

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: IT Security Management, Administrators
Windows NT can be implemented in various configurations in a network. To allow an appraisal and understanding of the advantages and disadvantages of the individual types of implementation, the security system of Windows NT needs to be described briefly to start with. In principle, this operating system retains control of all resources. Users can only access the resources if they have been granted the corresponding rights and authorisations. Access to the system is only possible via a valid user account, which can be protected by means of a password. The security account manager (SAM) is used to administer information on user and group accounts in the security account database, often termed SAM database. When a user logs in, the operating system generates an access token for the user, in accordance with the entries in the SAM database. The security reference monitor uses this token to check whether the user is authorised to access certain objects and perform the required actions (e.g. delete a file or shutdown the system).
Windows NT supports network operations with the following concepts:
1. Workgroups
Computers can be assigned to workgroups and jointly use resources via the network as part of the peer-to-peer concept (also refer to Module 6.3 Peer-to-Peer Networks).
Every computer in such a network can be used as a server as well as a workstation. This is done by sharing resources on the individual computers. Every Windows NT workstation employed in a workgroup manages its own SAM database and, thus, its own user and group accounts. The entries in this database cannot be used by any other computer in the same workgroup. As a result, central administration is not possible. A password is generally required to access resources which have been shared.
The main disadvantage of this concept is that it does not allow adequate control of the rights of individual users. For this reason, the configuration of workgroups should be avoided wherever possible.
2. Network with a dedicated server
This type of network incorporates a client-server structure. In this case, a specification is made as to which computers should act as servers and clients respectively. Servers can share directories and / or printers, and supply applications such as Mail, Schedule+, Fax on a global basis. In contrast, clients can only use the resources made available by the servers.
An NT computer can be run on the "Windows NT Server" or "Windows NT Workstation" operating system. In small networks, a licensed version of "Windows NT Workstation" can also be operated as a server. Due to licensing regulations, however, no more than 10 users are allowed to simultaneously log into this computer via the network. If this limit proves too low, Windows NT Server needs to be installed. In general, standard users should not be allowed to work on a server running under the Windows NT operating system. The operation of clients under Windows NT is not absolutely necessary.
The main advantage of this concept is central data storage and management. If only one server is employed in a network like this, then only this server is used to configure and hold an account for every user of the network. To be able to use resources and services on this server via the network, a user simply needs to log into the server. The employment of this concept can by all means prove economically feasible in small networks.
However, if the server capacity no longer proves sufficient for fulfilling requirements concerning processing speed and disk space, a great deal of extra management is required when one or more servers are subsequently added to the network. If all users are to receive the right to access all servers via the network, corresponding user accounts must be configured and maintained on each of the servers.
3. Domain concept
Under Windows NT, a domain is a group of computers having access to a common security and user-account database (SAM database). This means that users only need to log into the domain once. After that, they are able to access all resources released for them, irrespective of which server these resources are located on.
One domain server under the Windows NT Server operating system acts as a primary domain controller (PDC). In addition, the domain can contain one or more backup domain controllers (BDC), member servers - i.e. those without a domain control functionality (also refer to the information provided further below) - and Windows NT workstations. The domain can also contain workstations running on other operating systems, such as Windows for Workgroups, Windows 95 and MS-DOS.
A decision as to whether a server is to act as a primary domain controller, backup domain controller or member server should be made before installation, as subsequent changes are only possible if a re-installation is performed. To provide a clearer understanding, the various types of servers which can be found in a domain are described in more detail below:
a) Primary domain controller (PDC)
One server of a Windows NT domain must always be configured as a primary domain controller. Use of the Windows NT Server operating system is absolutely necessary here, as the Workstation version does not provide this functionality. The central user-account database (SAM database) for the domains is managed on the PDC. All changes can only be performed on this database with the help of the user manager for domains. The primary domain controller also processes user logins.
b) Backup domain controller (BDC)
Other servers of the domain can be configured as backup domain controllers. Use of the Windows NT Server operating system is also absolutely necessary here. A read-only copy of the user database of the domain is replicated automatically on every backup domain controller. Synchronisation is performed regularly. Backup domain controllers can also process user logins for the domain. Particularly when a large number of users are involved, this feature can be used to distribute the load generated by the user logins among several servers.
If possible, every domain should have at least one backup domain controller, to ensure that management of the domain continues even after a failure of the primary domain controller. In such cases, it is possible to upgrade the backup domain controller to a primary domain controller. If no backup domain controller has been configured, it is not possible to install a new primary domain controller in a domain.
If the domain servers are distributed among several estates linked together via a WAN, at least one backup domain controller should be installed in each estate.
c) Member server
Member servers are not configured as primary or backup domain controllers. These servers do not have copies of the user-account database of the domain. Consequently, they cannot process user logins for the domain.
The addition of a member server to a domain proves beneficial in the following situations:
One essential aspect of the domain concept is that all user accounts for each domain only need to be defined once. Management is performed in the central user database on the primary domain controller. This means that users only need to authenticate themselves to this database when logging in. After that, they can access all objects and resources which have been shared for them, regardless of which server these objects and resources are located on. If a user needs to work on a computer running under Windows NT Workstation, authenticating against the central user database is sufficient for gaining access to this computer.
