

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: IT Security Management, Administrators
As it is impossible to predict the routes and nodes via which data will be sent over the Internet, data should always be encrypted before it is sent if at all possible. It would be useful if mechanisms to ensure that this is done were already provided in the lower layers of the protocol.
First, though, a distinction should be drawn between two approaches to encryption:
Encryption at the firewall
In order to exchange data with external communications partners via an open network and/or to grant these partners access to your own network, it may make sense to set up virtual private networks (VPNs). All connections to and from these partners should be encrypted, so that no unauthorised users can gain access to the connections. A large number of hardware and software solutions can be used to set up encrypted connections. If it is intended to connect only a few properties to each other, hardware solutions based on symmetric cryptographic procedures, in particular, are a simple and safe choice.
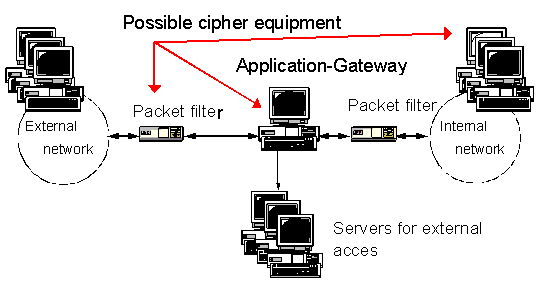
Figure: Integration of a crypto module into a firewall
Encryption and decryption can be performed on different devices. For example, a hardware solution in the packet filter could be used as the cipher equipment. This makes sense in particular in cases where no unencrypted communication is to be allowed via the device.
In contrast, the integration of encryption on the application gateway has the advantage of easier user administration. Furthermore, an attacker who has gained control of an external information server cannot eavesdrop on the encrypted communication.
Encryption on the terminal equipment
In order to protect the confidentiality of certain data, especially when sending e-mails, another option that suggests itself is the use of mechanisms that allow end-to-end encryption. The freely available software package PGP (Pretty Good Privacy) is very often used for this, for example (see S 5.63 Use of PGP). To ensure trustworthy data exchange with selected partners on the Internet, modified telnet and ftp programs should be used, which support encryption of the data being transmitted.
For the foreseeable future, encryption on the end systems will still be tied to specific applications, for example through the use of SSL or PGP. On the other hand, however, the encryption of data also presents a major problem for the effective use of firewalls, i.e. the filters. If the transmission of encrypted data via the firewall is permitted (as is the case with SSL), filters on the application layer are no longer capable of checking the user data with respect to viruses or other harmful programs, for example. The logging options available are also greatly restricted by encryption. An initial ad hoc solution could take the form of allowing SSL connections to be set up from certain internal computers, perhaps only to selected destination systems. On the other hand the data is protected even if an attacker has gained control of the application gateway.
Temporary decryption on a filter component for analytical purposes is neither practicable nor desirable.
No general recommendation can be given for against the use of encryption via or at a firewall; this is dependent on the requirements applying in each individual case.
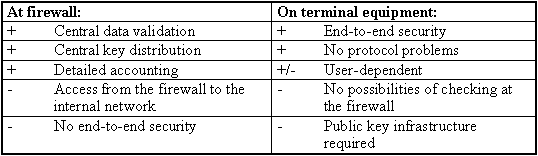
Advantages and disadvantages of various possible implementations
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |