

|
|
| Previous | Table of Contents | Next |
Assume Joe wants to send Alice a signed message. The procedure is outlined next and pictured in figure 10.5.
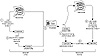
Figure 10.5 The steps for using digital signatures involve creating the signature (the sender) and checking the signature (the recipient).
Digital signatures and digital certificates are encryption-based methods for proving the identities of users (user authentication), the origin of messages (message authentication), and the integrity of documents. They can also provide non-repudiation as well as digital time stamping, which effectively binds a document to the time it was created or sealed.
Secure network operating systems use various schemes to verify the identity of a person logging in. In the simplest form, the user must type a user name and password. A user account matching the name is referenced to see if the password is correct. If so, the user gains access.
Of course, this scheme breaks down if the password is found out by someone else or if it is captured and read during transmission. One problem that exists on some networks is that users may use the same password to log onto different systems. However, one of those systems might accept unencrypted passwords (that is, plaintext passwords sent “in-the-clear”). An attacker could somehow capture passwords that are sent to the unsecure system, then attempt to use them to gain access to more secure systems.
One way to solve this problem is the challenge-response method, which does not require you to send any kind of password over the wire, either plaintext or encrypted. With the challenge-response scheme, the client is issued a challenge and must provide an appropriate response to log on. The response is calculated using the user’s password, but the password itself is never sent. The reason this works is that the authenticating server performs the same calculation using the challenge it sent to the user and the user’s password, which it has stored. If its own calculated response compares to the user’s response, then the user is considered valid.
Note: Refer to Chapter 9, “Kerberos,” for a discussion of the Kerberos authentication model.
Authentication within the corporate environment has been relatively easy to implement compared to validating remote users or Internet users who want to access your systems. Internally, you can create accounts for known users, validate the user based on the machine they are logging in from, and require the use of a preferred authentication scheme by every system in the organization. You simply have more control over the security of the entire system.
Authenticating remote users and Internet users is another matter. Assume you set up a web server that contains sensitive information. Only select users can access the information on the server. What techniques can you use to authenticate users over the Internet to prevent spoofing? There are two possibilities:
Of course, these schemes may differ slightly, based on the implementation. Certificates are available from the certificate authorities listed earlier. See table 10.3 for a list of sites where token authentication devices are available.
| Site Name | Address |
|---|---|
| Datakey, Inc. | http://www.datakey.com |
| ActivCard, Inc. | http://www.activcard.com |
| Security Dynamics | http://www.securid.com |
| Digital Pathways | http://www.digpath.com |
| Previous | Table of Contents | Next |