

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: Administrators
For each user, access to a Windows NT system must be protected by a password. User accounts without a password are not allowed to exist, as they constitute a potential weakness in the system. It is important that users too are familiar with the protective function of the passwords, since the co-operation of users naturally contributes to the security of the overall system.
Setting up a new user is performed with the aid of the utility User Manager via the command " New User ". At the same time an initial password with a maximum of 14 characters must be entered in the fields "Password" and "Confirm Password". For passwords under Windows NT, the use of upper and lower case letters must be observed. A meaningful initial password should be allocated which is notified to the user. Always choosing the same initial password or making this password identical to the user name opens up a security gap which can be avoided with a little effort.
The option " User Must Change Password At Next Log-On " should be set with all new accounts, so that the log-on password is not retained. On the other hand, the option " User Cannot Change Password " should only be used in exceptional cases, for instance for pre-defined accounts in the training operation. The option " Password Never Expires " should only be used for user accounts to which a service is assigned with the aid of the system control option " Services " ( the reproduction service, for example), as it cancels the setting " Maximum Password Age " in the Accounts Policy and prevents the password from expiring.
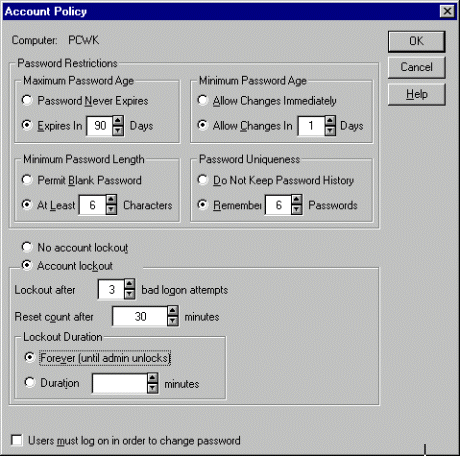
Policy for user accounts, user rights and system monitoring can be stipulated via User Manager. In the User Accounts Policy the figure 6 should be entered as the minimum password length, for higher security requirements the figure 8 should be entered (see also S 2.11 " Provisions governing the use of passwords ").
Password history should always be activated and should include at least 6 passwords. The duration of validity of the password (" Maximum Password Duration ") should be limited to a maximum period of 6 months. By fixing a figure for " Minimum Password Duration ", users can be prevented from changing their password several times in a row with the object of by-passing history validation. However, a period greater than 1 day should not be chosen for " Minimum Password Duration ", in order to enable the user to change a password at any time.
Note: The parameter " Allow Changes Immediately " must not be chosen under version 3.51 of Windows NT, as otherwise validation of password history is deactivated.
User accounts should be locked out following repeated invalid password entries, in order to make attempts to guess the passwords of users more difficult. The option " Account lockout " should in any case be activated. At the same time the option " Lockout after ", which fixes the number (1 to 999) of invalid log-on attempts which lead to the lockout of the account, should be set to a figure between 3 and 10. The option " Reset count after ", which specifies the maximum number of minutes (1 to 99999) between two invalid log-on attempts, should be set at approximately half an hour. If, for example, for " Lockout after " the figure 5 and for " Reset count after " the figure 30 is specified, a lockout occurs after 5 invalid log-on attempts made within a timeslot of 29 minutes.
In general, by activating the option " Forever " it should be stipulated that lockout remains active until an administrator cancels it. Should this place too heavy a burden on the administrators, a suitable figure can also be specified as " Lockout duration ", so that account lockout is only maintained for a limited period. If it is intended to investigate the causes of account lockout directly, a sufficiently long time interval, e.g. 1,440 minutes (1 day) should be specified, otherwise a figure of approximately 30 minutes should be chosen.
In order to avoid complete locking of the system (see S 4.55 Secure Installation of Windows NT), it should be noted that the pre-defined administrator account is not included in this automatic lockout..
The option "User must log on in order to change password" should not be activated. Together with the setting "User must change password on next log on" this would lead to new users having no access to the system.
The policy figures shown in the following diagram give adequate protection in terms of an average security requirement:
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |