whether a disk is in the floppy drive from which the computer is configured to boot.
The Power-On Self Test (POST) verifies that all hardware components are running and that the central processing unit (CPU) and memory are working properly. The POST routine then loads up the boot record from the first sector of the disk and checks for two signature bytes at the end of the 512-byte block.
When the boot record signature is present, the ROM chip transfers control to the bootstrap program. The bootstrap program then can do whatever it likes. It can display a message such as nonsystem disk error if no operating system is on the disk, for example, or it can load up the remainder of the DOS operating system. The operating system files eventually launch COMMAND.COM, the command interpreter file, and a prompt appears on the computer screen for drive A. Figure 15.1 shows the boot sequence from an uninfected floppy diskette.
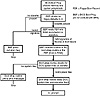
Figure 15.1 Boot sequence from uninfected floppy diskette.
Virus writers frequently target FBRs for one key reason: users often make the mistake of leaving disks in floppy drives. Such a seemingly benign error actually represents the sole mode of entry for the floppy boot record virus. When you have a disk in the drive from which the computer is configured to boot, the bootstrap program always executes. Replacing the original bootstrap routine with the virus’ own program, including its own viral bootstrap routine, enables the virus to gain control of the system before any other program does. The virus then can infect the hard drive.
You can partition a single physical hard drive into several different logical drives. And you can divide drives into multiple partitions for organizational purposes. You might dedicate partitions to different operating systems, for example, or store word processing files in one partition, programs in another, and games in yet another.
The Master Boot Record (MBR) is a structure stored on the first track, sector, and head of the hard drive. Each physical hard drive contains exactly one MBR. The MBR contains a partition table, which denotes the allocation of all sectors and their respective partitions. Programs require the partition table on the hard disk (like they require the BIOS parameter block on the floppy disk) to understand the disk’s characteristics, such as how many partitions (that is, logical drives) exist on the drive.
The MBR also contains a bootstrap program for use during bootup from the hard drive. Similar to the floppy disk’s bootstrap routine, the MBR bootstrap routine is responsible for loading up the default operating system and booting up the computer into a usable state.
The MBR has a limited job, however, because the user can partition a physical hard drive into many logical drives (each potentially with a different operating system). It must first determine which partition is the active partition (the one from which the user wants to boot), and then load and transfer control to the active partition’s Partition Boot Record (PBR). This information is determined by using the contents of the MBR’s partition table.
Booting from the hard drive always requires the same series of steps. During the ROM BIOS’s execution of a cold or warm boot, it checks system memory, checks for peripherals, then determines whether a floppy disk is inserted in the floppy drive from which the PC is configured to boot. If it doesn’t find a floppy disk, it attempts to boot an operating system on the hard drive.
The ROM BIOS boot program then loads the MBR from the hard drive and verifies that it contains a valid signature. If so, the ROM program transfers control to the bootstrap routine in the MBR. The bootstrap routine examines the partition table and determines which partition is active.
Note: Determining the active partition is rather simple because only one partition can be active on a physical hard drive.
After the bootstrap routine determines the active partition, it uses the other information in the partition table to determine the starting track, sector, and head of the active partition. It then loads the Partition Boot Record from the first logical sector of the active partition and checks its signature. If the signature is valid, the MBR bootstrap routine transfers control to the PBR’s bootstrap routine.
The MBR’s bootstrap routine doesn’t know anything about each of the many possible operating systems present on the computer. All it knows about is transferring control to the bootstrap routine in the PBR of the active partition.
The partition table is the only section of the MBR that must remain intact (other than the signature at the end of the MBR) for DOS and other programs to properly understand the drive’s layout and partitioning.
There are two reasons why the hard drive MBR is often targeted. For one thing, hard drives contain only one hard drive Master Boot Record in the same physical location on all PC hard drives. Therefore, virus writers can easily write viruses that can work on almost any PC on the market.
Furthermore, when the computer boots from the hard drive, the bootstrap routine in the MBR always loads and executes. If the virus replaces the MBR bootstrap routine with its own MBR bootstrap routine, it executes during each system bootup. During system bootup, the virus gains complete control over the computer before any software-based antivirus program has a chance to load and protect the system. Figure 15.2 shows the boot sequence from an
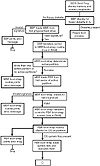
Figure 15.2 Boot sequence from uninfected hard drive.
| Previous | Table of Contents | Next |