

|
|
Initiation responsibility: Head of IT Section
Implementation responsibility: Administrators
If Windows 95 computers are run in a network (Novell Netware or Windows NT), use should be made of the option of storing the applicable system guidelines on network servers and managing them centrally from there.
In this case, the primary network login, i.e. the path for the system guidelines, is specified via CONTROL PANEL under NETWORK. The user profiles on a Novell Netware server are stored by default under SYS:PUBLIC. If a primary network login is performed on a Windows NT computer, the user profiles are stored by default under NETLOGON (%SystemRoot%\SYSTEM32\REPL\IMPORT\SCRIPTS\).
Activation of the user profiles is ensured with the help of CONTROL PANEL / PASSWORDS / USER PROFILES.
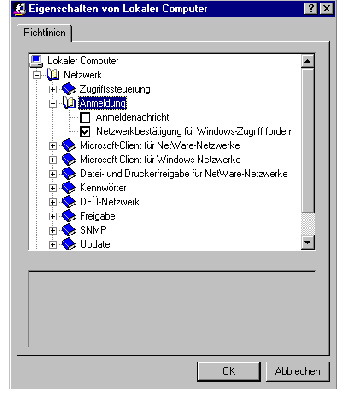
In addition, an operation of Windows 95 without network login should be disabled in order to prevent circumvention of the system guidelines on a local basis. For this purpose, the option designated REQUEST NETWORK CONFIRMATION FOR WINDOWS ACCESS should be activated with the help of POLEDIT.EXE via local computer-network login.
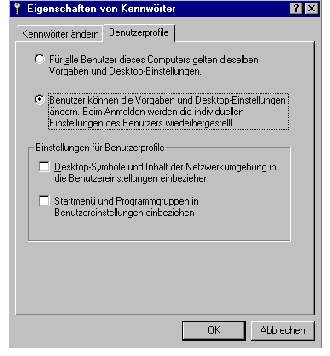
For reasons of standardisation, the system guidelines should be managed primarily through the configuration of user groups.
Under Windows 95, group guidelines are installed via CONTROL PANEL / SOFTWARE / WINDOWS / SETUP and located by default in the directory named ADMIN\APPTOOLS\POLEDIT\GROUPPOL.INF.
The names of the user groups must correspond to those of the user groups configured under Novell Netware or Windows NT.
Furthermore, to ensure correct IT operation, the program named POLEDIT.EXE must not be installed on the local Windows 95 computer, as anyone could use this program to perform persistent modifications to the valid system guidelines.
Also, the BootKeys parameter in the file named MSDOS.SYS should be changed (BootKeys=1) to prevent Windows 95 from starting in the "protected" mode. This ensures observance of the system guidelines.
Finally, the BIOS of the computer should be set to prevent a system boot from a floppy disk, and the floppy-disk drive should be furnished with a lock to discourage the use of unauthorised software.
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |