

|
|
Initiation responsibility: Agency/company management
Implementation responsibility: Agency/company management; IT Security Management Team
IT security is of particular importance to all IT projects, all IT systems and all IT users in an organisation. The aspired-to level of IT security can only be achieved if the IT security policy is implemented throughout the agency/company. This organisation-wide character of the IT security process makes it necessary to specify particular roles within the agency/company. Appropriate tasks must be assigned to each role, and these roles must be served by staff with the appropriate skills. This is the only way to ensure that all important aspects are taken into consideration and that all tasks are carried out efficiently and effectively.
IT security management depends on the size, nature and structure of the organisation concerned. The following central roles should be defined in every case:
To guarantee direct access to Management, these should both be organised as special staff functions.
Basic rule:
The most important considerations in the definition of roles in IT security management are:
Organisational structure of IT security management
Depending on the size of the organisation, there are three possible ways of structuring IT security management. These are illustrated in the diagrams below. The first diagram shows the organisational structure for IT security management in a large organisation. The second diagram shows the organisational structure in a medium-sized organisation in which the roles of the IT Security Management Team and IT Security Officer are merged. The third diagram presents an organisational structure for IT security management in a small organisation, where all the tasks are performed by the IT Security Officer.
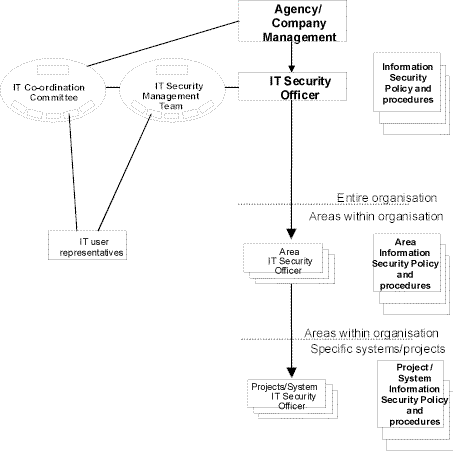
Figure 1: Organisational structure of IT security management in a large organisation
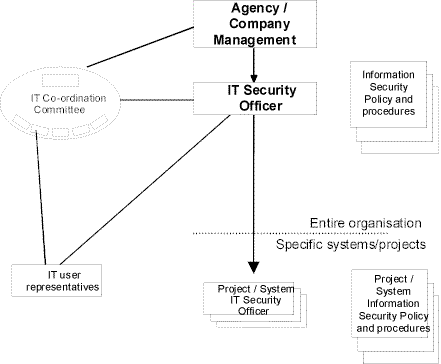
Figure 2: Organisational structure of IT security management in a medium-sized organisation
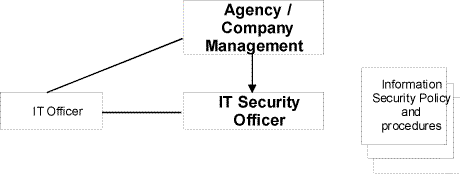
Figure 3: Organisational structure of IT security management in a small organisation
At this point it should be made clear that these central roles do not necessarily have to be performed by more than one person. Staffing arrangements should reflect the size of the organisation concerned, the existing resources and the aspired-to level of IT security. On the other hand, it should be emphasised that IT security comes at a price. Those in positions of responsibility must have sufficient resources at their disposal so that they can devote sufficient effort to the "IT security" task. This will have more than paid for itself if there are fewer damaging incidents due to lack of security provision.
IT security management tasks, responsibility and authority
The IT Security Officer and the IT Security Management Team must have clearly defined tasks, responsibilities and authorities, which must be laid down by Management. In order to be able to perform their tasks, they should both be involved in all relevant procedures and decisions. The roles should be integrated into the organisational structure in such a way that all those involved can communicate with each other. The roles of IT Security Officer and of being a member of the IT Security Management Team should be entrusted to staff who possess the relevant specialist skills. If necessary, to support these roles tasks can be delegated to the specific IT Security Officers appointed for a given division or department, IT project or IT system.
The IT Security Officer
As the responsibility for IT security is delegated in the same way as the responsibility for task accomplishment, the danger presented by unclear delegation is that IT security is transformed into "someone else's problem". The result is that the responsibility for IT security is shifted around until no one takes responsibility for it any longer. To avoid this happening, responsibility for IT security should be given directly to a specific role, that of the IT Security Officer. This person is responsible for looking after all matters of IT security within the organisation. The tasks of the IT Security Officer are:
In order to carry out these tasks, it is desirable that the IT Security Officer has knowledge and experience in the areas of IT security and IT. As this task requires a variety of skills, the person appointed to this position should possess the following qualifications and attributes:
Working together with IT users requires a high degree of skill as these users must first be convinced of the necessity of IT security, which some of them may perceive as a burden. Equally difficult is questioning IT users about sensitive incidents and weak spots. In order to guarantee success here, the IT users must be convinced that honest answers will not cause them problems.
The IT Security Management Team
The IT Security Management Team supports the IT Security Officer with the performance of his tasks by co-ordinating measures which impact the entire organisation, compiling information and performing supervisory tasks. The precise shape of the team will depend on the size of the organisation concerned, the aspired-to level of IT security and the available resources. In extreme cases the IT Security Management Team may consist of only one person, the IT Security Officer, who in this case is responsible for all the tasks in the IT security process.
Tasks of the IT Security Management Team include:
In order to be able to carry out its tasks effectively, the IT Security Management Team members should have knowledge of IT security, technical knowledge of IT systems and experience in organisation and administration. In addition, the IT Security Management Team should reflect the different operational areas within the organisation. As a minimum, the IT Security Management Team should include an IT Officer, the IT Security Officer and an IT user representative. If a similar body already exists in the organisation, its tasks could be extended accordingly. However, to underline the importance of IT security it is advisable to set up an IT Security Management Team and to place at its disposal the resources it needs.
Only a few organisations, either very large ones or ones with high IT security requirements, will be able to make full-time staff available to the IT Security Management Team. Normally these tasks will have to be performed in addition to the employees' primary duties. An exception to this, however, might be the first occasion that the IT security process is set up. If possible, the members of the IT Security Management Team should be released from most of their other duties during this phase. The decision as to whether staff should be released and to what extent this is appropriate will depend on the distribution of tasks between the IT Security Management Team and the IT Security Officer. The final decision here lies with Management. Whatever arrangements are adopted, the IT Security Management Team should meet regularly to ensure continuous oversight of the IT security process.
Area IT security officer, IT project and IT system security officers
In large organisations it can be necessary to employ separate IT Security Officers in each of the various business units (referred to below as the "Area IT Security Officer"). The Area IT Security Officer is responsible for all security aspects of the IT systems and applications in his area (e.g. department, branch etc.). Depending on the size of the business unit, the task of Area IT Security Officer can be assumed by somebody who is already entrusted with similar tasks, e.g. the person might already perform the role of Divisional IT Officer (if such a position exists). Care should be taken during selection of the Area IT Security Officer to ensure that he is familiar with the tasks, conditions and work processes in the relevant business unit.
The various IT systems and applications within an organisation often have different IT security requirements, which may be compiled in a separate IT system security policy document and require different IT security measures. The analogous situation applies to the IT project Security Officer, with the distinction that his role is IT project-specific instead of IT system-specific.
The tasks of the IT Project, IT System and Area Security Officers include:
Persons in these roles should possess the following qualifications:
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
last update: October 2000 |