Organisation of domains
Although several domains can be configured in a network, each of these domains must have a unique name. Every domain manages its own central SAM database. For this reason, user and group accounts are only valid in the domain in which they were defined.
Within a network however, a requirement might arise for users of one domain to access resources in another domain. This requirement can be fulfilled by the trust relationships between domains.
In this respect, a distinction is made between two types of domain: the trusted domain and the trusting domain. User accounts and global groups of the trusted domain can be assigned rights and authorisations in the trusting domain, thus allowing access to the resources shared in the latter.
The following domain models can be implemented:
a) Single-domain model
This is the simplest domain model, as it only involves the existence of one domain in a network. Consequently, it is not necessary to manage trust relationships. In this case, only one SAM database exists for management purposes in the entire network. One variant of this model consists of a configuration of several individual domains in a network, between which no trust relationships are defined. In this case, each domain manages its own SAM database as well as user and group accounts. The single-domain model is particularly suitable for networks with a low number of users (approx. 200 to 300) and computer nodes. A disadvantage of this model is the decrease in performance which occurs as the number of users and user groups rises. Furthermore, it is not possible to group resources into organisational units, for example, in order to reserve a server for a particular department.
b) Master-domain model
The main characteristic of this model is that it divides a network into several domains, one of which centrally manages all user accounts and group accounts. This domain is termed master domain. The other domains hold the resources. These resource domains trust the domain holding the user accounts. The master-domain model is illustrated in the following diagram:
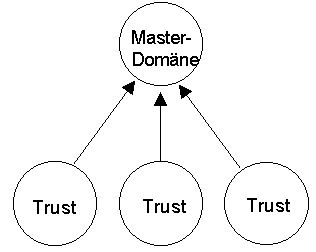
According to Microsoft, this domain model can handle up to 15,000 users. It is particularly suitable for organisations which consist of several departments, each needing to manage its own resources, and in which user administration is performed centrally. This domain model allows a separate person to be appointed for the administration of each of the resource domains, and also permits central security management.
c) Multiple-master domains
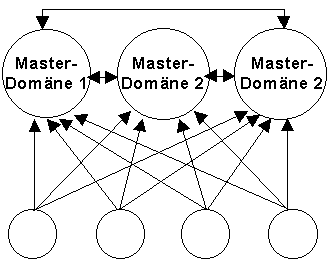
This model consists of several master domains which trust each other. The user and group accounts are managed in these master domains. In addition, there are resource domains which unilaterally trust all master domains. A multiple-master domain is illustrated in the following diagram:
The explicit trust relationship between domain 1 and domain 3 is necessary, as positions of trust are not transitive, i.e. mutual trust between domains 1 and 2, as well as between domains 2 and 3, does not automatically imply mutual trust between domains 1 and 3.
The master domain concepts are often used in networks where more than 15,000 users are present. This concept also allows a network to be partitioned among main departments, and the resources to be managed by these individual departments. For this purpose, a master domain is configured for each main department. The users of a main department are assigned user accounts in the master domain. The resources are managed by the departments in the resource domains. It is also possible to organise a network by location. This involves the configuration of a master domain for each location, and a resource domain for each department. This domain model is scaleable, and no limits are imposed on the size of the organisation. Central security management is possible here, and global groups and user accounts only need to be configured once throughout the organisation.
Finally, it must be noted that this module requires a high degree of administrative discipline and careful planning. Particular care must be exercised when defining the trust relationships. In addition, it is absolutely necessary to prevent a configuration of user accounts in the resource domains.
d) Complete-trust model
This model involves relationships of mutual trust between all the domains of a network. Resources as well as user and group accounts are managed in each domain. A complete-trust model is shown in the following diagram:
This model allows the departments of an organisation to manage user
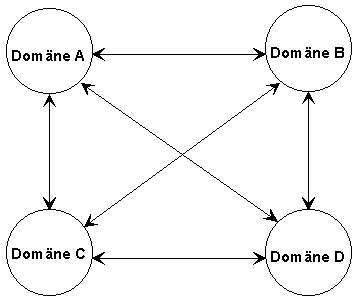
accounts as well as resources. No central department is required for management. This model can be scaled to any required number of users. However, it also has major disadvantages. For example, it is hard to check compliance with the applicable security policy. This makes it difficult not only to set up a central security management, but also to co-ordinate the activities of the individual administrators. Many trust relationships need to be managed in a network containing a large number of domains, so that a clear overview is ultimately lost.
No general recommendations can be made as to which of the domain models described should be used in an organisation. This can only be ascertained individually, on the basis of the physical and logical network structure, as well as the distribution of data, applications and users in the network. For this reason, a determination of the ideal domain structure requires a detailed analysis, which can prove quite elaborate for extensive networks and might need to be supported with planning software.
Additional controls:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |