

|
|
| Previous | Table of Contents | Next |
Windows NT was designed to be portable across different processor architectures including the Intel x86 line and RISC processors such as the MIPS and DEC Alpha processors. In addition, Windows NT supports symmetric multiprocessing on multiprocessor systems. Symmetric multiprocessing allows different portions of an applications to run on different processors at the same time and complete a task much faster. This is done through multithreading—tasks are broken up into separate processes and run with different start and completion times on a single processor or multiple processors. Windows NT was the first network operating system to achieve this level of processing.
Windows NT has a modular design. Adding new modules to any level of the operating system at any time is easy without affecting the stability of the operating system. Due to symmetric processing, the system easily scales up to handle additional loads by simply adding more processors. In addition, Windows NT supports clustering, which is a way to link multiple servers together for shared processing and access to resources.
Security is built into Windows NT at the core level, which provides a consistent security model at all levels. We now delve into the architectural design and core features of the operating system.
As shown in figure 12.1, the base operating system is composed of a family of software components called the Executive Services that run in Kernel Mode.
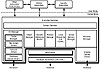
Figure 12.1 The Windows NT system architecture consists of the lower-level kernel mode and the upper-level user mode.
Above the Kernel Mode is the User Mode, which consists of non-privileges services called protected subsystems that are started at the discretion of the user. Basically, the Kernel Mode components are required and make up a self-contained operating system. The User Mode components run on top of the kernel and take advantage of its functions.
Some subsystems are integral, meaning that they augment a critical operating system function. The Security subsystem is an example of an integral system. Environmental subsystems support applications. Currently, the Win32 (32-bit Windows) subsystem is the native Windows NT subsystem. Other available subsystems are POSIX and OS/2, but they are waning in importance.
Any of these components can by updated or replaced at any time to improve the operation of the operating system, update its core technology, or add new technology components.
The Security Subsystem
The security model is pictured in figure 12.2. Note that this discussion centers around the Security Reference Monitor in the kernel and the Security subsystem as pictured in Figure 12.1.
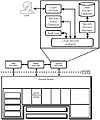
Figure 12.2 The security subsystem is a complete set of components integrated into the Windows NT architecture.
The purpose of the security system is to protect all the components of the system, including hardware, software, and data stored on the system. The security system pictured in figure 12.2 applies to both Windows NT Workstation and Windows NT server, except that the user account database in Windows NT Server can apply to a whole domain whereas the user account database in Windows NT Workstation is local only.
Everything in the Windows NT operating system is an object to which access is strictly controlled by the security system. The details of this object access are given in a moment. For the time being, keep in mind that objects include not only directories and files, but also peripherals like printers and even objects on the screen like the program components.
Access to objects and the system is controlled in the following ways:
These controls enable administrators to specifically define what users can do and where they can do it. They also enable the operating system to protect objects from random or malicious reuse and access.
Access to objects is only provided to authorized users, so all users must identify themselves at logon. A guest account is available but it generally has limited access to objects. Each user is given a unique identification number and is tracked through each logon session via a unique token. The token changes with each logon to prevent attacks by crackers that discover the token. All user activities can be written to audit logs. Administrators can define who and what is audited and have exclusive rights to view the audit logs.
| Previous | Table of Contents | Next |