

|
|
| Previous | Table of Contents | Next |
Not all of the functionality or corresponding programs and files in table 3.1 exist between implementations. One implementation has one file or program, and the other does not.
The UUCP network consists of a group of machines connected by some communication mechanism that uses UUCP to transfer files and information. A sample network is depicted in figure 3.1.
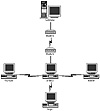
Figure 3.1 A sample UUCP network.
This UUCP network consists of a gateway that provides UUCP services via dialup at 19.2 Kbaud to the machine unilabs. In turn, unilabs offers dedicated UUCP connections over direct serial cables to the machines bugs, thumper, and wabbit.
Machines are connected via a modem and phone line, a direct connection—serial cable—between machines in close proximity, or some form of a leased line in the case of distant systems. If desired, UUCP can even be deployed over TCP/IP.
Often the machines in a UUCP network are different models or use different operating system versions. The network in figure 3.1 has SunOS, SCO Unix, Motorola Unix, AT&T Unix, Spectrix XENIX, and SCO XENIX in it. Even though all the machines are running Unix, each version has a unique form of UUCP; the only way to ensure network communication is through sysop cooperation.
A UUCP job is submitted by a user through the commands uucp, uux, or uuto. These commands create a job file in the /usr/spool/uucp/sysname directory. The program uucico then runs at some point and calls the remote system. The uucico program then logs in and transfers the files; afterward, the program uuxqt is run to complete the processing on the remote system. UUCP is a batch-processing service: it may take a while for the job to be processed, depending on whether the system administrator restricted the times when the uucico daemon executes.
UUCP, like most networking tools, has a specific form of machine addressing. This form is commonly referred to as bang addressing. Machines in the UUCP command are separated by “ !” (pronounced “bang”), with the file name as the final component, as in this syntax:
thumper!unilabs!choreo!/tmp/transfer
A file travels from the machine thumper, to unilabs, to choreo, where it ends up as the file /tmp/transfer. UUCP commands do not understand Internet or Domain addressing, which is typically used in TCP/IP and many mail applications. Internet addressing uses the “@” symbol to separate machine and user:
chare@unilabs.org
Users who are working with the C shell know that the “!” has special meaning for that shell. When you use the UUCP commands, remember to ‘escape’ the “!” with a backslash to prevent the C shell from interpreting the “!”, as shown in this example:
thumper\!unilabs\!choreo\!/tmp/transfer
Note: You can execute a UUCP command, but whether the remote system will carry out your request depends on the level of security that has been established on the remote system.
Before you read about the process of naming your system, you first need to understand the various names your system already has. In addition to the name your machine uses for networking purposes (issue the uname command to see what this is), it has a system name that describes the operating system. You can find the system name by issuing uname with the -s option (although this can often be overridden). Sample output of the uname command follows:
pc:~# uname Linux pc:~# uname -s Linux pc:~# uname -a Linux pc 1.0.9 #3 Tue Sep 13 04:45:23 CDT 1994 i486 pc:~#
This name is not part of UUCP but is inherent in the operating system itself. Yet another name for your system, called the nodename or hostname, appears when you issue the uname -n command, or the hostname command on those systems that support it:
pc:~# uname -n pc pc:~# hostname pc pc:~#
Many implementations of UUCP limit the number of characters allowable in the UUCP name to six or seven; because of this, the UUCP name may not even be the same as the host name. Even though you can use longer names in the commands, the names of the different machines should be unique for the first seven characters. Consider two machines named “gateway1” and “gateway2.” They are the same for the first seven characters; transactions for one machine could possibly be delivered to the other in error.
If you are not connected to Usenet or the Internet, you basically have free license on what you call your machines. If you are part of Usenet, however, you should contact your Usenet hookup and ask them to check whether the name you want is already in use. Alternatively, you can contact a local UUCP registry, which will verify that the machine that you are connecting doesn’t have a name conflict with someone else’s machine. Always try to choose a name for your Usenet machine that describes the organization. For example, UniLabs Research Group initially started with the name “unilabs.uucp” for Internet work, and has since registered into the .org network domain. The name, unilabs, had to first be processed by the Canadian UUCP Registry to verify that the name didn’t conflict.
Regardless of the existence of the Usenet connection, try to choose meaningful names. Resist the common urge to use names such as “host1,” “server22,” and “sco111,” which do little to describe their purpose. Many organizations follow a common theme to describe their machines. For example, one company the author was involved with initially used cookie names (oreo, pirate, chipsahoy) for their machines, but has since started to incorporate cartoon characters (goofy, mickey, tazDevil).
A side effect of using obscure names is that it is harder for the system administrator to remember which machine serves what purpose. Commonly used names, such as ftp, will highlight these services provided by a particular machine, and invite attention.
The actual mechanism of changing or setting the system name depends on the Unix derivative you are using. On SCO Unix, for example, the name is generally compiled into the kernel; SCO XENIX uses the file /etc/systemid. Check your system documentation to determine the method in which the system name is defined.
| Previous | Table of Contents | Next |