

|
|
| Previous | Table of Contents | Next |
Class A Addresses
In a class A address, the first octet represents the network portion, and the remaining three identify the host (see fig. 1.1).
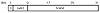
Figure 1.1 The class A address format.
This address class means that this network can have millions of hosts because there are 24 bits available to specify the host address. In figure 1.1, you see that the first bit of the first octet is set to 0. This means that the network portion of the address must be less than 128. Actually, the network portion of a class A address ranges from 1 to 127.
Class B Addresses
A class B address is similar in structure to a class A, with the exception that a class B address uses two octets for the network portion and two octets for the host portion (see fig. 1.2). This means that there can be more class B networks, each with thousands of hosts.

Figure 1.2 The class B address format.
As illustrated in figure 1.2, the configuration of the class B address is such that each portion shares the same amount of the address. The first two bits of the network address are set to 1 and 0, meaning that the network address ranges from 128 to 191. With this format, each network can have thousands of hosts.
Class C Addresses
A class C address uses three octets for the network portion, and one octet for the host. The result is that there can be more class C networks, each with a small number of hosts. Because the maximum value of a single octet is 255, and there are two reserved values, there can be 253 hosts for a class C network. This network format is illustrated in figure 1.3.

Figure 1.3 The class C address format.
As illustrated in figure 1.3, the first two bits of the network address are set to one. This means that the network address for a class C network ranges from 192 to 223. The remaining values from 224 to 255 are used in the fourth address class.
Special Addresses
It has been mentioned that there are several different addresses reserved for special purposes. These addresses are listed in table 1.1.
| Dotted Decimal Address | Explanation |
|---|---|
| 0.0.0.0 | All hosts broadcast address for old Sun networks. |
| num.num.num.0 | Identifies the entire network. |
| num.num.num.255 | All hosts on the specified network. (Broadcast Address) |
| 255.255.255.255 | All hosts broadcast for current networks. |
These reserved addresses cannot be used to address any host or network. They have been specifically reserved. There can be other reserved addresses depending upon other factors, which you will see later in this chapter.
Each host on a network has a specific IP address to enable other hosts to communicate with it. Depending upon the class of network, there can be anywhere from 253 to millions of hosts on a network. It would not be practical, however, for a class A or class B address to be restricted to one network with thousands or millions of hosts. To solve this problem, subnets were developed to split the host portion of the address into additional networks.
Subnets work by taking the host portion of the address and splitting the address space by using a netmask. The netmask essentially moves the dividing line between the network and the hosts from one place to another within the address. This has the effect of increasing the number of available networks, but reduces the number of hosts that can be connected to each individual network.
The use of subnets does provide advantages. Many smaller organizations can only obtain a class C address, yet they have several distinct offices that must be linked together. If they only have one IP address, a router will not connect the two locations because the router requires that each network has a distinct address. By splitting the network into subnets, they can use a router to connect the two networks because they now have distinctly different network addresses.
The subnet is interpreted through the netmask, or subnet mask. If the bit is on in the netmask, that equivalent bit in the address is interpreted as a network bit. If the bit is off, it is considered part of the host address. It is important to note that the subnet is known only locally; to the rest of the Internet, the address looks like a standard IP address.
As noted in the following table, each class of IP addresses has a default netmask associated with it.
| Address Class | Default Netmask |
|---|---|
| A | 255.0.0.0 |
| B | 255.255.0.0 |
| C | 255.255.255.0 |
To fully understand and appreciate how this works, consider an example. Assume that you have a network address of 198.53.64.0, and you want to break this up into subnets. To further subdivide this class C network, you must use some of the bits in the host portion, or last byte, of the address as part of the network portion. Although this increases the number of networks you can have, it decreases the number of hosts that can be on each subnet.
The Internet RFC 950 also requires that the first and last division of each subnet be reserved. This means that the actual number of useable subnets is two less than the total number of divisions. For example, if you want to split your class C network into two divisions, you cannot connect any hosts. If you want to have six subnets, then you must split your network into eight divisions.
The following example illustrates how the bits in the last octet are set, and how many subnets and hosts can be created for each. The variable portion that represents the bits used for the host portion is identified by the letter V.
8 7 6 5 4 3 2 1 Divisions Subnets Hosts/Subnets ----------------------------------------------------------- F V V V V V V V 2 0 0 F F V V V V V V 4 2 62 F F F V V V V V 8 6 30 F F F F V V V V 16 14 14 F F F F F V V V 32 30 6 F F F F F F V V 64 62 2 F F F F F F F V 128 126 0
The preceding example shows that you can effectively only use a minimum division of four with two subnets and 62 hosts per net, or a maximum of 64 divisions, which results in 62 subnets of two hosts each. The first example could be used for two separate ethernets, while the second could be used for a series of point-to-point protocol links.
| Previous | Table of Contents | Next |