

|
|
| Previous | Table of Contents | Next |
RFC 1510
This document gives an overview and specification of version 5 of the protocol for the Kerberos network authentication system. It is available from the following:
ftp://ftp.isi.edu/in-notes/rfc1510.txt
Much of the information in this chapter is based on RFC 1510, and some portions are directly extracted from the RFC.
The design of Kerberos has goals in three areas: authentication, authorization, and accounting. In addition, any function that benefits from the secure distribution of encryption keys will benefit.
There is much discussion in the security industry of how particular systems fit into the government-trusted host classification system. Kerberos by itself does not fit into the trust classifications because it does not offer a full security environment. It can, however, be used as a component when building a secure network. Kerberos provides an authentication mechanism and encryption tools that can be used to implement a secure networking environment.
Authentication
Any user can make a claim to an ID. The authentication process tests this claim. During basic authentication, the user is asked to provide a password. During enhanced authentication, the user is asked to use a piece of hardware (a token) assigned to the legitimate owner of that ID. Alternatively, the user can be asked to provide biometric measurements (thumbprints, voiceprints, or retinal scans) to authenticate the claim to that ID.
Kerberos’ goal is to remove authentication from the insecure workstation to a centralized authentication server. This authentication server can be physically secured, and can be controlled to ensure its reliability. This ensures that all users within a Kerberos realm have been authenticated to the same standard or policy.
Authorization
After a user has been authenticated, the application or network service can administrate authorization. It looks at the requested resource or application function and verifies that the owner of the ID has permission to use the resource or perform the application function.
Kerberos’ goal is to provide a trusted authentication of the ID on which a system can base its authorizations.
Accounting and Auditing
The goal of accounting is to support quotas charged against the client (to limit consumption) and/or charges based on consumption. In addition, accounting audits users’ activities to ensure that responsibility for an action can be traced to the initiator of the action. Auditing, for example, can trace the originator of an invoice back to the individual who entered it into the system.
Security of the accounting and auditing system is important. If an intruder is able to modify accounting and auditing information, it is no longer possible to ensure that a user is responsible for his/her actions.
The goal of Kerberos is to permit attachment of an integrated, secure, reliable accounting system.
Kerberos performs authentication as a trusted third-party authentication service using shared secret key cryptography.
The authentication process proceeds as follows:
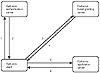
Figure 9.2 Kerberos authentication protocol.
An implementation consists of one or more authentication servers running on physically secure hosts. Each authentication server maintains a database of principals (that is, users and servers) and their secret keys. Code libraries on the server provide encryption and implement the Kerberos protocol. Before a typical network can add authentication to its transactions, it adds calls to the Kerberos library, which results in the transmission of the necessary messages to achieve authentication.
A client can use two methods for asking a Kerberos server for credentials:
After credentials are obtained, they can be used to establish the level of security the application requests:
| Previous | Table of Contents | Next |