

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: Head of IT Section
When creating a virus protection concept, the first essential step is to identify the IT systems at the agency or institution which are potentially under threat from computer viruses. From an overview of all IT systems currently in service or whose use is planned, it is possible to pick out all IT systems for which computer viruses represent a threat or via which computer viruses may be distributed. This overview can also be obtained from the results of the determination of protection requirements in accordance with the IT Baseline Protection Manual, Chapter 2.2.
Systems typically affected by computer viruses are all IT systems with PC-based operating systems such as DOS, Windows 3.x, 95/98 or NT, or those running application programs such as Microsoft Word or Excel, which may be infected by macro viruses.
Although servers are not generally threatened directly by computer viruses themselves, they may be a distribution point for infected programs and files.
The possibility of computer viruses also posing a threat where other operating systems or IT application programs are used cannot be ruled out. In a few individual cases this applies to Unix systems and OS/2 systems, for example, but in view of the lack of widespread use these constitute only a low potential threat (see G 5.23).
For each IT system that is identified in this way, the possible infection paths which computer viruses may take can also be determined in a subsequent step. This information can be used for the later selection of which action to take. An infection by computer viruses may take place in the following ways, for example:
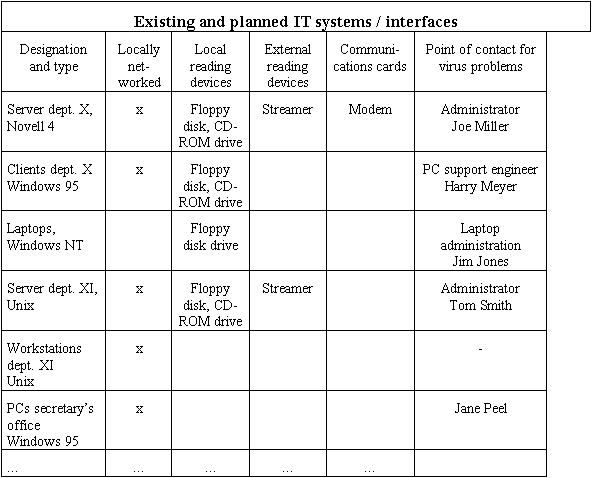
It makes sense to draw up a table showing the interfaces via which a computer virus infection may occur for each identified IT system or, by way of example, for each identified IT system type. These interfaces may be as follows:
The most important aspect of an overview of this nature is the nomination of people to contact for the respective IT systems, who are responsible for implementing the necessary measures and who are the people who users turn to when needed. As the IT landscape in any organisation is subject to constant change, this information must be updated whenever necessary to reflect changes to existing systems.
Example of a survey:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |