

|
|
Initiation responsibility: PBX officer; IT Security Management
Implementation responsibility: Administrators
The remote accesses in case of PBX equipment are used for remote maintenance, remote administration and network management tasks. Furthermore, remote accesses can also exist for system users (dial-in options).
A distinction can be made between
In the case of internal remote access, consideration is given to measures for the protection of remote maintenance within a telecommunications (PBX) network. Such a network is understood to mean an overall installation comprising several separate facilities interconnected with private lines. Where such a link is provided over public switching systems, the measures described under S 5.15 External remote maintenance must be implemented as well. In case of networking via closed user groups within public networks or via virtual private networks (VPN), the measures for internal remote access and, if possible, the items marked * in the measures for external remote accesses should be implemented.
The most important aspect when securing the internal "remote access" is being able to effectively prevent and detect penetration attempts from external networks. Furthermore, the accesses from the internal network should be limited to the authorised points and persons. There are various methods of doing this, depending on the type of access technology.
Securing an internal remote access via modem
The following illustration shows a typical scenario of an internal remote access to a remote administration port via modem. The PBX 1 system is administered by the service point directly via the V.24 service interface. The PBX 2 system is administered by the service point via modem 1 - PBX 1 - PBX 2 - modem 2 - V.24 service interface.
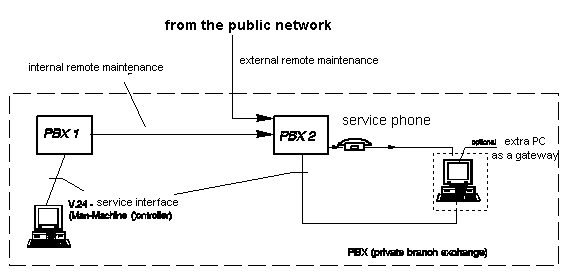
Diagram: Modem
In this case, the following measures can be taken to protect against accesses from external networks:
In order to ensure that only authorised bodies within the internal network can gain access to remote accesses, the following steps must be taken:
In order to ensure that only authorised persons within the internal network can gain access to remote accesses, the following steps must be taken:
Securing an internal remote access via ISDN networks
For practical reasons, it is recommended to equip the PC's used for network management tasks with ISDN cards. In this instance, a closed user group should be created. Here, the number of the calling party can be used (Calling Line Identification and Presentation CLIP). This could be implemented by the terminal itself using the number of the calling terminal (CLIP) provided by the network.
Securing Direct Inward System Access (DISA)
If possible, direct system accesses should be blocked. If this is not possible, the authorisation should be set in such a way that the direct system access can only take place via a dedicated port. In this way it is possible to run the DISA access via a gateway. An example of this is shown in the following illustration:
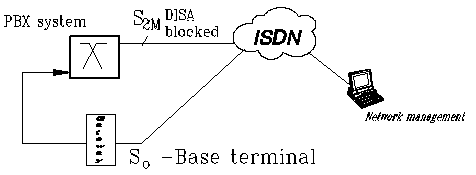
Menu diagram: Securing a direct system access
Establishment and accommodation of a network management centre
The advantage of a central network management is, that besides being a convenient method of system administration, physical access to the PBX is no longer needed for everyday administration work.
If the installation of central network management is being considered, it should be located in a secure area. Access to this centre should be controlled using organisational measures. For the relevant provisions, c.f. Chapter 4.3.2 Server Room. The management computers from which work can be carried out should be protected by suitable safeguards. See Chapter 5.1 DOS PC (single user) and 5.2 Unix system.
Logging of maintenance work
It must be possible at all times to get a picture of the current plant configuration, i.e. allocated call numbers and rights, activated and de-activated user facilities, established follow-me groups, etc. For this purpose, the changes made must be logged. A neat solution is forced logging by means of a PC gateway.
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |