

|
|
Initiation responsibility: PBX officer; IT Security Management
Implementation responsibility: Administrators
Here external remote access is understood to mean any access through the maintenance port of the telecommunications (PBX) system via public switching systems. The reasons for such access may be either that the individual installations of the PBX network are not, or not exclusively,1/ connected through dedicated lines or that, in emergencies, reliance on quick assistance by the manufacturer is indispensable. In such cases, the service port (modem) must have full direct-access rights.
The following illustration shows a typical scenario of an external remote access to a remote administration port via modem. The PBX system is administered by the external service point via modem 1 - public network - PBX 1 - modem 2 - V.24 service interface.
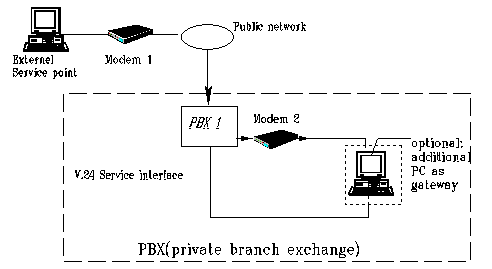
Menu diagram: Configuration of external remote administration via modem
For security reasons, it is advisable to operate without external remote maintenance. Where this is not possible, apart from the measures for internal remote access, additional safeguards are unavoidable.
PC-Gateway*
A PC gateway should be switched between the service port and the modem. This should provide the following security functions:
In addition, other functions can be implemented as well:
Physical de-activation of the remote-maintenance ports
If remote maintenance is normally not required and is to be provided only if required, physical shut-off of the port is recommended. If required, it can be re-activated at short notice, possibly after consultation over the telephone with the manufacturer or the service contractor.
Closed User Group (CUG)
It is possible to create a CUG in public ISDN and X.25 networks. Here, the network operator provides the user with a virtual "network within a network". The closed user groups can be obtained from the network operator against the appropriate fee.
Alternatively, it can be considered realising the closed user groups by using the ISDN Calling Line Identification and Presentation (CLIP) and Connected Line Identification and Presentation (COLP). If possible, this can also be done by appropriately configuring the PBX system or the PC gateway.
Avoiding or controlling direct dial-in
Direct dial-in, e.g. from other networks by suffix dialling in dual tone multifrequency signalling, into the PBX system should be disabled, if possible. This is often used for access to server services. If it is not possible to prevent direct dial-in, it is recommended to activate all available protective mechanisms and regular controls to detect possible abuse.
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |