

|
|
Initiation responsibility: IT Security Management
Implementation responsibility: Administrators
If navigation under Windows 95 needs to be eased for inexperienced users, or if certain resources need to be restricted for operational reasons, certain restrictions can be provided for the user environment via the system guidelines under Windows 95. However, it must be noted that users might take a cold attitude towards an IT system, if restrictions are not immediately comprehensible. Thus a restriction should only occur when absolutely necessary or if this will go unnoticed by the user.
As soon as system guidelines are activated, Windows 95 will check upon starting whether user-specific restrictions have been set up for the present user. If this is the case, they will be loaded. If it is not the case, restrictions for standard users will be applied. In the following, the principal restrictions that can be set via the system guidelines are described. It is then listed how these restrictions can be established and activated via the system guideline editor (POLEDIT.EXE).
The essential restrictions to be set via system guidelines for a non-networked Windows 95 computer are as follows:
Additionally, the computer can be arranged so that Windows 95 log-on passwords must consist of letters as well as numbers or symbols and must have a minimum length. Programs that should be executed at the system start can also be set.
The following shows in single steps how the system guidelines can be established and activated and which restrictions offer security for a non-networked Windows 95 computer.
1. Establishing a system guideline file
With the help of the system guideline editor a system guideline file can be created. Any name is possible. However, for reasons of simplicity, the name CONFIG.POL will be selected here. The program POLEDIT.EXE should then be started, a new file created and saved under the name CONFIG.POL. This file automatically contains entries for the standard user and the standard computer which, if applicable, must be restricted in the next step. Entries for computer and user must also be established for the administrator ( in the menu point EDIT with ADD USER and ADD COMPUTER). The setting must be specified in the third step.
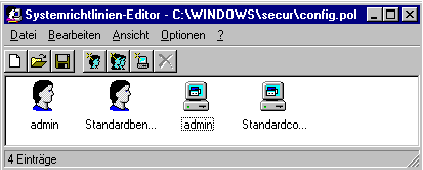
2. Defining a guideline for a standard user and a standard computer
By opening settings for the standard user with the system guideline editor, the appropriate relevant security entries can be made via the menu.
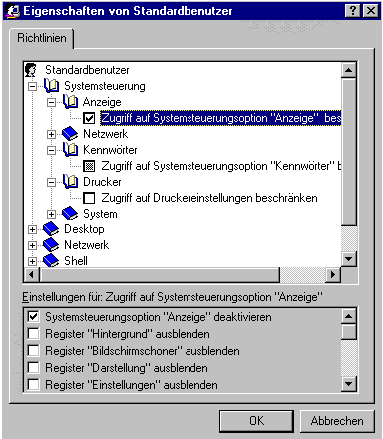
The following restrictions should be set for a Standard user:
CONTROL PANEL
Shell-Access Restrictions
System-access restriction
The following restrictions should be set for a standard computer:
Network
System
3. Defining a guideline for the administrator
None of the restrictions listed above should be implemented for an administrator guideline. For this, an own user must be set up under Windows 95 along with a user and a computer via the system guidelines, otherwise the same restrictions will apply as for a standard user. The password may only be made known to the administrator and his substitute.
In any case, this guideline must be saved in the CONFIG.POL file.
4. Defining guidelines for single users based on a standard user and a standard computer
If users are required whose restrictions should differ from those specified under 1., the guidelines are the same as for 1. but must additionally be set up in the CONFIG.POL file. The standard profile is copied, the name of the user concerned will then be given to the profile and the restrictions are set as described under 1.
5. Activating the guidelines
When the administrator sets up the system guidelines, particular care and attention must be given as inconsistent system conditions can easily be set which hinder work with the computer. The operating system would have to be re-installed. Therefore the system guidelines should only be activated once they have been defined with utmost care.
For this purpose, the administrator must open the local registry with the system guideline editor (POLEDIT.EXE) and the switch REMOTE-UPDATE for the LOCAL COMPUTER under the option NETWORK-UPDATE must be switched on. INTERACTIVE must be selected as update-mode. The path for the CONFIG.POL as described above must also be defined.
Highly experienced administrators can carry out the necessary settings with the registry editor (program REGEDIT.EXE).
Furthermore, the user profiles must be activated under the option PASSWORDS in the program group CONTROL PANEL.
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |